Embark on a journey to understand GitOps, a revolutionary approach to managing infrastructure and applications. This methodology leverages Git as the single source of truth, streamlining deployment processes and fostering collaboration. Explore its origins, from its roots in DevOps practices to its current status as a cornerstone of modern software development.
GitOps has transformed how teams manage their systems, from its core principles to the tools and technologies that power it. It offers a declarative approach, where the desired state of the system is defined in code and automatically reconciled, leading to increased efficiency, reliability, and security. Let’s delve into the intricacies of GitOps, exploring its components, workflow, benefits, and its impact on various aspects of software development and infrastructure management.
Introduction to GitOps
GitOps is a modern approach to managing infrastructure and application deployments, leveraging Git as the single source of truth. It simplifies the process of deploying and operating applications, making it more reliable, repeatable, and efficient. By treating infrastructure as code and version-controlling it in Git, GitOps allows for automated deployments, easy rollbacks, and enhanced collaboration.GitOps focuses on declarative configuration, which means you define the desired state of your system, and the GitOps tools automatically ensure that the system matches that state.
This approach reduces the risk of human error and provides a clear audit trail of all changes.
Core Concept of GitOps
GitOps centers around using Git repositories to store the desired state of your infrastructure and applications. When changes are made to the Git repository, they trigger automated processes that update the live environment to match the new configuration. This ensures that what is defined in Git is what is running in production.The central idea is:
“Everything as code, managed by Git.”
This principle means that all aspects of your system, from infrastructure configuration to application deployments, are described in code and stored in Git.
Brief History of GitOps
GitOps emerged in the mid-2010s, primarily driven by the need for more efficient and reliable deployment practices in cloud-native environments, particularly those utilizing Kubernetes. The term “GitOps” was coined by Alexis Richardson, the CEO of Weaveworks, a company that played a significant role in developing and popularizing GitOps practices.The evolution of GitOps can be traced through several key stages:
- Early Adoption (2017-2018): Initial experimentation and the development of core principles. Focus was on automating deployments and infrastructure management using Git.
- Growing Maturity (2019-2020): Increased adoption, development of GitOps tools, and expansion beyond Kubernetes. The emphasis shifted to incorporating security, observability, and governance into GitOps workflows.
- Wider Acceptance (2021-Present): GitOps is now a mainstream approach, with broader industry adoption and the integration of GitOps principles into various DevOps and cloud-native platforms.
Fundamental Principles of GitOps
GitOps is guided by several core principles that contribute to its effectiveness:
- Declarative Configuration: Instead of specifying
-how* to achieve a state, you define
-what* the desired state should be. Tools then automatically manage the transition. For instance, instead of manually creating a Kubernetes deployment, you declare the desired deployment configuration in a YAML file, and a GitOps operator ensures that Kubernetes matches this configuration. - Version Control: All system configurations are stored in Git repositories, providing a complete history of changes, enabling easy rollbacks, and fostering collaboration. Every change to the infrastructure or application is tracked and auditable.
- Automation: Changes to the Git repository automatically trigger the deployment process. This ensures that the live environment always reflects the state defined in Git. Automation reduces manual errors and speeds up deployments.
- Observability: The state of the system is continuously monitored and compared to the desired state in Git. Any discrepancies are automatically detected and corrected, ensuring that the system remains in the desired configuration.
- Immutability: The deployed infrastructure and applications are treated as immutable. Changes are made by creating new versions of the configuration in Git and deploying them. This approach simplifies rollbacks and reduces the risk of configuration drift.
GitOps vs. Traditional Operations
The shift from traditional operational models to GitOps represents a significant evolution in how infrastructure and applications are managed. Understanding the key differences between these approaches is crucial for organizations seeking to modernize their software delivery pipelines and improve operational efficiency. This section will explore these differences, highlighting the roles of various teams, and comparing the advantages and disadvantages of each methodology.
Key Differences in Approach
The core distinction lies in how infrastructure and application configurations are managed and deployed. Traditional operations often rely on manual processes, scripting, and ad-hoc changes, whereas GitOps leverages Git as the single source of truth, automating and versioning all changes.
| Feature | Traditional Operations | GitOps |
|---|---|---|
| Configuration Management | Manual configuration, scripting, and configuration management tools. | Declarative configuration stored in Git repositories. |
| Deployment Process | Manual deployments, often requiring downtime. | Automated deployments triggered by changes in Git, often with zero downtime. |
| Version Control | Limited or no version control for infrastructure configurations. | Full version control using Git, enabling rollbacks and audit trails. |
| Change Management | Manual change approval processes and potential for human error. | Automated change management with built-in audit trails and rollback capabilities. |
Roles of Developers and Operations Teams
The responsibilities of developers and operations teams also change significantly with GitOps.
- Traditional Operations: In traditional models, operations teams typically handle infrastructure provisioning, deployment, and monitoring. Developers focus on writing code and may have limited involvement in the operational aspects of their applications. This often leads to a separation of concerns and potential communication bottlenecks.
- GitOps: GitOps promotes a more collaborative approach. Developers become more involved in the operational aspects, as they manage configurations through Git. Operations teams focus on building and maintaining the GitOps pipeline and ensuring the overall system’s health. This fosters a shared responsibility model.
Advantages and Disadvantages
Both approaches have their strengths and weaknesses. Understanding these trade-offs is essential for making informed decisions.
- Advantages of Traditional Operations:
- Well-established practices and readily available expertise.
- Familiarity with existing tools and processes.
- Potentially simpler to implement initially for smaller organizations.
- Disadvantages of Traditional Operations:
- Manual processes are prone to human error.
- Slow deployment cycles.
- Difficult to achieve consistent environments.
- Limited automation and scalability.
- Difficult to troubleshoot and rollback changes.
- Advantages of GitOps:
- Improved automation and efficiency.
- Faster deployment cycles.
- Increased reliability and consistency.
- Enhanced security through version control and audit trails.
- Simplified collaboration between developers and operations teams.
- Easier rollbacks and disaster recovery.
- Disadvantages of GitOps:
- Requires a cultural shift and adoption of new tools and processes.
- Initial setup can be complex.
- Requires expertise in Git and related technologies.
- Potential for increased complexity in the short term.
Core Components of GitOps
GitOps relies on a specific set of tools and practices to manage infrastructure and application deployments. These core components work together to provide a declarative, version-controlled, and automated approach to operations. Understanding these components is crucial for grasping the full potential of GitOps.
Essential Tools and Technologies
Several tools and technologies are integral to implementing GitOps. These tools facilitate the key principles of declarative configuration, version control, and continuous deployment.
- Git Repository: At the heart of GitOps is a Git repository, such as GitHub, GitLab, or Bitbucket. This repository stores the desired state of the infrastructure and applications, represented as code (YAML, JSON, etc.).
- Kubernetes (or other Container Orchestration): Kubernetes is a popular choice for container orchestration, providing the runtime environment where applications are deployed and managed. Other orchestration platforms can also be used.
- Deployment Tools (Operators, Controllers, Agents): These tools automate the process of comparing the desired state in Git with the actual state of the infrastructure. They detect discrepancies and apply the necessary changes to reconcile the two. Examples include:
- Operators: Kubernetes Operators extend the Kubernetes API to manage complex applications. They automate tasks like deployment, scaling, and updates.
- Controllers: Controllers continuously monitor the state of Kubernetes resources and take actions to maintain the desired state.
- Agents: Agents run within the cluster and pull configuration changes from the Git repository, then apply those changes.
- CI/CD Pipelines: Continuous Integration and Continuous Delivery (CI/CD) pipelines automate the building, testing, and deployment of applications. These pipelines are triggered by changes in the Git repository.
- Monitoring and Observability Tools: These tools provide visibility into the health and performance of the infrastructure and applications. They allow for monitoring and alerting, ensuring that any issues are quickly identified and addressed. Examples include Prometheus, Grafana, and the Elastic Stack.
Git as the Single Source of Truth
Git serves as the single source of truth in GitOps. All desired states for infrastructure and applications are defined and stored in Git repositories. This approach offers several advantages.
- Version Control: Every change to the infrastructure or application configuration is tracked, providing a complete history and the ability to revert to previous states.
- Auditability: All changes are auditable, allowing for easy tracking of who made changes and when.
- Collaboration: Git enables collaborative workflows, allowing teams to work together on infrastructure and application code.
- Automation: Changes in the Git repository trigger automated deployments and updates, ensuring consistency and efficiency.
Diagram of GitOps Interaction
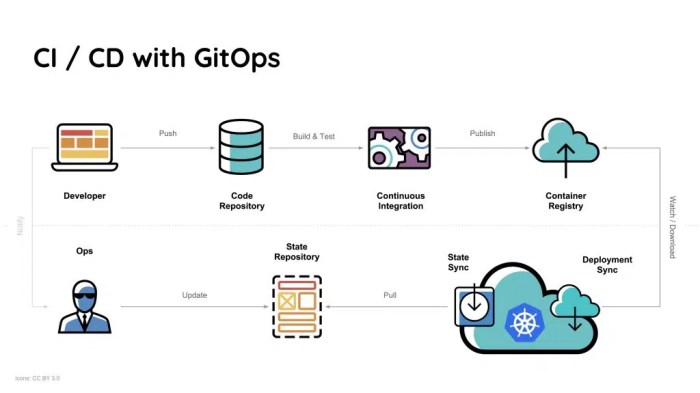
The following diagram illustrates the interaction between Git, infrastructure, and applications within a GitOps workflow.
Diagram Description: The diagram depicts a cyclical flow. The starting point is a Git repository, which stores the desired state configuration (YAML, etc.). An automated process, such as a CI/CD pipeline, triggers when changes are committed to the Git repository. The pipeline builds and validates the application code and then updates the configuration in the Git repository if needed.
A deployment tool (e.g., an Operator or Controller) continuously monitors the Git repository for changes. When changes are detected, the deployment tool applies them to the infrastructure and applications running within a container orchestration platform, such as Kubernetes. Monitoring and observability tools provide feedback on the state of the infrastructure and applications. This information can be used to refine the configuration in the Git repository, completing the cycle.
Arrows indicate the flow of information and actions between the components.
The GitOps Workflow
The GitOps workflow streamlines application deployment and management by treating infrastructure and application configurations as code, stored in a Git repository. This approach promotes automation, version control, and collaboration, resulting in more reliable and efficient deployments. The following sections detail the typical steps involved in a GitOps workflow and provide a practical example.
Typical Steps in a GitOps Workflow
The GitOps workflow typically involves a series of automated steps that ensure consistency and repeatability in application deployments. This process minimizes manual intervention and reduces the risk of human error.
- Code Commit and Push: Developers commit changes to the application code and push them to the designated Git repository. This triggers the GitOps process.
- Configuration Update: Alongside code changes, developers also update the configuration files (e.g., Kubernetes manifests, Helm charts) that define the desired state of the application and infrastructure. These configuration files are also committed and pushed to the Git repository.
- Reconciliation: A GitOps operator or agent, running within the target environment (e.g., a Kubernetes cluster), continuously monitors the Git repository for changes. When a new commit is detected, the operator compares the desired state (defined in the Git repository) with the actual state of the environment.
- Deployment: If a difference is detected between the desired and actual state, the GitOps operator automatically applies the necessary changes to the environment to bring it into alignment with the configuration in Git. This typically involves deploying new versions of applications, updating configurations, or scaling resources.
- Monitoring and Feedback: The GitOps operator also monitors the environment to ensure that the application is running as expected. It provides feedback on the status of the deployment and any errors that may have occurred. This feedback loop allows for continuous improvement and faster issue resolution.
Deploying an Application Using GitOps: A Step-by-Step Procedure
This section presents a practical, step-by-step procedure for deploying an application using GitOps, illustrating the key elements of the process. This example utilizes Kubernetes, but the principles apply to other environments.
- Define the Application: Create a Kubernetes deployment manifest (e.g., a YAML file) that describes the desired state of the application, including container images, resource requests, and other configurations. For instance:
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-app-deployment
spec:
replicas: 2
selector:
matchLabels:
app: my-app
template:
metadata:
labels:
app: my-app
spec:
containers:
-name: my-app-container
image: your-docker-registry/my-app:v1.0
ports:
-containerPort: 8080This manifest defines a deployment that runs two replicas of a container image called `your-docker-registry/my-app:v1.0`.
- Store the Configuration in Git: Commit the Kubernetes manifest to a Git repository. The repository acts as the single source of truth for the application’s desired state.
- Configure the GitOps Operator: Install and configure a GitOps operator (e.g., Argo CD, Flux) within the Kubernetes cluster. The operator is responsible for monitoring the Git repository and reconciling the desired state with the actual state.
- Define the Application in the Operator: Configure the GitOps operator to monitor the Git repository and deploy the application based on the configuration files stored there. This typically involves specifying the repository URL, the path to the configuration files, and the target namespace. For example, in Argo CD, this is achieved by creating an `Application` resource that points to the Git repository and defines the desired deployment target.
- Push Changes and Observe Deployment: When a change is made to the Kubernetes manifest in the Git repository (e.g., updating the container image version), the GitOps operator detects the change and automatically applies it to the Kubernetes cluster. The operator then ensures the cluster reflects the new desired state. The operator’s logs provide visibility into the reconciliation process.
- Monitor the Application: Monitor the deployed application using Kubernetes tools (e.g., `kubectl`) and the GitOps operator’s dashboard. This monitoring ensures that the application is running as expected and that any issues are promptly identified and addressed.
Propagation of Changes and Automation
Changes are propagated through the system in a fully automated manner, which is a core characteristic of GitOps. The following details the process.
- Developer Commits Configuration Changes: A developer commits changes to the application’s configuration files (e.g., a new version of a container image in a Kubernetes deployment manifest) and pushes them to the Git repository.
- GitOps Operator Detects Changes: The GitOps operator, continuously monitoring the Git repository, detects the new commit.
- Operator Reconciles the State: The operator compares the desired state (defined in the Git repository) with the actual state of the environment (e.g., the running Kubernetes cluster).
- Automation of Deployment: If the actual state differs from the desired state, the operator automatically applies the necessary changes to the environment. For example, if the container image version has been updated, the operator will initiate a rolling update of the application’s pods.
- Continuous Feedback Loop: The GitOps operator provides continuous feedback on the deployment status. This feedback loop enables rapid identification and resolution of issues, which improves the reliability of the system.
Benefits of Implementing GitOps
Implementing GitOps offers a multitude of advantages, transforming how organizations manage and deploy their applications. This approach fosters greater efficiency, reliability, and collaboration within development and operations teams. The benefits extend beyond technical improvements, impacting business agility and the ability to respond rapidly to market demands.
Improved Reliability and Stability
GitOps inherently improves the reliability and stability of deployments through several mechanisms.
- Version Control: All configurations are stored in Git, enabling versioning and audit trails. This allows for easy rollback to previous states if issues arise, minimizing downtime and impact.
- Immutable Infrastructure: GitOps often encourages the use of immutable infrastructure, where changes are made by deploying new versions rather than modifying existing ones. This eliminates configuration drift and reduces the risk of unexpected behavior.
- Declarative Configuration: Infrastructure and application states are defined declaratively in Git. This makes it easier to understand and reproduce environments consistently, reducing the likelihood of errors.
- Automated Reconciliation: GitOps tools continuously monitor the live state of the system and automatically reconcile it with the desired state defined in Git. This ensures that the environment always reflects the intended configuration.
Enhanced Collaboration and Reduced Errors
GitOps streamlines collaboration and reduces errors by centralizing configuration management and promoting a shared understanding of the system’s state.
- Centralized Configuration: Git serves as the single source of truth for all configurations, making it easy for teams to understand the current state of the system.
- Simplified Collaboration: Developers and operations teams can collaborate more effectively using Git’s familiar tools and workflows, such as pull requests and code reviews.
- Reduced Human Error: Automation minimizes the need for manual intervention, reducing the potential for human error during deployments and configuration changes.
- Increased Observability: GitOps provides a clear audit trail of all changes, making it easier to track down the root cause of issues and improve overall system observability.
Real-World Case Studies
Several organizations have successfully adopted GitOps, realizing significant benefits. These case studies highlight the tangible impact of GitOps across various industries.
- Weaveworks: As a pioneer in GitOps, Weaveworks has implemented GitOps for its own infrastructure and for its clients. Weaveworks experienced a significant reduction in deployment time and improved stability. Their use of GitOps principles has enabled them to achieve faster release cycles and increased operational efficiency. For instance, by automating the reconciliation process, they have reduced the time spent on manual configuration changes by 80%.
- Intuit: Intuit, a financial software company, has adopted GitOps to manage its Kubernetes deployments. By embracing GitOps, Intuit has improved its deployment frequency and reliability. They were able to reduce the time to deploy new features from weeks to hours. The adoption of GitOps principles, including declarative configuration and automated reconciliation, has significantly enhanced their ability to manage complex Kubernetes environments.
- Adidas: Adidas has used GitOps to manage its cloud infrastructure and applications. This has resulted in faster deployments and reduced infrastructure costs. They have been able to standardize their infrastructure across different environments. This has improved the consistency and reliability of their deployments, as well as significantly decreased infrastructure management costs by up to 30%.
GitOps and Infrastructure as Code (IaC)
GitOps and Infrastructure as Code (IaC) are closely intertwined, forming a powerful combination for modern software delivery. IaC provides the foundation for defining and managing infrastructure in a declarative manner, while GitOps leverages this to automate infrastructure changes and ensure consistent state management. This synergy enables teams to treat infrastructure like application code, versioning it, and automating its deployment and management.
Relationship Between GitOps and IaC
The relationship between GitOps and IaC is symbiotic. IaC provides the “what” – the desired state of the infrastructure, described in code. GitOps provides the “how” – the process of applying that desired state, managing changes, and ensuring that the actual infrastructure matches the declared state. IaC tools like Terraform, Ansible, and others generate the configuration files, while GitOps platforms use Git as the source of truth to deploy and manage these configurations.
This approach allows for version control, auditability, and automation of infrastructure changes, similar to application code deployments.
Comparison of IaC Tools in GitOps
Several IaC tools are commonly used within a GitOps framework, each with its strengths and weaknesses. The choice of tool often depends on the specific infrastructure requirements and team preferences.
- Terraform: Terraform, developed by HashiCorp, is a popular IaC tool that focuses on infrastructure provisioning. It uses a declarative language (HashiCorp Configuration Language or HCL) to define infrastructure resources.
- Strengths: Terraform excels at provisioning infrastructure across multiple cloud providers (AWS, Azure, Google Cloud, etc.) and on-premise environments. It offers a rich ecosystem of providers and a strong community. Terraform’s state management is a key feature, allowing it to track the current state of infrastructure and make intelligent changes.
- Considerations: Terraform can sometimes be slower for iterative changes compared to configuration management tools. The HCL language has a learning curve, though it is relatively straightforward.
- Use Case Example: Deploying and managing virtual machines, networks, and storage across different cloud platforms.
- Ansible: Ansible, developed by Red Hat, is a configuration management and orchestration tool. It uses a declarative language (YAML) to define configurations and playbooks.
- Strengths: Ansible is known for its simplicity and ease of use. It’s agentless, meaning it doesn’t require any software to be installed on the target servers. Ansible is well-suited for configuration management, application deployment, and orchestration tasks.
- Considerations: While Ansible can provision infrastructure, it’s not as strong as Terraform in this area. Its primary focus is on configuration management and orchestration.
- Use Case Example: Configuring servers, deploying applications, and managing software packages.
- Other Tools: Other IaC tools like Pulumi (supports multiple programming languages), Chef, and Puppet are also used in GitOps.
IaC Enables Declarative Infrastructure Management
IaC is fundamental to enabling declarative infrastructure management within a GitOps framework. By defining infrastructure as code, teams can describe the desired state of their infrastructure, rather than specifying the exact steps to achieve that state.
Declarative infrastructure management means focusing on “what” the infrastructure should look like, not “how” to build it.
This approach offers several advantages:
- Version Control: IaC allows infrastructure definitions to be stored in version control systems like Git, enabling versioning, collaboration, and rollback capabilities.
- Automation: IaC facilitates automation of infrastructure provisioning and management tasks, reducing manual effort and the risk of human error.
- Consistency: IaC ensures that infrastructure is consistently provisioned and configured across environments, reducing configuration drift.
- Reproducibility: IaC makes it easy to reproduce infrastructure environments, which is essential for testing, development, and disaster recovery.
GitOps platforms use the IaC definitions stored in Git as the source of truth. When changes are made to the IaC code, the GitOps platform automatically detects these changes and applies them to the infrastructure, ensuring that the actual state of the infrastructure matches the desired state defined in the IaC code. This continuous reconciliation loop is a core principle of GitOps, and IaC is the essential component that makes it possible.
Security Considerations in GitOps
GitOps, while offering significant benefits in terms of automation and efficiency, necessitates careful consideration of security. The declarative nature of GitOps, where the desired state of the system is defined in code, introduces new attack vectors and requires robust security practices to protect against unauthorized access, data breaches, and other vulnerabilities. Implementing these security best practices is crucial for realizing the full potential of GitOps while mitigating its inherent risks.
Security Best Practices for Implementing GitOps
Implementing robust security practices is paramount when adopting GitOps. Several key areas require careful attention to ensure the integrity and confidentiality of your infrastructure and applications.
- Secure Git Repository Access: The Git repository is the single source of truth in GitOps. Therefore, it’s essential to secure access to it. Implement strong authentication mechanisms, such as multi-factor authentication (MFA), to verify user identities. Regularly review and manage access permissions, ensuring that only authorized personnel have the necessary privileges. Consider using service accounts with limited permissions for automated processes.
Regularly audit access logs to detect and respond to any suspicious activity.
- Secrets Management: Never store secrets (passwords, API keys, etc.) directly in the Git repository. Use a dedicated secrets management solution, such as HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault, to securely store and manage sensitive information. Integrate the secrets management system with your GitOps workflow, allowing applications to retrieve secrets at runtime. Implement regular rotation of secrets to minimize the impact of potential breaches.
- Image Scanning and Vulnerability Management: Container images are a critical component of modern applications. Scan container images for vulnerabilities before deploying them to production. Use tools like Trivy, Clair, or Anchore to automatically scan images for known vulnerabilities. Integrate image scanning into your CI/CD pipeline to prevent vulnerable images from being deployed. Regularly update base images and rebuild container images to patch vulnerabilities.
- Network Security: Implement network segmentation to isolate different components of your infrastructure. Use firewalls and network policies to restrict communication between services and prevent unauthorized access. Employ a zero-trust network model, where all access requests are verified, regardless of their origin. Regularly monitor network traffic for suspicious activity.
- Auditing and Logging: Implement comprehensive auditing and logging to track all changes to your infrastructure and applications. Log all Git repository events, including commits, merges, and permission changes. Capture all events related to the deployment process, including deployments, rollbacks, and configuration changes. Centralize logs in a security information and event management (SIEM) system to facilitate analysis and incident response.
- Regular Security Audits: Conduct regular security audits to assess the effectiveness of your security controls and identify potential vulnerabilities. Perform penetration testing to simulate real-world attacks and identify weaknesses in your systems. Regularly review and update your security policies and procedures to reflect evolving threats and best practices.
How GitOps Can Improve Security Posture
GitOps, when implemented correctly, can significantly enhance an organization’s security posture. The declarative nature of GitOps, coupled with its focus on automation and auditability, provides several advantages over traditional operational approaches.
- Improved Access Control: GitOps allows for fine-grained access control through the use of Git repository permissions. You can define who can make changes to infrastructure and application configurations, and restrict access based on roles and responsibilities. This minimizes the risk of unauthorized modifications and reduces the blast radius of potential security incidents. For example, you might grant developers read-only access to production configuration files, while only designated operations personnel have write access.
- Enhanced Auditability: Every change to your infrastructure and applications is tracked in the Git repository. This provides a complete audit trail of all modifications, including who made the change, when it was made, and why. This auditability is invaluable for incident response, compliance, and identifying potential security breaches.
- Immutable Infrastructure: GitOps promotes the concept of immutable infrastructure, where infrastructure components are created and replaced rather than modified in place. This reduces the risk of configuration drift and makes it easier to roll back to a known good state in the event of a security incident. For example, if a vulnerability is discovered in a running application, you can quickly deploy a new, patched version from the Git repository.
- Automation and Consistency: GitOps automates the deployment and management of infrastructure and applications, reducing the potential for human error. Automated deployments are more consistent and less prone to configuration mistakes, which can often be a source of security vulnerabilities.
- Faster Recovery: In the event of a security incident, GitOps allows for faster recovery. You can quickly roll back to a known good state by reverting to a previous commit in the Git repository. This minimizes downtime and reduces the impact of security breaches.
Security Considerations Comparison Table
The following table compares different security considerations in GitOps, highlighting their importance and implications.
| Security Consideration | Description | Impact | Mitigation Strategies |
|---|---|---|---|
| Access Control | Controlling who can access and modify infrastructure and application configurations. | Unauthorized changes, data breaches, system compromise. | Use strong authentication (MFA), role-based access control (RBAC) in Git, and least privilege principles. |
| Secrets Management | Securely storing and managing sensitive information like passwords and API keys. | Exposure of sensitive data, system compromise. | Use dedicated secrets management tools, encrypt secrets in transit and at rest, and regularly rotate secrets. |
| Image Scanning and Vulnerability Management | Identifying and addressing vulnerabilities in container images. | Exploitation of known vulnerabilities, system compromise. | Scan images regularly, integrate scanning into CI/CD pipelines, and promptly patch vulnerabilities. |
| Auditability and Logging | Tracking all changes to infrastructure and applications. | Difficulty in identifying the root cause of security incidents, compliance violations. | Implement comprehensive logging, centralize logs in a SIEM, and regularly review audit trails. |
GitOps and Kubernetes
GitOps is a natural fit for Kubernetes, providing a robust and efficient method for managing containerized applications. Its declarative approach aligns perfectly with Kubernetes’ desired state configuration, enabling automated deployments, rollbacks, and consistent application management. This section explores the synergy between GitOps and Kubernetes, demonstrating how they enhance each other’s capabilities.
GitOps Suited for Kubernetes Deployments
Kubernetes, at its core, is about defining the desired state of your cluster. This includes the applications running, their configurations, and how they interact. GitOps complements this by using Git as the single source of truth for this desired state. This approach provides a number of benefits, including version control, auditability, and automated deployments.
Streamlining Kubernetes Configuration and Management with GitOps
GitOps significantly streamlines Kubernetes configuration and management through several key practices. Using Git for all configurations, deployments become predictable and repeatable. Automation tools continuously monitor the Git repository and reconcile the live cluster state with the desired state defined in Git. This results in faster deployments, simplified rollbacks, and improved overall operational efficiency.Here’s how GitOps streamlines Kubernetes management:
- Declarative Configuration: GitOps promotes the use of declarative configuration files (YAML or JSON) that define the desired state of the Kubernetes cluster. This approach allows for easy management and versioning of configurations.
- Automated Deployments: Continuous integration/continuous deployment (CI/CD) pipelines are integrated with GitOps to automate the deployment of applications. When changes are pushed to the Git repository, the GitOps operators automatically apply the changes to the Kubernetes cluster.
- Rollbacks and Version Control: Git’s version control capabilities enable easy rollbacks to previous versions of the application or configuration if needed. This reduces the risk of deployment errors and provides a safety net for operational issues.
- Auditability and Compliance: All changes to the Kubernetes configuration are tracked in Git, providing a complete audit trail. This is essential for compliance requirements and helps in understanding and troubleshooting any operational issues.
Here’s an example of a Kubernetes configuration managed by GitOps:
This example demonstrates a simple deployment of a web application using Kubernetes manifests stored in a Git repository.
deployment.yaml:
apiVersion: apps/v1 kind: Deployment metadata: name: my-web-app spec: replicas: 3 selector: matchLabels: app: my-web-app template: metadata: labels: app: my-web-app spec: containers: -name: my-web-app-container image: nginx:latest ports: -containerPort: 80service.yaml:
apiVersion: v1 kind: Service metadata: name: my-web-app-service spec: selector: app: my-web-app ports: -protocol: TCP port: 80 targetPort: 80 type: LoadBalancerIn this example, the `deployment.yaml` file defines a deployment for an nginx web server, specifying the number of replicas, the container image, and the port.
The `service.yaml` file defines a service to expose the web application, using a LoadBalancer type to make it accessible from outside the cluster. These YAML files are stored in a Git repository. When changes are made to these files and pushed to the repository, a GitOps operator, such as Argo CD or Flux, automatically detects the changes and applies them to the Kubernetes cluster, ensuring the desired state is maintained.
Challenges and Limitations of GitOps
Implementing GitOps offers significant benefits, but it’s crucial to acknowledge and address the potential challenges. A successful GitOps journey requires careful planning, awareness of potential pitfalls, and a proactive approach to mitigation. Understanding these challenges is essential for a smooth transition and maximizing the advantages of GitOps.
Complexity and Learning Curve
GitOps introduces new concepts and tools, which can lead to a steeper learning curve for teams accustomed to traditional operational practices. The shift from manual configuration to declarative infrastructure management requires a change in mindset and skillset.
- Understanding Declarative Configuration: Teams must become proficient in writing and managing configuration files (e.g., YAML or JSON) that describe the desired state of the system. This involves learning the syntax and semantics of these configuration languages.
- Mastering Git and Version Control: A deep understanding of Git, including branching, merging, and conflict resolution, is paramount. Teams need to be comfortable using Git workflows for all infrastructure and application changes.
- Tooling and Automation: GitOps relies heavily on automation tools (e.g., CI/CD pipelines, reconciliation agents). Teams need to learn how to configure, manage, and troubleshoot these tools. This can involve understanding specific GitOps operators like Argo CD or Flux.
- Overcoming the Learning Curve: Investing in comprehensive training programs, providing hands-on workshops, and creating clear documentation can ease the transition. Start with small, well-defined GitOps projects and gradually expand scope.
Security Concerns
While GitOps enhances security by providing an auditable trail of changes, it also introduces new security considerations that must be addressed. Securing the Git repository and the deployment pipeline are critical.
- Securing the Git Repository: The Git repository becomes the single source of truth, containing sensitive information like application configurations and infrastructure definitions. Implementing strong access controls, such as multi-factor authentication (MFA) and role-based access control (RBAC), is essential. Regularly auditing access logs is also crucial.
- Protecting Secrets: Secrets management is a critical aspect of GitOps security. Secrets should never be stored directly in the Git repository. Instead, use dedicated secrets management solutions (e.g., HashiCorp Vault, AWS Secrets Manager, Azure Key Vault) and integrate them into the GitOps workflow. Ensure proper encryption and access controls for these secrets.
- Supply Chain Security: GitOps pipelines often involve pulling container images and other dependencies from external sources. Implement measures to verify the integrity of these dependencies. Use image scanning tools to detect vulnerabilities and sign container images to ensure their authenticity.
- Compliance and Auditing: GitOps simplifies compliance by providing a clear audit trail of all changes. Ensure that your GitOps implementation aligns with relevant compliance standards. Regularly audit your GitOps configurations and deployments to identify and address any security gaps.
Operational Complexity and Troubleshooting
Managing a GitOps-based system can introduce new operational complexities, particularly when troubleshooting issues. Understanding the entire system, from Git repository to deployed applications, is essential for effective troubleshooting.
- Distributed Systems: GitOps often manages distributed systems, making it more challenging to diagnose and resolve issues that span multiple components and services. Effective monitoring and logging are crucial for gaining visibility into the system’s behavior.
- Debugging Declarative Configurations: Troubleshooting issues related to declarative configurations can be more complex than troubleshooting imperative configurations. Teams need to develop skills in interpreting error messages, analyzing logs, and understanding the reconciliation process.
- Automated Rollbacks: GitOps allows for automated rollbacks to previous versions. However, it’s crucial to test rollback procedures thoroughly and ensure that they function as expected. Implement strategies for quickly identifying and reverting to a known good state.
- Infrastructure Dependencies: Managing infrastructure dependencies (e.g., databases, networking) within a GitOps workflow can be complex. Consider using infrastructure-as-code tools (e.g., Terraform, Ansible) to manage these dependencies and ensure consistency.
Tooling and Ecosystem Maturity
The GitOps ecosystem is rapidly evolving, with new tools and technologies emerging frequently. While this offers a wide range of options, it can also lead to challenges in selecting and integrating the right tools for your specific needs.
- Tool Selection: Choosing the right GitOps tools (e.g., Argo CD, Flux, Jenkins X) depends on your specific requirements, including your existing infrastructure, application architecture, and team skills. Evaluate different tools carefully and consider factors like ease of use, scalability, and community support.
- Tool Integration: Integrating GitOps tools with your existing CI/CD pipelines, monitoring systems, and other operational tools can be challenging. Ensure that the tools you choose integrate well with your existing infrastructure and workflows.
- Ecosystem Maturity: The GitOps ecosystem is still relatively young compared to traditional operational practices. Some tools may have limited features or documentation, and the community support might be less mature. Consider these factors when selecting tools and be prepared to contribute to the community if needed.
- Staying Up-to-Date: The GitOps landscape is constantly changing. Stay informed about new tools, best practices, and emerging trends. Regularly update your tools and configurations to take advantage of the latest features and security patches.
Change Management and Governance
Implementing GitOps requires a well-defined change management process and robust governance policies to ensure consistency, security, and compliance.
- Change Control: Establish clear processes for managing changes to both application code and infrastructure configurations. Implement change request procedures, code reviews, and approval workflows to ensure that all changes are properly vetted.
- Configuration Drift: Configuration drift, where the actual state of the system deviates from the desired state defined in the Git repository, can be a significant challenge. Implement automated checks to detect and remediate configuration drift. Use tools like drift detection and remediation to automatically reconcile the system state with the desired state.
- Role-Based Access Control (RBAC): Implement RBAC to control access to Git repositories and deployment environments. Define clear roles and permissions to limit the impact of potential security breaches.
- Policy Enforcement: Establish policies to enforce security, compliance, and operational best practices. Use policy-as-code tools (e.g., Open Policy Agent) to automate policy enforcement and ensure that all deployments adhere to your organization’s standards.
Final Wrap-Up
In conclusion, GitOps represents a significant shift in how we build and manage software, offering a more efficient, reliable, and secure way to deploy and operate applications. From its core principles to its practical applications, GitOps has revolutionized software development, making it more streamlined, collaborative, and resilient. Embracing GitOps principles can significantly enhance your team’s agility and ability to deliver value, marking a new era of infrastructure management.
FAQs
What is the primary advantage of using GitOps?
The primary advantage of GitOps is its ability to improve reliability and speed up deployments by automating the entire process and maintaining a clear audit trail.
How does GitOps improve security?
GitOps enhances security through version control, auditability, and access control. All changes are tracked, making it easy to identify and revert unauthorized modifications. Moreover, the use of declarative configurations allows for consistent security policies across the entire system.
Is GitOps only for Kubernetes?
While GitOps is particularly well-suited for Kubernetes, it can also be applied to other infrastructure and application environments. It is adaptable to various deployment platforms and cloud providers.
What are the main tools used in a GitOps workflow?
Key tools include Git for version control, a continuous delivery tool (like Argo CD or Flux) for automation, and Infrastructure as Code (IaC) tools (such as Terraform or Ansible) for defining and managing infrastructure.