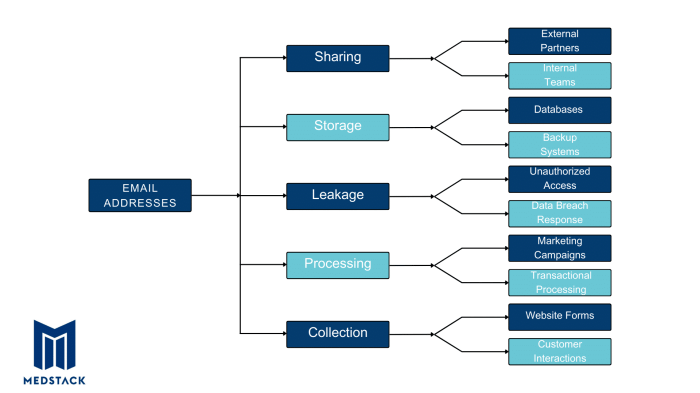
GDPR Data Residency and Sovereignty: Technical Controls for Compliance
This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...
152 posts in this category

This article explores the critical technical controls necessary for organizations to comply with GDPR regulations concerning data residency and sovere...

In the digital age, the integrity and admissibility of digital evidence are paramount for successful investigations. This article delves into the cruc...
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...
Handling cardholder data in the cloud necessitates adherence to Payment Card Industry Data Security Standard (PCI DSS) compliance. This guide provides...
This comprehensive article delves into the transformative technology of homomorphic encryption, exploring its core functionality, diverse types, and u...

This guide provides a comprehensive roadmap for establishing robust threat hunting capabilities, essential for proactively identifying and mitigating...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...
This comprehensive guide delves into the critical aspects of secure logging and monitoring within cloud environments, exploring its fundamental concep...

This guide provides a comprehensive overview of how to launch a successful career in the dynamic field of cloud security. It offers practical advice a...
Protecting sensitive API keys and tokens is crucial for maintaining application security and preventing costly data breaches. This article provides a...

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...