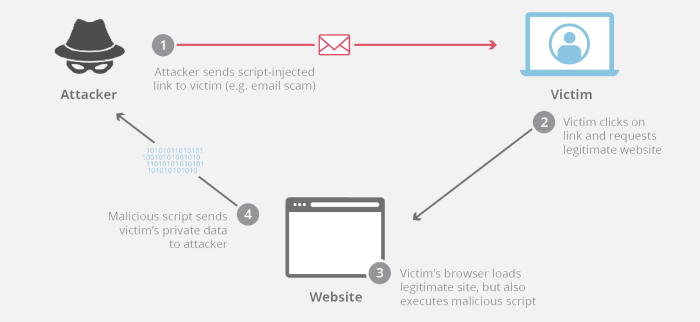
The digital landscape is constantly evolving, and with it, the threats that can compromise our online experiences. Among these threats, cross-site scripting (XSS) attacks stand out as a persistent and potentially devastating vulnerability. These attacks allow malicious actors to inject client-side scripts into web pages viewed by other users, essentially turning your website against its visitors. Understanding and mitigating XSS attacks is, therefore, crucial for any web developer or security-conscious individual.
This guide provides a detailed exploration of how to prevent cross-site scripting (XSS) attacks. We’ll delve into the core concepts, examine different attack vectors, and explore various preventative measures. From input validation and output encoding to content security policies and regular security audits, we’ll equip you with the knowledge and tools necessary to build and maintain secure web applications.
Understanding Cross-Site Scripting (XSS) Attacks
Cross-Site Scripting (XSS) attacks are a type of web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. These attacks exploit the trust users have in a website, tricking their browsers into executing attacker-supplied code. Successful XSS attacks can have serious consequences, potentially compromising user data and website integrity.
Fundamental Concept of XSS Attacks
XSS attacks exploit vulnerabilities in how a web application handles user input and displays it in a web browser. If a web application doesn’t properly sanitize or encode user-supplied data before including it in the output, an attacker can inject malicious JavaScript code. This code then executes in the victim’s browser when they view the compromised page. The browser, believing the code is part of the trusted website, executes the script, allowing the attacker to perform actions on behalf of the user.
The core principle involves manipulating how a website processes and renders user-provided data, turning a legitimate website into a vehicle for malicious code execution.
Types of XSS Attacks
There are several types of XSS attacks, each with its own characteristics and attack vectors. Understanding these different types is crucial for effectively mitigating XSS vulnerabilities.
- Reflected XSS: This type of attack involves injecting malicious scripts into a website’s URL or other user input that is then reflected back to the user by the web server. The attacker typically crafts a malicious link and tricks the victim into clicking it. When the victim clicks the link, the injected script executes in their browser. For example, an attacker might craft a URL that includes a malicious script in a search query parameter.
When the victim searches for that term, the script is displayed on the search results page and executed.
- Stored XSS (Persistent XSS): In stored XSS attacks, the malicious script is permanently stored on the target server, such as in a database or comment section. When a user visits a page containing the injected script, the script executes. This type of attack is particularly dangerous because it affects all users who visit the compromised page. For example, an attacker might inject a script into a blog comment.
Every time someone views that blog post, the script executes in their browser.
- DOM-based XSS: This type of attack occurs when the vulnerability is in the client-side JavaScript code rather than the server-side code. The attacker manipulates the Document Object Model (DOM) of the page, causing the browser to execute malicious code. The vulnerability often arises from using JavaScript functions that dynamically generate HTML content based on user input without proper sanitization. For example, if a JavaScript function uses `document.write()` to display user input directly on the page, and the input isn’t sanitized, an attacker could inject a script.
Potential Impact of Successful XSS Attacks
Successful XSS attacks can lead to a variety of malicious outcomes, impacting both the user and the website. The severity of the impact depends on the nature of the injected script and the permissions of the user’s browser.
- Data Theft: Attackers can steal sensitive user data, such as cookies, session tokens, and personal information. This allows them to impersonate the user and access their accounts.
- Account Hijacking: By stealing session cookies or other authentication information, attackers can gain complete control of a user’s account.
- Website Defacement: Attackers can inject scripts to alter the content of the website, displaying false information or redirecting users to malicious sites.
- Malware Installation: XSS attacks can be used to redirect users to websites that distribute malware or exploit other vulnerabilities in the user’s browser or system.
- Phishing Attacks: Attackers can use XSS to create fake login forms or other phishing attempts to steal user credentials.
Input Validation and Sanitization

Input validation and sanitization are crucial defenses against Cross-Site Scripting (XSS) attacks. These techniques ensure that any data received from users, such as text entered in a form or data passed in a URL, is safe to use in your web application. Properly implementing these practices significantly reduces the risk of malicious scripts being injected and executed in users’ browsers, thereby protecting both your users and your application.
Importance of Input Validation in Preventing XSS Attacks
Input validation is essential because it acts as the first line of defense against XSS. By verifying the format, type, length, and content of user-supplied data before it is processed, you can prevent malicious code from entering your application. This proactive approach helps to mitigate the risk of attackers injecting harmful scripts that could steal user credentials, redirect users to phishing sites, or deface your website.
Without robust input validation, your application becomes vulnerable to a wide range of XSS attacks.
Common Input Validation Techniques
Various input validation techniques can be employed to secure your web applications. These methods work by examining user input and rejecting or modifying it if it doesn’t meet predefined criteria. Here are some common techniques:
- Whitelist Validation: This technique involves defining a list of acceptable characters or patterns. Any input that doesn’t match the whitelist is rejected. This is generally considered the most secure approach because it explicitly defines what is allowed, minimizing the risk of unexpected vulnerabilities.
- Blacklist Validation: This approach defines a list of prohibited characters or patterns. Any input containing these blacklisted elements is rejected. While seemingly straightforward, blacklist validation is often less effective than whitelisting because it’s challenging to anticipate all possible attack vectors, and new exploits can bypass the blacklist.
- Type Validation: This ensures that the input data is of the expected type (e.g., integer, string, boolean). For instance, if a field is intended to receive a numerical value, the validation process will check if the input consists of digits only.
- Length Validation: This technique checks the length of the input to ensure it falls within acceptable bounds. This helps prevent buffer overflows and other attacks that exploit excessive input lengths.
- Format Validation: This method verifies that the input conforms to a specific format, such as an email address, a date, or a phone number. Regular expressions are commonly used for format validation. For example, a regular expression can be used to validate that an email address follows the standard “[email protected]” format.
- Contextual Encoding: This technique encodes the data based on where it will be used (e.g., HTML, JavaScript, CSS, URL). Encoding transforms special characters into their safe equivalents. For instance, in HTML, the character ” <" is encoded as "<".
Example: Sanitizing User Input to Prevent XSS
Here’s a simple example, using JavaScript, demonstrating how to sanitize user input to prevent XSS. This example focuses on escaping HTML entities to prevent script injection. The provided code sanitizes user input by replacing potentially harmful characters with their HTML entity equivalents.
Scenario: A user submits a comment on a website. Without sanitization, a malicious user could inject JavaScript code within the comment, which would then execute when other users view the comment.
Code Example (JavaScript):
function sanitizeInput(input) let sanitized = input.replace(/&/g, "&"); sanitized = sanitized.replace(/ /g, ">"); sanitized = sanitized.replace(/"/g, """); sanitized = sanitized.replace(/'/g, "'"); return sanitized;// Example usage:let userInput = " This is a test.";let sanitizedInput = sanitizeInput(userInput);console.log("Original Input: " + userInput);console.log("Sanitized Input: " + sanitizedInput); Explanation:
- The
sanitizeInputfunction takes a string as input. - Inside the function, the
replace()method is used with regular expressions to find and replace specific characters:&: Replaces ampersands (&) with their HTML entity (&).<: Replaces less-than signs (<) with their HTML entity (<).>: Replaces greater-than signs (>) with their HTML entity (>).": Replaces double quotes (“) with their HTML entity (").': Replaces single quotes (‘) with their HTML entity (').
- The function returns the sanitized string.
- In the example usage, a string containing a malicious script is passed to the
sanitizeInputfunction. - The output shows the original input and the sanitized input, where the script tags have been converted into their HTML entity equivalents, thus preventing the script from executing.
Output Encoding
Output encoding is a crucial defense mechanism against Cross-Site Scripting (XSS) attacks. It involves transforming data before it’s displayed on a webpage to neutralize any malicious code that might be embedded within it. By properly encoding output, developers can ensure that user-supplied data is treated as plain text and not executed as active code within the browser.
Role of Output Encoding in Mitigating XSS Vulnerabilities
Output encoding is fundamental to preventing XSS attacks because it alters the way a web browser interprets data. When user-supplied data is not properly encoded, an attacker can inject malicious scripts (e.g., JavaScript) into a website. These scripts can then execute within the context of the user’s browser, potentially stealing sensitive information, redirecting users to malicious sites, or defacing the website.
Output encoding prevents this by converting special characters in the data into their corresponding HTML entities, JavaScript escape sequences, or URL-encoded representations, depending on the context. This conversion ensures that the browser interprets the data as data and not as executable code. For example, the character ” <" might be converted to "<", which the browser will display as "<" rather than interpreting it as the start of an HTML tag. This process effectively neutralizes the malicious code, making it harmless.
Comparison of Different Output Encoding Methods
Different output encoding methods are designed to address XSS vulnerabilities in different contexts.
The appropriate encoding method depends on where the data is being used within the HTML document.
- HTML Encoding: HTML encoding converts characters that have special meanings in HTML (e.g., ” <", ">“, “&”, “””) into their respective HTML entities (e.g., “<“, “>”, “&”, “"”). This is used when displaying data within the HTML body, attributes, or within HTML tags. For example, if a user enters the string “<script>alert(‘XSS’)</script>” in a comment form, HTML encoding would convert it to “<script>alert(‘XSS’)</script>”, which the browser will display as text instead of executing it as a script.
- JavaScript Encoding: JavaScript encoding is used when data is inserted into JavaScript code. It involves escaping special characters within the data with backslashes. This prevents the data from breaking the JavaScript code and ensures that it is treated as a string literal. For instance, if a user-supplied string contains a quote character (“), JavaScript encoding would convert it to “\””, preventing a JavaScript syntax error and preventing potential code injection.
- URL Encoding: URL encoding, also known as percent-encoding, is used when data is inserted into a URL. It converts special characters into a “%” followed by their hexadecimal representation. This ensures that the data is correctly interpreted as part of the URL. For example, spaces are converted to “%20”. This prevents the data from being misinterpreted by the server or browser.
Demonstration of HTML Encoding to Prevent XSS
HTML encoding is a fundamental defense against XSS attacks, especially when displaying user-supplied data within the HTML body or attributes. Consider a simple example where a user submits a comment to a website. Without proper encoding, an attacker could inject malicious JavaScript code into the comment, which would then be executed when the comment is displayed.
Before HTML Encoding (Vulnerable Code):
Suppose the website code looks like this (simplified PHP example):
“`php Your comment: ” .
$comment . ”
“;?>“`
In this vulnerable code, if a user enters the following comment:
“`html “`
The browser will execute the JavaScript code, displaying an alert box. This demonstrates a successful XSS attack.
After HTML Encoding (Secure Code):
By using HTML encoding, the website can prevent this attack. Here’s the modified code (using the `htmlspecialchars()` function in PHP):
“`php Your comment: ” . $encoded_comment .
”
“;?>“`
In this secure code, the `htmlspecialchars()` function converts special characters into their HTML entities. If the user enters the same malicious comment:
“`html “`
The `htmlspecialchars()` function converts the comment to:
“`html<script>alert('XSS');</script>“`
The browser will display this as plain text, and the JavaScript code will not be executed, thus preventing the XSS attack. The `ENT_QUOTES` flag in `htmlspecialchars()` ensures that both single and double quotes are also encoded, and `UTF-8` specifies the character encoding.
This demonstrates how HTML encoding effectively mitigates XSS vulnerabilities by treating potentially dangerous user input as plain text.
Content Security Policy (CSP)
Content Security Policy (CSP) is a crucial security measure designed to mitigate XSS attacks by controlling the resources a web page is allowed to load. It functions as an added layer of defense, complementing input validation, output encoding, and other security practices. By defining a whitelist of trusted sources for content, CSP significantly reduces the attack surface for malicious scripts.
Content Security Policy (CSP) and XSS Prevention
CSP plays a vital role in XSS prevention by explicitly declaring the sources from which the browser should load resources, such as JavaScript, CSS, images, and fonts. This declaration prevents the browser from executing or loading resources from unauthorized origins, effectively blocking malicious scripts injected through XSS vulnerabilities. Even if an attacker manages to inject a script into the page, CSP can prevent its execution if the source is not explicitly allowed.
Basic CSP Configuration Example
A basic CSP configuration is implemented using the `Content-Security-Policy` HTTP response header. This header contains directives that instruct the browser on how to handle different types of content.“`Content-Security-Policy: default-src ‘self’; script-src ‘self’ https://example.com; style-src ‘self’ https://fonts.googleapis.com; img-src ‘self’ data:;“`Let’s break down this example:* `default-src ‘self’;`: This directive sets the default source for loading content. `’self’` indicates that content can be loaded only from the same origin (domain, protocol, and port) as the website.
`script-src ‘self’ https
//example.com;`: This directive specifies the allowed sources for JavaScript files. In this case, scripts can be loaded from the same origin (`’self’`) and from `https://example.com`.
`style-src ‘self’ https
//fonts.googleapis.com;`: This directive defines the allowed sources for CSS stylesheets. Here, stylesheets can be loaded from the same origin (`’self’`) and from `https://fonts.googleapis.com` (e.g., for using Google Fonts).
`img-src ‘self’ data
;`: This directive specifies the allowed sources for images. `’self’` allows images from the same origin, and `data:` allows inline images using data URIs.
Common CSP Directives
CSP offers a variety of directives to control different types of resources. Understanding these directives is essential for configuring an effective CSP. The following table summarizes some of the most common directives and their functions.
| Directive | Function | Example | Explanation |
|---|---|---|---|
| `default-src` | Defines the default source for all content not explicitly specified by other directives. | `default-src ‘self’;` | Allows loading content only from the same origin. If a more specific directive is not set, this directive controls the behavior. |
| `script-src` | Specifies the allowed sources for JavaScript files. | `script-src ‘self’ https://example.com;` | Allows JavaScript files to be loaded from the same origin and from `https://example.com`. |
| `style-src` | Specifies the allowed sources for CSS stylesheets. | `style-src ‘self’ https://fonts.googleapis.com;` | Allows CSS stylesheets to be loaded from the same origin and from `https://fonts.googleapis.com`. |
| `img-src` | Specifies the allowed sources for images. | `img-src ‘self’ data:;` | Allows images to be loaded from the same origin and from data URIs (e.g., inline images). |
| `font-src` | Specifies the allowed sources for fonts. | `font-src ‘self’ https://fonts.gstatic.com;` | Allows fonts to be loaded from the same origin and from `https://fonts.gstatic.com` (e.g., for Google Fonts). |
| `connect-src` | Restricts the origins to which the page can connect (e.g., via XMLHttpRequest, WebSocket). | `connect-src ‘self’ https://api.example.com;` | Allows connections only to the same origin and to `https://api.example.com`. |
| `media-src` | Specifies the allowed sources for media files (e.g., audio, video). | `media-src ‘self’;` | Allows media files to be loaded from the same origin. |
| `object-src` | Specifies the allowed sources for plugins, such as ` | `object-src ‘none’;` | Disables plugins by default. |
| `frame-src` | Specifies the allowed sources for frames and iframes. | `frame-src ‘self’;` | Allows frames and iframes to be loaded from the same origin. |
| `form-action` | Specifies the valid targets for form submissions. | `form-action ‘self’;` | Allows form submissions only to the same origin. |
HTTP Headers and Security Best Practices
HTTP headers play a crucial role in bolstering the security of web applications, particularly in mitigating the risks associated with XSS attacks. By implementing specific headers, developers can instruct browsers to behave in a more secure manner, reducing the likelihood of successful XSS exploits. This section explores essential HTTP headers for XSS protection and provides practical guidance on their implementation.
Essential HTTP Headers for XSS Protection
Several HTTP headers are designed to enhance XSS protection. Properly configuring these headers is a proactive measure in securing web applications against cross-site scripting vulnerabilities.
- Content-Security-Policy (CSP): This header is a powerful tool that allows web developers to control the resources a browser is allowed to load for a given page. By defining a whitelist of trusted sources for scripts, stylesheets, images, and other resources, CSP significantly reduces the attack surface for XSS. For example, a CSP header might specify that scripts can only be loaded from the same origin as the website.
- X-XSS-Protection: This header, primarily supported by older browsers, enables the built-in XSS filter in the browser. When enabled, the browser attempts to detect and block reflected XSS attacks. While less effective than CSP, it provides an additional layer of defense, particularly for legacy browsers. The header can be set to ‘1’ to enable the filter and ‘0’ to disable it.
Setting it to ‘mode=block’ instructs the browser to block the entire page if an XSS attack is detected.
- X-Frame-Options: Although not directly related to XSS, this header helps prevent clickjacking attacks, which can be used in conjunction with XSS. By specifying whether a page can be framed by other websites, the X-Frame-Options header protects against malicious websites embedding your content and tricking users into performing actions. The header can be set to ‘DENY’, ‘SAMEORIGIN’, or ‘ALLOW-FROM uri’.
- Strict-Transport-Security (HSTS): Although not directly preventing XSS, HSTS enforces the use of HTTPS, preventing attackers from intercepting and injecting malicious scripts into HTTP traffic. This header ensures that the browser always connects to the website over a secure connection.
Implementing HTTP Headers in Web Server Configuration
Implementing these headers involves configuring your web server to include them in the HTTP response. The method of configuration varies depending on the web server software used.
- Apache: In Apache, you can add headers to your configuration files (.htaccess or httpd.conf) using the `Header` directive. For example, to set the X-XSS-Protection header:
Header set X-XSS-Protection "1; mode=block"To set the Content-Security-Policy header:
Header set Content-Security-Policy "default-src 'self'; script-src 'self' https://trusted-cdn.com; style-src 'self' https://trusted-cdn.com" - Nginx: In Nginx, you can use the `add_header` directive within the `server` or `location` blocks of your configuration files. For example:
add_header X-XSS-Protection "1; mode=block";add_header Content-Security-Policy "default-src 'self'; script-src 'self' https://trusted-cdn.com; style-src 'self' https://trusted-cdn.com"; - IIS (Internet Information Services): In IIS, you can configure headers through the IIS Manager. Select your website, then go to HTTP Response Headers and add the headers.
- Cloud Platforms (AWS, Google Cloud, Azure): Cloud platforms typically provide tools to configure HTTP headers, often through their load balancer or content delivery network (CDN) services. Consult the platform’s documentation for specific instructions.
The Significance of Regular Updates for Security
Regularly updating web application frameworks and libraries is critical for maintaining robust security against XSS and other vulnerabilities. Security updates often include patches for known vulnerabilities, which are actively exploited by attackers.
- Security Patches: Software vendors regularly release updates to address security flaws. These updates often include patches that fix vulnerabilities like XSS, SQL injection, and cross-site request forgery (CSRF).
- Vulnerability Databases: Websites like the National Vulnerability Database (NVD) and Common Vulnerabilities and Exposures (CVE) provide information about known vulnerabilities. Staying informed about these databases helps in prioritizing updates.
- Dependency Management: Using a package manager like npm (Node.js), pip (Python), or Maven (Java) can simplify the process of managing dependencies and updating them to the latest versions. Automated dependency scanning tools can also identify vulnerable libraries.
- Real-World Examples: The Equifax data breach in 2017 was partially attributed to the failure to patch a known vulnerability in the Apache Struts framework. This highlights the severe consequences of neglecting security updates. In another case, a vulnerability in a popular JavaScript library allowed attackers to inject malicious scripts into websites using the library. These examples demonstrate the importance of timely updates.
Frameworks and Libraries for Security
Web frameworks and libraries play a crucial role in mitigating XSS vulnerabilities. They often provide built-in mechanisms and utilities designed to protect against these attacks, simplifying the development process and reducing the risk of security flaws. Leveraging these tools is a cornerstone of secure web application development.
Built-in XSS Protections in Web Frameworks
Popular web frameworks incorporate several strategies to safeguard against XSS attacks. These features are typically designed to be easy to implement, making it straightforward for developers to build secure applications.
- Automatic Output Encoding: Many frameworks automatically encode data before rendering it in the browser. This prevents malicious scripts from being interpreted as HTML or JavaScript. For instance, when a user submits data that includes HTML tags, the framework converts these tags into their encoded equivalents (e.g., `<` for ` <` and `>` for `>`), effectively neutralizing the potential for script injection.
- Context-Aware Escaping: Frameworks often understand the context in which data is being rendered (e.g., HTML attributes, JavaScript code, or CSS). This allows them to apply the appropriate escaping techniques based on the context, preventing vulnerabilities that might arise from using a generic escaping method.
- Templating Engines: Templating engines, common in web frameworks, frequently offer built-in escaping mechanisms. They automatically escape variables within templates, ensuring that user-provided data is rendered safely.
- Input Validation and Sanitization Helpers: Some frameworks include utilities for validating and sanitizing user input. While not a primary defense against XSS, these features can help reduce the attack surface by ensuring that only valid data is processed.
- Content Security Policy (CSP) Integration: Frameworks can facilitate the implementation of CSP by providing mechanisms to easily set and manage HTTP response headers. This allows developers to define which resources the browser is allowed to load, further reducing the risk of XSS attacks.
Using Built-in Security Features: Examples
Here are examples illustrating how to use built-in security features in different frameworks:
- Example: Django (Python)
Django’s templating engine, Jinja2, automatically escapes variables by default. For example, if a user’s input is stored in a variable called `user_input`, and you render it in a template like this: ` user_input `, Django will automatically escape the HTML characters, preventing XSS.
If you need to explicitly mark content as safe (e.g., when rendering trusted HTML), you can use the `safe` filter. However, use this with extreme caution, as it bypasses the default escaping mechanism.
user_input|safe - Example: React (JavaScript)
React escapes values by default when rendering them using JSX. This means that if you include user-provided data in your JSX, React will automatically escape it, preventing XSS vulnerabilities. For example:
<div>userInput</div>If you need to render raw HTML, you can use the `dangerouslySetInnerHTML` prop. However, this is considered unsafe unless you are absolutely certain about the source and validity of the HTML. Use this feature with extreme caution.
<div dangerouslySetInnerHTML=__html: userInput></div> - Example: Ruby on Rails (Ruby)
Rails automatically escapes output in its view templates. For instance, when using ERB templates, variables are escaped by default. For example:
<%= user_input %>If you need to render raw HTML, you can use the `raw` helper. However, this should be used carefully, as it bypasses the default escaping.
<%= raw user_input %>
Comparison of XSS Protection Capabilities
The following table compares the XSS protection capabilities of several popular frameworks and libraries. This comparison highlights the core features each framework offers, aiding in the selection of appropriate tools for a project.
| Framework/Library | Automatic Output Encoding | Context-Aware Escaping | Templating Engine | Input Validation/Sanitization | CSP Integration |
|---|---|---|---|---|---|
| Django (Python) | Yes (Jinja2) | Yes | Jinja2 | Helpers available | Facilitated |
| React (JavaScript) | Yes (JSX) | Yes | JSX | Libraries available | Facilitated |
| Ruby on Rails (Ruby) | Yes (ERB) | Yes | ERB | Helpers available | Facilitated |
| Angular (JavaScript) | Yes | Yes | Angular Templates | Built-in validators | Facilitated |
| Vue.js (JavaScript) | Yes | Yes | Vue Templates | Libraries available | Facilitated |
Regular Expressions and XSS Prevention
Regular expressions (regex) can be a valuable tool in the fight against Cross-Site Scripting (XSS) attacks. They offer a way to examine user input for potentially malicious patterns before the data is processed or displayed. However, it’s crucial to understand both their strengths and limitations within the context of a comprehensive security strategy. Regex alone is rarely sufficient for complete XSS protection.
Input Validation Using Regular Expressions
Input validation is the process of verifying that user-provided data conforms to expected formats and constraints. Regular expressions are particularly useful for this because they allow you to define patterns that the input must match (or not match). This can help to identify and reject malicious payloads, such as JavaScript code embedded within HTML tags.For example, a website might use a regular expression to validate a username, ensuring it only contains alphanumeric characters and underscores.
Another example might involve filtering out potentially harmful characters in a comment section.Here are some examples of regular expressions and their use:
- Filtering HTML Tags: A regex can be used to strip out HTML tags from user input. For example, the following regex in JavaScript:
/<[^>]*>/g. This pattern looks for any character sequence starting with a ‘ <' and ending with a '>‘. The ‘g’ flag indicates a global search, replacing all matches. This is useful for removing potentially dangerous HTML elements. - Blocking JavaScript Events: To prevent the execution of JavaScript code via event handlers, you could use a regex to identify and remove attributes like
onload,onerror, oronclick. A pattern like/(on\w+\s*=\s*["'][^"']*["'])/gicould be used to find and remove these event handler attributes. This is case-insensitive (iflag) and searches globally (gflag). - Validating URLs: Regular expressions can also be used to validate URLs. For instance, a regex can check if a URL is properly formatted. The following is a simplified example:
/^(https?:\/\/)?([\da-z\.-]+)\.([a-z\.]2,6)([\/\w \.-]*)*\/?$/. This pattern validates that the URL starts with “http://” or “https://”, followed by a domain name and a path.
Limitations of Regular Expressions for XSS Prevention
While regular expressions are a useful component of XSS prevention, they are not a silver bullet. Relying solely on regex for XSS protection can lead to significant vulnerabilities. Here’s why:
- Complexity and Maintenance: Creating and maintaining complex regular expressions to cover all potential XSS attack vectors can be difficult. Regex patterns can become long and challenging to read, understand, and update. They are also prone to errors, and even a small mistake can leave vulnerabilities open.
- Evasion Techniques: Attackers are constantly evolving their techniques. They can use various encoding methods (e.g., URL encoding, HTML entities, Unicode) to bypass regex filters. For example, an attacker might encode a JavaScript payload using HTML entities to bypass a filter that looks for the literal ”
- Context Dependence: The effectiveness of a regex depends heavily on the context in which it is used. A regex that works well in one context (e.g., filtering comments) might be ineffective in another (e.g., validating data in a database).
- False Positives and Negatives: Regex can sometimes generate false positives (incorrectly flagging legitimate input as malicious) or false negatives (allowing malicious input to pass through). This can lead to usability issues or security vulnerabilities.
- Lack of Comprehensive Protection: Regex primarily focuses on pattern matching. It doesn't provide protection against all types of XSS attacks, such as those that exploit the application's logic or data flow.
Therefore, using regular expressions should be combined with other security measures, such as output encoding, Content Security Policy (CSP), and a robust security framework. It is also recommended to regularly update and test regex patterns to stay ahead of evolving attack techniques.
Security Auditing and Penetration Testing
Regular security audits and penetration testing are crucial for identifying and mitigating XSS vulnerabilities in web applications. These proactive measures provide a comprehensive assessment of a system's security posture, helping to uncover weaknesses that could be exploited by attackers. They also ensure that implemented security controls are effective and up-to-date.
Security Auditing and XSS Vulnerability Identification
Security auditing involves a systematic review of a web application's code, configuration, and security controls to identify potential vulnerabilities. This process often includes both manual code review and automated scanning tools. The primary goal is to uncover flaws that could be exploited for malicious purposes, including XSS attacks.
- Code Review: Manual code review is a fundamental aspect of security auditing. Auditors examine the application's source code to identify potential XSS vulnerabilities. This includes scrutinizing how user inputs are handled, validated, and displayed. Reviewers look for instances where unsanitized user-supplied data is directly embedded into the HTML output. For example, an auditor might analyze code snippets responsible for generating dynamic content, such as comments sections or search results, to ensure that all user-provided data is properly escaped or encoded.
- Configuration Review: Audits also encompass a review of the application's configuration files and server settings. This includes examining HTTP headers, Content Security Policy (CSP) implementations, and other security-related configurations. Misconfigurations can inadvertently introduce XSS vulnerabilities or weaken existing security measures. For instance, a misconfigured CSP might allow the execution of malicious scripts, even if input validation is robust.
- Automated Scanning: Automated security scanners are used to identify potential vulnerabilities by analyzing the application's behavior. These tools typically simulate various attack scenarios, including XSS attacks, and report any detected weaknesses. These scanners can detect common XSS vulnerabilities, such as reflected XSS and stored XSS, by injecting malicious payloads into input fields and observing the application's response. Tools like OWASP ZAP and Burp Suite are frequently employed for this purpose.
- Vulnerability Assessment Reports: The outcome of a security audit is usually documented in a detailed vulnerability assessment report. This report identifies all discovered vulnerabilities, including XSS flaws, along with their severity levels, and recommended remediation steps. The report serves as a roadmap for developers to address the identified issues and improve the application's security posture.
Penetration Testing for XSS Vulnerabilities
Penetration testing, also known as "pen testing," is a simulated attack on a web application to identify vulnerabilities that an attacker could exploit. Unlike security auditing, which can involve a broad review, penetration testing focuses on actively exploiting identified vulnerabilities to assess their real-world impact. This includes assessing the feasibility of XSS attacks and evaluating the effectiveness of existing security controls.
- Planning and Scoping: The first step involves defining the scope and objectives of the penetration test. This includes determining the target web application, the types of attacks to be simulated, and the specific goals of the test. The scope should be clearly defined to avoid unintended consequences and ensure that the test remains within legal and ethical boundaries.
- Information Gathering: Penetration testers gather information about the target application, including its technologies, functionalities, and known vulnerabilities. This phase might involve using reconnaissance techniques such as web scraping, DNS lookups, and examining HTTP headers. Understanding the application's architecture and components helps testers identify potential attack vectors.
- Vulnerability Analysis: Testers analyze the gathered information to identify potential XSS vulnerabilities. This includes examining the application's input fields, output rendering mechanisms, and any existing security controls. The testers use various techniques to discover potential weaknesses, such as manually reviewing the application's source code and using automated scanning tools.
- Exploitation: In this phase, testers attempt to exploit identified vulnerabilities. For XSS attacks, this might involve injecting malicious JavaScript payloads into input fields and observing how the application handles the injected code. The goal is to verify the exploitability of the vulnerability and assess its potential impact. Testers may use different XSS attack vectors, such as reflected XSS, stored XSS, and DOM-based XSS.
- Post-Exploitation: After successfully exploiting a vulnerability, testers might attempt to gain further access or escalate their privileges within the application. This could involve stealing user credentials, defacing web pages, or gaining control over the server. The post-exploitation phase helps assess the overall impact of the vulnerability and the effectiveness of the application's security controls.
- Reporting: The final step is to document the findings in a comprehensive report. The report includes a detailed description of the identified vulnerabilities, the steps taken to exploit them, the potential impact of the attacks, and recommendations for remediation. The report is shared with the application developers to enable them to address the identified vulnerabilities.
XSS Risk Review Checklist for Security Professionals
A checklist helps security professionals systematically assess web applications for XSS risks. This checklist can be used during code reviews, penetration tests, and security audits. Using a checklist ensures a consistent and thorough assessment.
- Input Validation:
- Verify that all user inputs are validated on both the client-side and server-side.
- Ensure that input validation is performed before any data is used or stored.
- Check for proper validation of data types, lengths, and formats.
- Review the use of allowlists and denylists to restrict input to acceptable values.
- Output Encoding:
- Confirm that all output data is properly encoded based on the context where it is used (HTML, JavaScript, URL, etc.).
- Verify the use of appropriate encoding functions or libraries to prevent XSS attacks.
- Check for consistent encoding across all parts of the application.
- Content Security Policy (CSP):
- Ensure that a strong and well-configured CSP is implemented to restrict the sources from which the browser can load resources.
- Verify that the CSP includes directives to prevent inline scripts and evaluate code.
- Review the CSP configuration for any weaknesses or bypasses.
- HTTP Headers:
- Verify that relevant HTTP headers, such as `X-XSS-Protection` and `X-Content-Type-Options`, are set appropriately.
- Check that the `X-XSS-Protection` header is enabled and configured to block potential XSS attacks.
- Ensure the `X-Content-Type-Options` header is set to `nosniff` to prevent MIME-sniffing attacks.
- Frameworks and Libraries:
- Check for the use of secure frameworks and libraries that provide built-in XSS protection.
- Verify that these frameworks and libraries are up-to-date and properly configured.
- Review the application's use of third-party libraries for any known XSS vulnerabilities.
- Regular Expressions:
- Examine the use of regular expressions for input validation and data sanitization.
- Verify that regular expressions are correctly constructed and do not allow for bypasses or vulnerabilities.
- Check for the use of overly complex or inefficient regular expressions that could introduce performance issues.
- Security Auditing and Penetration Testing:
- Ensure that regular security audits and penetration tests are conducted to identify and address XSS vulnerabilities.
- Verify that the testing scope includes a thorough assessment of XSS risks.
- Review the results of previous audits and penetration tests to ensure that identified vulnerabilities have been addressed.
- Developer Training:
- Provide training to developers on secure coding practices and XSS prevention techniques.
- Educate developers about the importance of input validation, output encoding, and CSP.
- Ensure that developers are aware of the latest XSS attack vectors and mitigation strategies.
Protecting Against DOM-based XSS
DOM-based Cross-Site Scripting (XSS) attacks are a sophisticated type of XSS vulnerability that targets the Document Object Model (DOM) of a web page. Unlike reflected or stored XSS, DOM-based XSS vulnerabilities arise when JavaScript code dynamically modifies the DOM based on user-controllable data. This makes them particularly challenging to identify and mitigate because the vulnerability exists within the client-side JavaScript code rather than the server-side code.
Challenges Posed by DOM-based XSS Attacks
DOM-based XSS attacks present unique challenges due to their nature. They operate within the browser's environment, making them harder to detect during server-side input validation. The vulnerabilities are often subtle, residing in JavaScript code that processes data before it's displayed. This requires careful examination of client-side code. Moreover, the attack payload is not necessarily sent to the server; it's injected directly into the DOM, bypassing traditional security measures.
This characteristic increases the difficulty in detecting and preventing such attacks.
Common Sources of DOM-based XSS Vulnerabilities
Several common sources contribute to DOM-based XSS vulnerabilities. These sources involve JavaScript code that interacts with user input and manipulates the DOM.
- `document.write()` and `document.writeln()`: These methods are frequently used to write content directly to the DOM. If user-supplied data is passed to these methods without proper sanitization or encoding, it can lead to XSS.
- `innerHTML`: The `innerHTML` property allows JavaScript to modify the HTML content of an element. Using `innerHTML` with unsanitized user input can inject malicious scripts.
- `eval()` and `setTimeout()`/`setInterval()` with string arguments: These functions execute JavaScript code dynamically. If user-supplied data is passed as a string argument to these functions, attackers can inject and execute arbitrary code.
- URL parameters and the `location` object: Reading data from the URL (e.g., query parameters, fragments) and using it to modify the DOM without proper validation can create vulnerabilities.
- `setAttribute()`: Using `setAttribute()` to set attributes of HTML elements, particularly event handlers like `onclick` or `onload`, with user-controlled data can be exploited.
Example: Vulnerable and Secure JavaScript Code Snippets
The following example illustrates a vulnerable JavaScript code snippet and its secure, XSS-resistant alternative.
Vulnerable Code:
```javascript // Vulnerable code using document.write() function showMessage() let message = new URLSearchParams(window.location.search).get('message'); document.write('<div>' + message + '</div>'); showMessage(); ```
Explanation: This code retrieves a `message` parameter from the URL and writes it directly to the DOM using `document.write()`.If an attacker crafts a URL like `https://example.com/?message=<script>alert('XSS')</script>`, the script will be executed.
Secure Code:
```javascript // Secure code using textContent function showMessage() let message = new URLSearchParams(window.location.search).get('message'); let div = document.createElement('div'); div.textContent = message; document.body.appendChild(div); showMessage(); ```
Explanation: The secure code retrieves the `message` parameter.Instead of directly writing to the DOM using `document.write()`, it creates a `div` element, sets its `textContent` property to the `message`, and then appends the `div` to the `body`. The `textContent` property automatically escapes HTML entities, preventing the execution of any embedded HTML or JavaScript. This effectively prevents XSS vulnerabilities.
Final Summary
In conclusion, preventing cross-site scripting (XSS) attacks requires a multifaceted approach. By implementing robust input validation, employing output encoding, configuring content security policies, and adhering to security best practices, you can significantly reduce your website's vulnerability. Remember, staying informed about the latest threats and continuously updating your security measures is paramount. Embrace a proactive security mindset, and you'll be well-equipped to navigate the ever-changing landscape of web security, safeguarding both your data and your users' trust.
Helpful Answers
What is the primary goal of an XSS attack?
The primary goal of an XSS attack is to inject malicious scripts into a website to steal user data, hijack user sessions, or redirect users to malicious websites.
How does input validation help prevent XSS?
Input validation prevents XSS by ensuring that user-supplied data conforms to expected formats and does not contain malicious code. This can include filtering out potentially harmful characters or patterns.
What is the difference between HTML encoding and JavaScript encoding?
HTML encoding converts characters into their HTML entities (e.g., < becomes <). JavaScript encoding escapes characters so they are interpreted literally within JavaScript code. The appropriate encoding method depends on where the user input is being displayed.
What is a Content Security Policy (CSP)?
A Content Security Policy (CSP) is an HTTP response header that allows you to control the resources the browser is allowed to load for a given page. This can prevent XSS by limiting the sources from which scripts can be loaded.
How often should I conduct security audits?
Security audits should be conducted regularly, especially after significant code changes or updates. The frequency depends on the sensitivity of the data and the risk profile of the website. Consider annual or bi-annual audits at a minimum, or more frequently for high-risk applications.