Embarking on a journey through the intricate world of cybersecurity, this guide, “How to Perform a Root Cause Analysis (RCA) for a Security Incident,” unveils the critical process of understanding and mitigating security breaches. In today’s digital landscape, security incidents are unfortunately inevitable. However, the ability to dissect these incidents, identify their origins, and prevent future occurrences is paramount. This comprehensive exploration delves into the methodologies, tools, and best practices required to conduct effective RCA, ensuring a more secure and resilient environment.
We will explore the fundamental principles of RCA, from gathering essential information and analyzing data to pinpointing the root cause and developing actionable solutions. You will learn how to define problem statements, utilize powerful analytical techniques such as the “5 Whys” and Fishbone diagrams, and develop corrective actions. Furthermore, the guide will cover the importance of thorough documentation, the use of specialized tools, and the avoidance of common pitfalls, all while providing real-world case studies to solidify your understanding.
This guide equips you with the knowledge to transform reactive responses into proactive, preventative strategies, fostering a robust security posture.
Introduction to Root Cause Analysis (RCA) for Security Incidents
Root Cause Analysis (RCA) is a systematic method used to identify the fundamental reasons behind an incident. In the realm of cybersecurity, RCA focuses on uncovering the underlying causes of security breaches and vulnerabilities, moving beyond the immediate symptoms to address the core issues. This approach aims to prevent future incidents by eliminating the root causes, rather than just treating the surface-level effects.Understanding the ‘why’ behind a security incident is paramount.
RCA provides a structured framework for investigating and learning from security failures. By identifying the root causes, organizations can implement effective preventative measures, improve their security posture, and mitigate the risk of future attacks. Failing to perform RCA after a security incident leaves the organization vulnerable to recurring issues and missed opportunities for improvement.
Fundamental Principles of RCA in Security Breaches
RCA in the context of security incidents adheres to several core principles. These principles guide the investigation process and ensure a thorough and effective analysis.
- Focus on the root cause, not just the symptoms: Instead of addressing the immediate consequences of a security breach (e.g., data loss), RCA delves into the underlying factors that allowed the breach to occur. This might involve investigating system misconfigurations, flawed security policies, or insufficient employee training.
- Gather factual evidence: RCA relies on concrete evidence, such as log files, system configurations, network traffic analysis, and witness testimonies. Subjective opinions and assumptions are minimized to ensure the analysis is based on verifiable data.
- Identify all contributing factors: Security incidents are often the result of multiple factors interacting with each other. RCA considers all contributing causes, not just the most obvious one. This could involve examining vulnerabilities in the software, human error, and the lack of proper security controls.
- Develop corrective actions to address the root causes: The ultimate goal of RCA is to implement solutions that eliminate the root causes and prevent recurrence. These corrective actions should be specific, measurable, achievable, relevant, and time-bound (SMART).
- Learn and improve continuously: RCA is not a one-time event. It’s a process of continuous learning and improvement. Organizations should regularly review and update their security policies, procedures, and controls based on the findings of RCA investigations.
Why RCA is Crucial After a Security Incident
Performing RCA after a security incident offers several critical benefits that contribute to an organization’s overall security resilience. It helps in several ways:
- Preventing Recurrence: The primary goal of RCA is to prevent future incidents. By identifying and addressing the root causes, organizations can implement measures to stop similar breaches from happening again.
- Improving Security Posture: RCA provides valuable insights into an organization’s security weaknesses. By analyzing the root causes of incidents, organizations can identify areas where their security controls are lacking and strengthen their defenses.
- Enhancing Incident Response: RCA can improve the effectiveness of incident response plans. By understanding the root causes of past incidents, organizations can refine their response procedures and train their staff to handle future incidents more effectively.
- Reducing Costs: Security incidents can be costly, involving expenses such as data recovery, legal fees, and reputational damage. RCA helps organizations minimize these costs by preventing future incidents and improving their overall security posture.
- Building a Security Culture: Conducting RCA demonstrates an organization’s commitment to security. This can help foster a security-conscious culture where employees are more aware of security risks and more likely to report potential vulnerabilities.
Common Security Incidents that Necessitate RCA
Various types of security incidents require a thorough RCA to understand the underlying causes and prevent future occurrences. Here are some examples:
- Data Breaches: When sensitive data is accessed or disclosed without authorization, RCA is essential to determine how the breach occurred. This includes analyzing the attack vector, identifying the vulnerabilities exploited, and assessing the impact of the breach. For example, a retailer experiences a data breach where customer credit card information is stolen. RCA could reveal that the breach was caused by a vulnerability in a web application, a weak password policy, and a lack of multi-factor authentication.
- Malware Infections: Infections by viruses, worms, and other malicious software can cause significant damage to systems and data. RCA helps identify the source of the infection, the methods used for propagation, and the vulnerabilities that were exploited. An example is a ransomware attack that encrypts an organization’s files. RCA could reveal that the ransomware entered the network through a phishing email, a lack of up-to-date patching, and inadequate endpoint security.
- Denial-of-Service (DoS) Attacks: These attacks aim to make a service unavailable to legitimate users. RCA helps determine the source of the attack, the vulnerabilities exploited, and the impact on the organization’s systems and services. A company’s website becomes unavailable due to a distributed denial-of-service (DDoS) attack. RCA could determine the attack originated from a botnet, highlighting the need for improved DDoS mitigation strategies.
- Unauthorized Access: Instances where individuals gain access to systems or data without proper authorization require RCA to identify the access method, the compromised credentials, and the systems affected. For instance, an employee gains unauthorized access to a restricted database. RCA could reveal that the employee used a stolen password or exploited a misconfigured access control list.
- System Outages: Unexpected system failures and service disruptions can be disruptive and costly. RCA helps identify the causes of these outages, whether they are related to hardware, software, or human error. A critical server crashes, causing significant downtime for a business. RCA might identify the root cause as a hardware failure, a software bug, or a lack of redundancy in the system design.
Preparing for an RCA
Following a security incident, a thorough root cause analysis (RCA) is crucial to understand what happened, why it happened, and how to prevent it from happening again. The preparation phase is critical, setting the foundation for a successful RCA. This involves meticulously gathering information, which forms the basis for identifying the root causes.
Initial Steps for Information Gathering
The initial steps after a security incident involve a rapid but methodical approach to secure the scene and begin collecting relevant information. The immediate actions taken are critical to preserving evidence and preventing further damage or data loss.
- Containment and Preservation: The primary goal is to contain the incident and prevent further harm. This might involve isolating affected systems, changing passwords, or blocking malicious network traffic. Simultaneously, it’s crucial to preserve all potential evidence. This includes documenting the state of the systems before any changes are made.
- Team Activation: Assemble the RCA team, including incident responders, security analysts, system administrators, and any relevant subject matter experts. Define roles and responsibilities to ensure a coordinated effort.
- Incident Documentation: Begin documenting the incident immediately. This should include the date and time of the incident, the affected systems, the impact of the incident, and the initial observations. This initial documentation serves as a chronological record of events.
- Communication: Establish clear communication channels with stakeholders, including management, legal counsel, and public relations, depending on the nature and severity of the incident. Keep them informed of the progress and findings.
Data Collection Methods
Collecting comprehensive data is essential for a complete RCA. The data collected should cover various aspects of the incident, including system logs, network traffic, and system configurations. Different methods are employed to collect data effectively.
- Log Analysis: System logs, application logs, and security logs are the primary sources of information. These logs record events, errors, and activities that occurred on the systems.
- Network Traffic Analysis: Network traffic captures, such as PCAP files, provide detailed information about network communications. Analyze these captures to identify malicious traffic, compromised systems, and data exfiltration attempts. Tools like Wireshark can be used to analyze the network traffic.
- System Configuration Analysis: Review system configurations to identify vulnerabilities or misconfigurations that might have contributed to the incident. This includes examining firewall rules, access controls, and software versions.
- Endpoint Forensics: If endpoints are involved, collect forensic images of the hard drives and memory. This allows for a detailed analysis of the system’s state at the time of the incident.
- Vulnerability Scanning: Perform vulnerability scans to identify any vulnerabilities that were exploited.
Evidence Documentation Checklist
A well-structured checklist ensures that all relevant evidence is documented and preserved. This checklist should be used throughout the information-gathering phase to maintain organization and completeness.
- Incident Details:
- Date and time of the incident
- Affected systems and applications
- Impact of the incident (e.g., data loss, system downtime)
- Initial observations
- Log Files:
- System logs (Windows Event Logs, syslog)
- Application logs (web server logs, database logs)
- Security logs (firewall logs, intrusion detection system logs)
- Log timestamps and time zones
- Log retention policies
- Network Data:
- Network traffic captures (PCAP files)
- Network device logs (firewall logs, router logs)
- Network diagrams
- IP addresses and domain names involved
- System Configuration:
- Operating system version and patch levels
- Software versions
- Firewall rules
- Access control lists (ACLs)
- User accounts and permissions
- System configuration backups
- Endpoint Data:
- Forensic images of hard drives and memory
- Malware samples (if applicable)
- Endpoint detection and response (EDR) logs
- Vulnerability Assessment Data:
- Vulnerability scan reports
- Penetration test reports (if available)
- Known vulnerabilities
- Communication Records:
- Emails and chat logs related to the incident
- Incident response reports
- Communication with stakeholders
- Chain of Custody:
- Documentation of who handled the evidence
- Date and time of evidence collection
- Location of the evidence
- Methods used to preserve the evidence
Identifying the Problem Statement
Defining the problem statement is a crucial step in Root Cause Analysis (RCA) for security incidents. A well-defined problem statement provides a clear and concise description of what happened, allowing the investigation team to focus their efforts effectively. It acts as a roadmap for the RCA process, guiding the team toward identifying the root causes and implementing effective solutions. A poorly defined problem statement, on the other hand, can lead to wasted time, misdirected efforts, and ultimately, ineffective solutions.
Formulating a Clear and Concise Problem Statement
Creating a problem statement that is both clear and concise involves several key techniques. It is essential to be specific and avoid vague language. The problem statement should clearly articulate what occurred, where it occurred, and when it occurred. This helps to set the scope of the investigation and prevents the team from getting sidetracked.
- Be Specific: Instead of stating “The network was slow,” specify “Network latency increased by 50% between 2:00 PM and 4:00 PM on October 26, 2023, affecting users in the Sales department.” This specificity helps pinpoint the affected system and time frame.
- Use Action-Oriented Language: Frame the problem statement using active verbs that describe the impact of the incident. For example, instead of “Data breach occurred,” use “Unauthorized access to sensitive customer data resulted in a data breach.”
- Focus on the Impact: Highlight the consequences of the incident. What was the impact on the organization? This helps prioritize the investigation and understand the severity of the problem. Consider the business impact, such as financial loss, reputational damage, or operational disruption.
- Define the Scope: Clearly state the boundaries of the problem. What systems or data were affected? What time period is relevant? This helps the team focus on the relevant information and avoid unnecessary investigation of unrelated areas.
- Avoid Assumptions: Do not include any assumptions about the root cause in the problem statement. The purpose of the RCA is to identify the root cause, not to assume it at the outset.
Examples of Problem Statements
Distinguishing between well-defined and vague problem statements is critical for a successful RCA. The following examples illustrate the difference.
| Type | Problem Statement | Analysis |
|---|---|---|
| Vague | “There was a security breach.” | This statement is too broad. It doesn’t specify what type of breach, where it occurred, or what data was affected. It offers no direction for the investigation. |
| Well-Defined | “On November 10, 2023, at approximately 10:00 AM PST, unauthorized access was detected to the company’s AWS S3 bucket containing confidential employee payroll data, resulting in the potential exposure of PII for 1,500 employees.” | This statement is specific. It details the date, time, location (AWS S3 bucket), type of data affected (employee payroll data), and the potential impact (exposure of PII). This provides a clear starting point for the RCA. |
| Vague | “Our website was down.” | This statement is too general. It doesn’t provide details about the cause, duration, or impact of the outage. |
| Well-Defined | “The company website experienced a denial-of-service (DoS) attack between 09:00 and 12:00 EST on December 1, 2023, rendering the website unavailable to customers and resulting in an estimated loss of $10,000 in potential revenue.” | This statement is precise. It specifies the type of attack (DoS), the timeframe, the impact (website unavailability), and the financial consequences. |
| Vague | “Data was lost.” | This statement is insufficiently detailed, as it does not indicate the type of data, the cause of the loss, or the extent of the damage. |
| Well-Defined | “On January 15, 2024, a ransomware attack encrypted the production database servers, resulting in the loss of customer order history data for the past 30 days and causing a disruption to order fulfillment processes.” | This statement provides key details, including the date, the nature of the attack (ransomware), the affected system (production database servers), the type of data lost (customer order history), and the impact on business operations (disruption to order fulfillment). |
These examples highlight the importance of precision in defining the problem statement. A well-defined statement allows for a more focused and efficient RCA, leading to more effective solutions.
Data Analysis Techniques for Security Incidents
Analyzing data is a crucial step in root cause analysis for security incidents. Employing various techniques helps investigators systematically uncover the underlying causes, leading to more effective remediation strategies. This section delves into three key data analysis techniques: the “5 Whys” method, the Fishbone diagram, and the Pareto Principle.
The “5 Whys” Method and Its Application
The “5 Whys” method is a simple yet powerful technique for identifying the root cause of a problem. It involves repeatedly asking “Why?” to drill down from the initial problem statement to the underlying cause. This iterative process helps to move beyond the symptoms and address the fundamental issues.To apply the “5 Whys” method effectively:
- Start with the Problem: Begin by clearly stating the security incident. For example, “Unauthorized access to the database occurred.”
- Ask “Why?”: Ask “Why?” to the initial problem. Document the answer. Example: “Why did unauthorized access occur?” Answer: “Weak password used by a privileged user.”
- Repeat “Why?”: Continue asking “Why?” based on the previous answer. Document each response. Example: “Why was a weak password used?” Answer: “Password policy was not enforced.”
- Continue the Process: Keep asking “Why?” until the root cause is identified. Example: “Why was the password policy not enforced?” Answer: “Lack of automated password enforcement tools.” “Why was there a lack of automated password enforcement tools?” Answer: “Insufficient budget allocated for security tools.” “Why was there insufficient budget?” Answer: “Security not prioritized by upper management.”
- Identify the Root Cause: The final “Why?” should reveal the root cause, which in this example is the lack of prioritization of security by upper management.
The “5 Whys” method is most effective when used collaboratively, involving individuals with relevant expertise and perspectives.
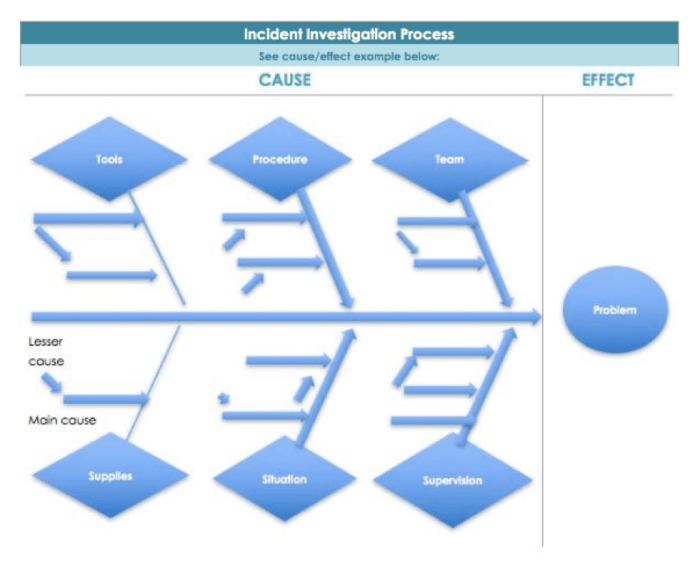
The Fishbone Diagram (Ishikawa Diagram)
The Fishbone diagram, also known as the Ishikawa diagram or cause-and-effect diagram, is a visual tool used to identify potential causes of a specific problem. It resembles the skeleton of a fish, with the problem statement at the “head” and potential causes branching out as “bones.”To construct a Fishbone diagram for a security incident:
- Define the Problem: Clearly state the security incident at the head of the diagram.
- Identify Main Categories: Determine the major categories of potential causes. Common categories in security incidents include:
- People: Related to human actions, errors, or training.
- Process: Related to procedures, policies, and workflows.
- Technology: Related to hardware, software, and network infrastructure.
- Environment: Related to physical security, environmental factors, and external threats.
- Brainstorm Potential Causes: For each category, brainstorm potential causes that could have contributed to the incident.
- Analyze and Refine: Review the diagram, prioritize the most likely causes, and identify areas for further investigation.
For instance, a Fishbone diagram for a malware infection might have “People” as a category with potential causes such as “Lack of user awareness training” or “Clicking on phishing emails.” “Technology” might include “Outdated antivirus software” or “Unpatched vulnerabilities.” The diagram provides a structured way to visualize and analyze the various factors that may have contributed to the incident.
Utilizing the Pareto Principle in Analyzing Incident Data
The Pareto Principle, also known as the 80/20 rule, suggests that roughly 80% of effects come from 20% of the causes. In the context of security incidents, this principle can be applied to prioritize investigation efforts and allocate resources effectively.To apply the Pareto Principle to incident data analysis:
- Collect Incident Data: Gather data related to security incidents, including the type of incident, the affected systems, the date and time, and any other relevant information.
- Categorize Incidents: Group incidents based on their type or cause. For example, group incidents into categories such as “Phishing attacks,” “Malware infections,” and “Unauthorized access attempts.”
- Calculate Incident Frequency: Determine the frequency of each incident category. This involves counting the number of incidents that fall into each category.
- Create a Pareto Chart: Create a Pareto chart, a bar graph that displays the frequency of each incident category in descending order. A cumulative line graph is often overlaid to show the cumulative percentage of incidents.
- Analyze the Chart: Identify the incident categories that contribute to the majority of incidents (the “vital few”). Focus investigation and remediation efforts on these categories.
For example, if a Pareto chart reveals that 80% of security incidents are caused by phishing attacks and malware infections, then investigation and remediation efforts should primarily focus on improving phishing detection and prevention measures, and patching vulnerabilities in systems. This focused approach allows for more efficient allocation of resources and a more significant impact on overall security posture.
Root Cause Identification
Pinpointing the root cause is the critical juncture in a security incident RCA. This phase moves beyond identifying the immediate effects and dives into the underlying reasons that allowed the incident to occur. The goal is to uncover the fundamental factors contributing to the event, enabling the implementation of effective and lasting preventative measures. Accurate root cause identification prevents recurrence and strengthens the overall security posture.
Root Cause Categories in Security Incidents
Security incidents can stem from a variety of root causes. Recognizing these categories helps in systematically investigating and addressing the issues. Understanding these categories facilitates a more targeted and effective approach to incident response and remediation.
- Human Error: This category encompasses mistakes made by individuals, such as misconfiguration of systems, clicking on phishing links, or failing to follow security protocols. These errors are often unintentional but can have significant consequences.
- System Vulnerabilities: These are weaknesses in software, hardware, or network infrastructure that can be exploited by attackers. This includes unpatched software, insecure configurations, and design flaws.
- Process Failures: This involves breakdowns in established procedures or lack of adequate processes. Examples include inadequate access controls, insufficient monitoring, and failure to regularly review security policies.
- Malicious Activity: This covers intentional actions by attackers, such as malware infections, data breaches, and denial-of-service attacks. These are often sophisticated and targeted attacks.
- Environmental Factors: These are external influences that contribute to security incidents, such as natural disasters, power outages, or physical security breaches.
Differentiating Symptoms and Root Causes
Distinguishing between symptoms and root causes is crucial for effective RCA. Symptoms are the observable effects of an incident, while root causes are the underlying reasons that led to the symptoms. Focusing solely on symptoms may address the immediate issue but won’t prevent future incidents.
Consider the analogy of a medical diagnosis. A fever is a symptom. The root cause might be an infection, requiring antibiotics to address the underlying problem, not just the fever.
To differentiate, ask “why” repeatedly. This helps peel back the layers of the incident to reveal the root cause. For example:
- Symptom: A server is down.
- Why? Because the hard drive failed.
- Why? Because the hard drive was old and nearing the end of its lifespan.
- Why? Because the hard drive replacement was not scheduled in the IT maintenance plan.
- Root Cause: Inadequate IT maintenance scheduling and budgeting for hardware replacement.
Tracing a Security Incident Back to Its Origin
Tracing an incident back to its origin involves a methodical investigation using various data sources and analytical techniques. This process requires a systematic approach to gather evidence, analyze the timeline of events, and identify the specific point of origin.
Here’s an example of how to trace a phishing attack:
- Incident: An employee’s account was compromised.
- Evidence Gathering: Reviewing logs, emails, and network traffic.
- Timeline Analysis: Determining the sequence of events, including when the suspicious email was received, when the user clicked the link, and when the account was accessed from an unusual location.
- Email Analysis: Examining the email’s headers to trace its origin.
- Network Traffic Analysis: Examining network traffic logs to identify the destination of the user’s clicks.
- User Activity Review: Investigating the actions taken after the account was compromised, such as data exfiltration or lateral movement within the network.
- Root Cause Identification: The phishing email, which contained a malicious link that directed the user to a fake login page that harvested credentials.
Another example is a data breach:
- Incident: Sensitive customer data was exposed.
- Evidence Gathering: Examining system logs, database access logs, and network traffic.
- Timeline Analysis: Determining when the data was accessed, modified, and exfiltrated.
- Log Analysis: Analyzing system logs to identify unauthorized access attempts, including the source IP addresses and user accounts involved.
- Database Access Logs Review: Examining database access logs to identify queries and operations performed on the compromised data.
- Network Traffic Analysis: Reviewing network traffic logs to identify data exfiltration.
- Root Cause Identification: A SQL injection vulnerability in a web application allowed attackers to bypass security controls and access the database.
Developing Corrective Actions and Recommendations
Following the identification of the root cause, the next crucial step in the RCA process involves developing and implementing corrective actions. These actions aim to address the underlying issues that led to the security incident, preventing its recurrence and improving the overall security posture. This phase requires careful planning, prioritization, and execution to ensure the effectiveness of the implemented solutions.
Framework for Developing Effective Corrective Actions
Creating a robust framework is essential for developing effective corrective actions. This framework should guide the process, ensuring that actions are targeted, measurable, achievable, relevant, and time-bound (SMART). The framework should incorporate a structured approach that considers various aspects of the incident and its root causes.A structured approach involves several key elements:
- Define the Objective: Clearly state the desired outcome of the corrective action. For instance, the objective might be to “prevent unauthorized access to sensitive data” or “reduce the mean time to detect and respond to security incidents.”
- Brainstorm Potential Solutions: Generate a wide range of potential corrective actions. This can involve a brainstorming session with a team of stakeholders, considering all possible solutions, even those that initially seem less viable.
- Evaluate Each Solution: Assess each potential solution based on its effectiveness in addressing the root cause, its feasibility, its cost, and its potential impact on the organization.
- Select the Best Solutions: Choose the corrective actions that offer the most effective and practical solutions, considering the evaluation results.
- Document the Corrective Actions: Clearly document each selected corrective action, including its scope, implementation steps, responsible parties, and expected outcomes.
- Implement the Corrective Actions: Put the selected corrective actions into action. This involves assigning tasks, allocating resources, and establishing timelines.
- Monitor and Evaluate: Continuously monitor the implemented corrective actions to assess their effectiveness. Evaluate whether they are achieving the desired outcomes and make adjustments as needed.
Prioritizing Corrective Actions
Prioritizing corrective actions is critical, especially when resources are limited. Prioritization helps ensure that the most impactful and feasible actions are addressed first. This process involves assessing each corrective action based on its potential impact on preventing future incidents and its feasibility of implementation.Prioritization is often achieved by evaluating two key factors:
- Impact: This refers to the potential severity of the consequences if the security incident were to recur. Impact can be assessed based on factors such as financial loss, reputational damage, legal and regulatory penalties, and disruption of business operations. A high-impact action is one that, if not implemented, could lead to significant negative consequences.
- Feasibility: This refers to the ease with which a corrective action can be implemented. Feasibility considers factors such as the cost of implementation, the availability of resources, the technical complexity, and the time required for implementation. A highly feasible action is one that can be implemented relatively easily and quickly.
Corrective actions can be categorized using an impact/feasibility matrix, where actions are plotted based on their impact and feasibility. This matrix helps visualize the prioritization process:
- High Impact/High Feasibility: These actions should be prioritized and implemented immediately.
- High Impact/Low Feasibility: These actions require careful planning and resource allocation, potentially involving phased implementation or seeking external expertise.
- Low Impact/High Feasibility: These actions can be implemented as resources become available, offering incremental improvements to security.
- Low Impact/Low Feasibility: These actions should be deprioritized or considered only if they can be implemented at minimal cost and effort.
Organizing Corrective Actions
Organizing corrective actions in a structured format facilitates communication, tracking, and implementation. A table format is a practical way to present corrective actions, their impact, and implementation timelines.
| Corrective Action | Root Cause Addressed | Impact (High/Medium/Low) | Estimated Implementation Time |
|---|---|---|---|
| Implement Multi-Factor Authentication (MFA) for all privileged accounts. | Compromised credentials. | High | 2 weeks |
| Enhance security awareness training for all employees. | Lack of employee awareness of phishing and social engineering tactics. | Medium | 1 month |
| Update and patch all vulnerable software. | Unpatched vulnerabilities exploited by attackers. | High | Ongoing (continuous patching cycle) |
| Implement a Security Information and Event Management (SIEM) system. | Lack of centralized logging and monitoring. | Medium | 3 months |
Implementing and Monitoring Corrective Actions
After identifying the root cause and developing corrective actions, the next crucial phase involves implementing these solutions and continuously monitoring their effectiveness. This step ensures that the implemented changes address the underlying issues and prevent future security incidents. This section Artikels the implementation process, monitoring methods, and the importance of regular reviews and updates.
Implementing Corrective Actions
Implementing corrective actions involves a systematic approach to ensure that the proposed solutions are effectively put into practice. This process typically includes the following steps:
- Planning and Prioritization: This involves creating a detailed implementation plan that Artikels the specific steps required, the resources needed (personnel, budget, tools), and a timeline for completion. Prioritization is crucial, focusing on actions that have the most significant impact on mitigating the identified risks. For instance, if a vulnerability scan revealed a critical unpatched system, patching that system would be a high-priority corrective action.
- Resource Allocation: Securing the necessary resources is essential for successful implementation. This includes allocating budget for software, hardware, or training, as well as assigning personnel with the appropriate skills and expertise to execute the corrective actions.
- Execution: This involves putting the corrective actions into practice. This might include deploying security software, updating configurations, implementing new policies and procedures, or providing training to employees. Thorough documentation of all actions taken is crucial for future reference and audit purposes. For example, if the root cause was a lack of multi-factor authentication (MFA), execution would involve deploying an MFA solution across the organization and configuring it for all relevant systems and user accounts.
- Testing and Validation: After implementation, it is essential to test and validate the effectiveness of the corrective actions. This can involve penetration testing, vulnerability scanning, or simply verifying that the implemented changes function as intended and address the identified vulnerabilities. If the implemented MFA solution works as expected, users can log in securely with MFA.
- Communication and Training: Ensure that all relevant stakeholders are informed about the implemented changes. Providing adequate training to employees on new security procedures or tools is crucial for ensuring their understanding and compliance.
Monitoring the Effectiveness of Implemented Solutions
Monitoring the effectiveness of implemented solutions is a continuous process that helps ensure that the corrective actions are working as intended and that the security posture of the organization is improving. Effective monitoring involves:
- Defining Metrics: Establish clear and measurable metrics to assess the effectiveness of the corrective actions. These metrics should be directly related to the root cause and the implemented solutions. Examples include the number of successful phishing attempts before and after implementing phishing awareness training, or the number of security incidents before and after implementing a new intrusion detection system.
- Data Collection: Collect data relevant to the defined metrics. This may involve reviewing security logs, conducting vulnerability scans, performing penetration tests, or surveying users.
- Analysis and Reporting: Regularly analyze the collected data to identify trends, patterns, and anomalies. Generate reports that summarize the findings and provide insights into the effectiveness of the corrective actions. This information should be presented to relevant stakeholders, including management and the security team.
- Continuous Monitoring Tools: Utilize security information and event management (SIEM) systems, intrusion detection/prevention systems (IDS/IPS), and vulnerability scanners to automate the monitoring process and provide real-time insights into the security posture. SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events.
- Examples of Monitoring Effectiveness:
- Vulnerability Patching: Monitor the time it takes to patch vulnerabilities and track the number of unpatched systems.
- User Training: Track the completion rate of security awareness training and assess user behavior through simulated phishing attacks.
- Network Security: Monitor network traffic for suspicious activity using IDS/IPS and analyze security logs for unusual events.
Procedure for Regularly Reviewing and Updating Security Measures
Regular review and updates are crucial to maintain a strong security posture, adapt to evolving threats, and ensure the continued effectiveness of the implemented corrective actions. This involves:
- Scheduled Reviews: Establish a schedule for regular reviews of security measures. The frequency of these reviews should be based on the criticality of the assets, the frequency of security incidents, and the rate of change in the threat landscape. For example, critical systems should be reviewed more frequently than less sensitive ones.
- Documentation Review: Review all relevant security documentation, including policies, procedures, and standards, to ensure they are up-to-date and aligned with current best practices and regulations.
- Risk Assessment: Conduct periodic risk assessments to identify new threats, vulnerabilities, and potential impacts to the organization. This assessment should consider changes in the business environment, technology, and the threat landscape.
- Vulnerability Scanning and Penetration Testing: Conduct regular vulnerability scans and penetration tests to identify and assess vulnerabilities in systems and applications. These tests should be performed by qualified personnel or third-party vendors.
- Incident Analysis: Analyze all security incidents to identify trends, patterns, and root causes. This analysis should inform the development of new corrective actions and updates to existing security measures.
- Technology Updates: Stay informed about the latest security technologies and best practices. Consider implementing new security tools and techniques to improve the organization’s security posture.
- Stakeholder Feedback: Gather feedback from stakeholders, including employees, customers, and partners, to identify areas for improvement and ensure that security measures are meeting their needs.
- Reporting and Communication: Prepare reports summarizing the findings of the reviews and updates. Communicate these findings to relevant stakeholders, including management and the security team. The reporting should also provide recommendations for improvement and a plan for implementing them.
Documentation and Reporting
Effective documentation and clear reporting are crucial components of a successful Root Cause Analysis (RCA) for security incidents. They ensure the RCA process is transparent, repeatable, and provides valuable insights for preventing future incidents. Meticulous record-keeping throughout the RCA process, culminating in a comprehensive report, is essential for communicating findings, recommendations, and the overall impact of the incident to stakeholders.
Importance of Comprehensive Documentation
Maintaining detailed documentation throughout the RCA process offers several significant benefits. It serves as a historical record, enabling organizations to track incident trends, evaluate the effectiveness of implemented solutions, and demonstrate due diligence in security practices. It also provides a basis for continuous improvement in security posture.
- Tracking the RCA Process: Documentation captures every step of the RCA, including the initial problem identification, data collection, analysis techniques used, root cause identification, corrective actions proposed, and the implementation status. This detailed record provides a clear audit trail.
- Facilitating Knowledge Sharing: Well-documented RCAs serve as a valuable resource for other security professionals and teams. It enables the organization to share lessons learned, understand the context of previous incidents, and proactively prevent similar issues.
- Supporting Regulatory Compliance: Many industries and regulatory bodies require detailed documentation of security incidents and the actions taken to address them. Comprehensive documentation demonstrates compliance and can mitigate potential penalties.
- Improving Incident Response: Documented RCAs can improve the speed and effectiveness of future incident responses. The documentation provides a foundation for understanding the vulnerabilities that led to previous incidents.
- Supporting Continuous Improvement: Analyzing past RCAs allows organizations to identify recurring issues, evaluate the effectiveness of security controls, and improve their overall security posture. The documented RCA data provides the necessary foundation for ongoing improvements.
Security Incident RCA Report Template
A standardized RCA report template ensures consistency and facilitates efficient communication of findings. This template Artikels the key sections typically included in a security incident RCA report. Adapting this template to the specific needs of an organization is advisable.
| Section | Description |
|---|---|
| Executive Summary | A concise overview of the incident, its impact, the root cause(s), and the key recommendations. This section is aimed at stakeholders who need a high-level understanding. |
| Incident Overview | Provides a detailed description of the incident, including the date and time, systems affected, and a timeline of events. |
| Problem Statement | Clearly defines the security incident, outlining what happened, when it happened, and the observed impact. |
| Data Collection and Analysis | Describes the data sources used (logs, system configurations, etc.) and the analysis techniques employed to investigate the incident. |
| Root Cause(s) | Identifies the underlying cause(s) of the security incident, supported by evidence from the data analysis. |
| Contributing Factors | Lists any other factors that contributed to the incident but were not the primary root cause. |
| Impact Assessment | Details the impact of the incident, including financial losses, reputational damage, and any operational disruptions. |
| Corrective Actions and Recommendations | Artikels the specific actions recommended to prevent similar incidents from occurring in the future, including responsible parties and timelines. |
| Implementation Plan | Provides details on how the corrective actions will be implemented, including resources required and any dependencies. |
| Monitoring and Verification | Describes how the effectiveness of the corrective actions will be monitored and verified. |
| Lessons Learned | Summarizes the key lessons learned from the incident and the RCA process. |
| Appendices | Includes supporting documentation, such as log extracts, system diagrams, and any other relevant data. |
Guidelines for Communicating Findings and Recommendations to Stakeholders
Effective communication of RCA findings and recommendations is crucial for gaining stakeholder buy-in and ensuring the successful implementation of corrective actions. Tailoring the communication style and content to the audience is vital.
- Identify Your Audience: Determine the key stakeholders, including technical teams, management, legal counsel, and potentially external parties. Tailor the report and presentation to their level of technical understanding and their specific interests.
- Choose the Right Communication Channels: Use a combination of written reports, presentations, and meetings to communicate the findings and recommendations. The choice of channels depends on the audience and the importance of the information.
- Be Clear and Concise: Use clear, concise language, avoiding technical jargon when communicating with non-technical audiences. Focus on the key findings, root causes, and recommendations.
- Provide Visual Aids: Use charts, graphs, and diagrams to illustrate the findings and impact of the incident. Visual aids can make complex information easier to understand. For example, a timeline of events can visually represent the sequence of actions.
- Focus on Solutions: Emphasize the proposed corrective actions and recommendations. Clearly articulate the benefits of implementing these actions and the potential impact on the organization’s security posture.
- Address Concerns and Questions: Be prepared to answer questions and address any concerns that stakeholders may have. Be transparent and honest about the incident and the RCA process.
- Present the Information in a Structured Manner: Use a logical and organized structure for your report and presentations. This will help stakeholders understand the information and follow the RCA process. The structure should generally follow the RCA report template.
- Follow Up: After communicating the findings and recommendations, follow up with stakeholders to ensure that they understand the information and are committed to implementing the corrective actions.
- Example: When presenting to senior management, focus on the business impact, the root cause(s), and the cost-benefit analysis of the proposed corrective actions. Use non-technical language and avoid getting bogged down in technical details.
Tools and Technologies for RCA
Performing a thorough Root Cause Analysis (RCA) for security incidents often requires leveraging various tools and technologies. These tools assist in data collection, analysis, and ultimately, the identification of the root cause. Effective use of these resources streamlines the process, improves accuracy, and reduces the time required to resolve incidents.
Software Tools Used in RCA
Several software tools are essential for conducting a comprehensive RCA. These tools span across different categories, each serving a specific purpose in the analysis process.
- Log Management Systems (SIEM): Security Information and Event Management (SIEM) systems aggregate and analyze security logs from various sources, such as servers, network devices, and applications. They provide real-time monitoring, alerting, and reporting capabilities. Examples include Splunk, IBM QRadar, and Microsoft Sentinel.
- Network Monitoring Tools: These tools monitor network traffic, identify anomalies, and provide insights into network performance. They are crucial for understanding network-related issues contributing to a security incident. Examples include Wireshark, SolarWinds Network Performance Monitor, and PRTG Network Monitor.
- Endpoint Detection and Response (EDR) Tools: EDR tools provide real-time monitoring and analysis of endpoint activities, such as process execution, file modifications, and network connections. They are instrumental in identifying malware infections and other endpoint-based threats. Examples include CrowdStrike Falcon, SentinelOne, and Microsoft Defender for Endpoint.
- Vulnerability Scanners: These tools scan systems and applications for vulnerabilities, helping to identify potential entry points for attackers. Examples include Nessus, OpenVAS, and Qualys.
- Incident Management Systems: These systems help manage the entire incident lifecycle, from detection and reporting to resolution and post-incident analysis. They facilitate collaboration, track progress, and provide a centralized repository for incident-related information. Examples include ServiceNow, Jira Service Management, and ManageEngine ServiceDesk Plus.
- Forensic Analysis Tools: These tools are used to collect and analyze digital evidence from compromised systems. They help investigators understand the scope of the incident and identify the attacker’s actions. Examples include EnCase, FTK, and Autopsy.
Comparison of Log Analysis and Incident Management Tools
Different log analysis and incident management tools offer varying features and capabilities. Choosing the right tool depends on the specific needs and requirements of the organization.
- Splunk vs. ELK Stack (Elasticsearch, Logstash, Kibana):
- Splunk: A commercial SIEM solution known for its user-friendly interface, powerful search capabilities, and extensive app ecosystem. It excels in handling large volumes of data and providing real-time analytics. Its strength lies in its ability to analyze and visualize complex data sets. Splunk’s proprietary nature means it has licensing costs.
- ELK Stack: An open-source stack comprising Elasticsearch (for indexing and searching), Logstash (for data collection and processing), and Kibana (for data visualization). It offers flexibility, scalability, and cost-effectiveness. The ELK Stack requires more technical expertise to set up and manage compared to Splunk.
- IBM QRadar vs. Microsoft Sentinel:
- IBM QRadar: A SIEM solution that provides comprehensive security monitoring, threat detection, and incident response capabilities. It integrates with a wide range of security products and offers advanced analytics features. It is well-suited for organizations with complex security environments.
- Microsoft Sentinel: A cloud-native SIEM solution that leverages Microsoft’s security intelligence and integrates with other Microsoft security products. It offers automated threat detection, incident response, and security orchestration capabilities. It is an ideal choice for organizations that have a significant investment in Microsoft technologies.
- ServiceNow vs. Jira Service Management:
- ServiceNow: An enterprise-grade incident management platform that provides a comprehensive suite of features, including incident management, problem management, change management, and IT service management (ITSM). It is designed for large organizations with complex IT environments.
- Jira Service Management: A service desk platform that integrates with Atlassian’s other products, such as Jira Software and Confluence. It is a popular choice for agile teams and organizations that need a flexible and customizable solution. It offers a wide range of features for incident management, problem management, and knowledge base management.
The Role of Automation in Streamlining the RCA Process
Automation plays a crucial role in streamlining the RCA process, reducing the time and effort required to identify root causes. Automating repetitive tasks allows security teams to focus on more complex analysis and decision-making.
- Automated Data Collection: Automation tools can automatically collect and aggregate data from various sources, such as logs, network traffic, and endpoint activity. This eliminates the need for manual data gathering, saving time and reducing the risk of human error.
- Automated Analysis: Machine learning and artificial intelligence (AI) can be used to automate the analysis of security data, identify anomalies, and correlate events. This can accelerate the identification of potential root causes. For instance, AI-powered tools can analyze network traffic patterns to detect unusual behavior that may indicate a security breach.
- Automated Reporting: Automation can generate reports and dashboards that provide insights into security incidents and the RCA process. This allows security teams to quickly understand the scope of the incident, identify the root cause, and track progress toward resolution.
- Automated Incident Response: Automation can be used to automate incident response tasks, such as isolating compromised systems, blocking malicious traffic, and containing the spread of malware. This can help to minimize the impact of security incidents and reduce the time to resolution.
Common Challenges and Pitfalls in RCA
Conducting a Root Cause Analysis (RCA) for security incidents is a critical process, but it is not without its challenges. Numerous pitfalls can hinder the effectiveness of an RCA, leading to inaccurate conclusions and ineffective corrective actions. Understanding these common issues and implementing strategies to mitigate them is essential for a successful RCA.
Avoiding Biases and Assumptions
Bias and assumptions can significantly skew the results of an RCA, leading to incorrect conclusions. Recognizing and mitigating these issues is crucial for maintaining objectivity.
- Confirmation Bias: This occurs when analysts seek or interpret information that confirms pre-existing beliefs or hypotheses. To avoid this, actively seek out contradictory evidence and consider alternative explanations. For example, if an initial assessment suggests a phishing attack, don’t solely focus on evidence supporting this theory; also, investigate other potential causes, such as compromised credentials or vulnerabilities.
- Availability Heuristic: This bias leads to over-reliance on readily available information, often the most recent or easily accessible data. This can result in overlooking less obvious but potentially more significant factors. To mitigate this, ensure a comprehensive data collection process, including logs, reports, and interviews.
- Anchoring Bias: This occurs when the initial piece of information (the “anchor”) unduly influences subsequent judgments and decisions. For example, if the initial incident report suggests a specific cause, analysts may become anchored to that cause, even if later evidence suggests otherwise. To combat this, consider multiple potential causes at the outset and be open to revising initial assumptions as new information emerges.
- Groupthink: This occurs when a group of individuals prioritize conformity and cohesion over critical thinking, leading to poor decision-making. Encourage diverse perspectives and critical evaluation of all ideas. Facilitate open communication, where all members feel comfortable expressing dissenting opinions.
- Premature Closure: This happens when the analysis concludes too quickly, without sufficient investigation. This often results from time pressures or a desire to resolve the incident swiftly. Ensure a thorough investigation is conducted, even if it takes more time, to identify the true root cause.
Pitfalls to Avoid and Mitigation Strategies
Several specific pitfalls can derail an RCA. Understanding these and implementing proactive mitigation strategies is key to a successful analysis.
- Focusing on Symptoms Instead of Causes: A common mistake is addressing the immediate symptoms of the incident rather than the underlying root cause. This leads to temporary fixes that do not prevent future occurrences. For example, if a system outage is caused by a faulty patch, fixing the outage is addressing a symptom. The RCA should investigate why the patch failed (e.g., insufficient testing, inadequate deployment procedures).
Focus on “Why” not “What” or “How”. The “5 Whys” technique can be extremely useful in this context.
- Lack of Clear Scope and Objectives: Without a well-defined scope and clear objectives, the RCA can become unfocused and ineffective. Define the scope of the incident, the specific objectives of the analysis, and the desired outcomes. This helps keep the investigation on track.
- Inadequate Data Collection: Relying on incomplete or inaccurate data will lead to flawed conclusions. Ensure a thorough data collection process, including all relevant logs, system configurations, network diagrams, and interview transcripts. Validate the data’s accuracy.
- Poor Communication and Collaboration: A lack of communication and collaboration among the team members can hinder the RCA process. Establish clear communication channels, assign roles and responsibilities, and hold regular meetings to discuss progress and findings.
- Ignoring the Human Element: Security incidents often involve human error or negligence. Ignoring the human element can lead to incomplete and ineffective corrective actions. Investigate human factors, such as inadequate training, unclear policies, or insufficient awareness.
- Failing to Implement Corrective Actions: Identifying the root cause is only the first step. If corrective actions are not implemented, the incident will likely recur. Develop a detailed action plan, assign responsibilities, and track progress to ensure that corrective actions are implemented effectively.
- Insufficient Documentation: Poor documentation can make it difficult to replicate the RCA process, learn from past incidents, or comply with regulatory requirements. Document all steps of the RCA process, including data collection, analysis, findings, and recommendations.
Case Studies: Real-World Examples
Root Cause Analysis (RCA) is best understood through practical application. Examining real-world security incidents and the RCA processes employed to address them provides valuable insights into the methodologies, challenges, and benefits of this crucial investigative technique. This section presents a detailed case study, illustrating the steps involved in a security incident RCA and highlighting the lessons learned.This case study focuses on a ransomware attack targeting a healthcare provider, detailing the incident’s impact, the RCA process, and the resulting corrective actions.
This example provides a clear understanding of how RCA can identify vulnerabilities and prevent future incidents.
Ransomware Attack on a Healthcare Provider: Case Study
The scenario involves a significant ransomware attack on a mid-sized healthcare provider, “HealthFirst.” The attack encrypted critical patient data, disrupting operations, and leading to significant financial and reputational damage. The incident required a comprehensive RCA to understand the attack’s root causes and prevent future occurrences.The RCA process at HealthFirst involved several key steps:
- Incident Detection and Initial Response: HealthFirst’s security team detected unusual activity on the network, including encrypted files and ransom notes. The initial response involved isolating affected systems, notifying relevant stakeholders, and activating the incident response plan.
- Problem Definition: The problem was clearly defined as a successful ransomware attack that encrypted critical patient data, leading to service disruption, potential data breaches, and financial losses.
- Data Collection: Extensive data collection was undertaken. This included:
- Network Logs: Analyzing network traffic logs to identify the attack vector, including any external connections, compromised accounts, and lateral movement within the network.
- System Logs: Examining system logs from affected servers and endpoints to identify the point of entry, the execution of malicious code, and the extent of data encryption.
- Endpoint Forensics: Performing forensic analysis on compromised endpoints to determine the malware’s origin, propagation methods, and the specific vulnerabilities exploited.
- Security Information and Event Management (SIEM) Data: Utilizing SIEM data to correlate events, identify suspicious activities, and visualize the attack timeline.
- Vulnerability Scan Reports: Reviewing vulnerability scan reports to identify pre-existing weaknesses in the infrastructure that may have been exploited.
- Data Analysis: The collected data was analyzed to understand the attack’s timeline, attack vector, and impact. This included:
- Timeline Reconstruction: Reconstructing the attack timeline to determine the sequence of events, from initial compromise to data encryption.
- Attack Vector Identification: Identifying the method used to gain initial access, such as phishing, compromised credentials, or exploitation of a known vulnerability. In this case, the RCA revealed that the attackers gained initial access through a phishing email containing a malicious attachment.
- Impact Assessment: Assessing the extent of the data encryption, the number of affected systems, and the potential impact on patient care and data privacy.
- Root Cause Identification: The RCA identified several root causes:
- Phishing Vulnerability: The primary root cause was a successful phishing campaign targeting employees, leading to the compromise of user credentials and the installation of malware.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA on critical systems allowed attackers to move laterally within the network using compromised credentials.
- Unpatched Vulnerabilities: Outdated software and unpatched vulnerabilities on servers and endpoints provided opportunities for attackers to exploit known weaknesses.
- Insufficient Security Awareness Training: Lack of comprehensive security awareness training among employees made them susceptible to phishing attacks.
- Inadequate Network Segmentation: Poor network segmentation allowed the attackers to move laterally throughout the network, increasing the scope of the attack.
- Corrective Actions and Recommendations: Based on the identified root causes, HealthFirst implemented the following corrective actions:
- Enhanced Phishing Protection: Implementing advanced email filtering, anti-phishing training for employees, and regular simulated phishing exercises.
- Implementation of MFA: Enforcing MFA on all critical systems and accounts, including email, VPN access, and remote access.
- Vulnerability Management Program: Establishing a robust vulnerability management program, including regular vulnerability scanning, patch management, and timely remediation of identified vulnerabilities.
- Improved Security Awareness Training: Conducting comprehensive security awareness training for all employees, covering topics such as phishing, social engineering, and password security.
- Network Segmentation: Implementing network segmentation to limit the impact of future attacks, isolating critical systems and data.
- Incident Response Plan Updates: Reviewing and updating the incident response plan to include procedures for ransomware attacks, data recovery, and communication protocols.
- Implementation and Monitoring: HealthFirst implemented the corrective actions and established monitoring mechanisms to assess their effectiveness. This included regular security audits, vulnerability scans, and monitoring of network traffic and system logs.
- Documentation and Reporting: A comprehensive report was prepared documenting the RCA process, the findings, the corrective actions, and the lessons learned. This report served as a reference for future security incidents and a basis for continuous improvement.
The HealthFirst case study demonstrates the value of a structured RCA process in identifying the root causes of a security incident and implementing effective corrective actions. By addressing the underlying vulnerabilities, HealthFirst significantly improved its security posture and reduced the risk of future ransomware attacks. The lessons learned from this incident highlighted the importance of a proactive security approach, including strong security awareness training, robust vulnerability management, and the implementation of multi-factor authentication.
Closing Summary
In conclusion, mastering the art of Root Cause Analysis is indispensable for any organization striving to fortify its digital defenses. By understanding the core principles, employing the right tools, and learning from real-world examples, you can effectively transform security incidents into valuable learning experiences. This guide has provided a comprehensive framework for conducting RCA, from the initial incident response to the implementation of preventative measures.
Embrace this knowledge, and equip yourself with the ability to not only react to security breaches but to proactively prevent them, creating a safer and more secure digital future.
FAQs
What is the primary goal of a Root Cause Analysis (RCA)?
The primary goal of RCA is to identify the underlying causes of a security incident to prevent its recurrence, rather than simply addressing the symptoms.
How long should an RCA process take?
The duration of an RCA can vary depending on the complexity of the incident. Simple incidents might take a few days, while more complex ones could require weeks or even months.
What are the key benefits of performing RCA?
Key benefits include preventing future incidents, improving security posture, reducing operational costs, enhancing team knowledge, and fostering a culture of continuous improvement.
Who should be involved in the RCA process?
The RCA team should include individuals with relevant expertise, such as security analysts, system administrators, network engineers, and representatives from affected departments.
What is the difference between a symptom and a root cause?
A symptom is an observable effect of a problem, while the root cause is the fundamental reason the problem occurred. For example, a compromised account (symptom) may be caused by weak passwords (root cause).