In the realm of hybrid cloud architectures, the seamless integration of on-premises infrastructure with public cloud services is paramount. This necessitates robust and reliable network connectivity. Direct Connect and ExpressRoute, offered by Amazon Web Services (AWS) and Microsoft Azure respectively, emerge as critical components in achieving this integration. They provide dedicated, private network connections, bypassing the public internet to enhance performance, security, and cost efficiency.
Understanding the intricacies of these services is crucial for organizations aiming to optimize their hybrid cloud deployments.
This discussion will delve into the core functionalities, benefits, use cases, and technical requirements of Direct Connect and ExpressRoute. We will explore their implementation steps, security considerations, monitoring and management strategies, troubleshooting approaches, and cost analysis. By examining these facets, we aim to equip readers with a comprehensive understanding of how these technologies facilitate the creation and maintenance of robust, secure, and cost-effective hybrid cloud environments.
Defining Direct Connect and ExpressRoute
Hybrid cloud architectures, which combine on-premises infrastructure with public cloud services, necessitate robust and reliable network connectivity. This is where dedicated network connections, such as AWS Direct Connect and Microsoft Azure ExpressRoute, become crucial. These services provide a direct, private connection between an organization’s network and the respective cloud provider’s infrastructure, bypassing the public internet. This approach offers enhanced performance, security, and consistency compared to internet-based connections.
AWS Direct Connect: Core Functionality
AWS Direct Connect establishes a private network connection from a customer’s data center, office, or colocation environment to Amazon Web Services (AWS). It allows organizations to bypass the public internet, providing a more stable and predictable network experience.
- Connectivity Options: Direct Connect offers various connectivity options, including:
- Dedicated Connections: Customers can provision dedicated connections with bandwidth options ranging from 1 Gbps to 100 Gbps. These connections are dedicated to a single customer and provide the highest level of performance and isolation.
- Hosted Connections: AWS partners offer hosted connections, which allow customers to share a connection with other customers. This is a more cost-effective option for customers who do not require a dedicated connection. Bandwidth options for hosted connections are typically smaller than dedicated connections.
- Virtual Interfaces (VIFs): Once a physical connection is established, customers create virtual interfaces to access AWS services. There are two primary types of VIFs:
- Public VIFs: Used to access public AWS services like Amazon S3, Amazon CloudFront, and Amazon Route 53.
- Private VIFs: Used to access Amazon Virtual Private Clouds (VPCs). This enables private connectivity to resources within a customer’s VPC, such as EC2 instances, databases, and other applications.
- Benefits: Direct Connect provides several advantages:
- Reduced Network Costs: By bypassing the public internet, Direct Connect can reduce data transfer costs, particularly for large data transfers.
- Increased Bandwidth: Offers higher bandwidth options compared to internet-based connections, leading to improved application performance.
- Consistent Network Performance: Provides a more stable and predictable network experience with reduced latency and jitter.
- Enhanced Security: Establishes a private connection, reducing the risk of data interception and other security threats.
Microsoft Azure ExpressRoute: Hybrid Cloud Role
Microsoft Azure ExpressRoute facilitates private connections to Microsoft Azure services, including virtual machines, storage, and other cloud-based resources. It provides a direct, private connection between an organization’s on-premises network and Microsoft’s global network.
- Connectivity Methods: ExpressRoute supports several connectivity methods:
- Direct Connections: For organizations with high bandwidth requirements, ExpressRoute offers direct connections to Microsoft’s network. These connections are available in various bandwidth options.
- ExpressRoute Partners: Microsoft partners provide connectivity services to Azure. This allows organizations to connect to Azure through their existing network infrastructure.
- Cloud Exchanges: Organizations can connect to Azure through cloud exchanges, which provide a neutral platform for connecting to multiple cloud providers.
- Peering Types: ExpressRoute supports different peering types to access various Azure services:
- Microsoft Peering: Used to access public Azure services, such as Azure Storage and Azure SQL Database.
- Azure Public Peering (Deprecated): Previously used to access public Azure services, but is being phased out.
- Private Peering: Used to connect to virtual networks within Azure, providing private connectivity to virtual machines and other resources.
- Benefits: ExpressRoute provides significant benefits for hybrid cloud deployments:
- Private Connectivity: Provides a dedicated, private connection to Azure, enhancing security and performance.
- Predictable Performance: Offers consistent network performance with lower latency and reduced jitter compared to internet-based connections.
- High Availability: Provides built-in redundancy and high availability through multiple connections and diverse network paths.
- Cost Savings: Can reduce network costs by eliminating the need to transfer data over the public internet.
Similarities and Differences: Network Connectivity
AWS Direct Connect and Microsoft Azure ExpressRoute share fundamental similarities but also exhibit key differences in their implementation and features. Understanding these distinctions is crucial for selecting the appropriate service for a hybrid cloud architecture.
- Similarities:
- Private Connectivity: Both services provide private, dedicated connections to the respective cloud provider’s network, bypassing the public internet.
- Enhanced Performance: Both offer improved network performance, including lower latency and higher bandwidth, compared to internet-based connections.
- Security: Both services enhance security by establishing a private connection, reducing the risk of data interception and other security threats.
- Cost Optimization: Both can reduce data transfer costs, especially for large data transfers.
- Differences:
- Cloud Provider Specific: Direct Connect is exclusively for AWS, while ExpressRoute is for Microsoft Azure.
- Connectivity Options: Direct Connect and ExpressRoute offer different connectivity options, including dedicated connections, hosted connections (Direct Connect), and various partner and exchange options (ExpressRoute).
- Peering Configurations: The way resources are accessed differs. Direct Connect utilizes Virtual Interfaces, while ExpressRoute uses peering types to access various Azure services.
- Service Integration: Direct Connect integrates with AWS services, such as VPCs, S3, and EC2. ExpressRoute integrates with Azure services, such as virtual networks, storage, and virtual machines.
Benefits of Direct Connect and ExpressRoute
Establishing a robust hybrid cloud infrastructure hinges on secure, reliable, and cost-effective network connectivity. Direct Connect and ExpressRoute offer significant advantages over public internet connections, optimizing performance and reducing expenses. These services provide dedicated network connections to cloud providers, bypassing the public internet and improving the overall user experience.
Advantages of AWS Direct Connect
AWS Direct Connect provides several advantages for establishing private network connections to AWS. These advantages center around enhanced performance, increased security, and predictable costs.
- Improved Network Performance: Direct Connect offers lower latency and more consistent performance compared to internet-based connections. This is because data travels over a dedicated network path, avoiding the congestion and variability inherent in the public internet. This dedicated path ensures a more stable and predictable network experience, particularly beneficial for applications requiring real-time responsiveness, such as video conferencing or database replication.
- Enhanced Security: Direct Connect allows for the establishment of private network connections, reducing the attack surface compared to internet-based connections. Data transmitted via Direct Connect is isolated from the public internet, mitigating the risk of eavesdropping, man-in-the-middle attacks, and other security threats. This is particularly important for organizations handling sensitive data or complying with strict regulatory requirements.
- Cost-Effective Data Transfer: While Direct Connect involves initial setup costs, it can lead to significant cost savings on data transfer compared to using the public internet, especially for high-volume data transfers. AWS charges for data transfer
-out* of AWS. With Direct Connect, the data transfer charges are often lower than the standard internet data transfer rates, leading to reduced overall costs, particularly for businesses that frequently move large datasets between their on-premises infrastructure and AWS. - Consistent Network Experience: Direct Connect provides a more consistent and predictable network experience. By establishing a dedicated connection, organizations can minimize the impact of network congestion and other internet-related issues. This consistency is crucial for applications that require a reliable network connection, such as disaster recovery and business continuity.
Benefits of Azure ExpressRoute
Azure ExpressRoute provides several key benefits for establishing private network connections to Azure. These benefits, similar to Direct Connect, focus on performance, security, and cost efficiency.
- Reduced Latency and Increased Throughput: ExpressRoute offers lower latency and higher throughput compared to internet-based connections. This dedicated connection allows data to bypass the public internet, leading to faster data transfer speeds and improved application performance. This is particularly beneficial for applications that require real-time responsiveness, such as virtual desktop infrastructure (VDI) or high-performance computing (HPC) workloads.
- Enhanced Security: ExpressRoute enables the creation of private network connections to Azure, significantly improving security. Data transmitted over ExpressRoute travels over a dedicated network path, isolating it from the public internet and reducing the risk of interception or unauthorized access. This is crucial for organizations that need to protect sensitive data or comply with strict regulatory requirements.
- Cost Optimization: ExpressRoute can provide cost savings on data transfer compared to using the public internet, especially for high-volume data transfers. Azure offers different ExpressRoute pricing tiers, allowing organizations to choose the option that best suits their needs and budget. While there are initial setup costs associated with ExpressRoute, the cost savings on data transfer can be substantial, especially for organizations that frequently move large datasets between their on-premises infrastructure and Azure.
- Guaranteed Bandwidth and Service Level Agreements (SLAs): ExpressRoute offers guaranteed bandwidth and Service Level Agreements (SLAs), providing a more reliable and predictable network experience. Azure guarantees a certain level of performance and uptime, ensuring that applications and services are consistently available. This is particularly important for mission-critical applications that require high availability and reliability.
Cost Savings of Direct Connect and ExpressRoute
The cost savings associated with Direct Connect and ExpressRoute, compared to internet-based connections, are substantial, particularly for organizations with high data transfer volumes. The primary cost drivers include data transfer charges and the avoidance of internet congestion-related performance degradation.
- Reduced Data Transfer Costs: Both Direct Connect and ExpressRoute often offer lower data transfer rates compared to standard internet data transfer. This is because the cloud providers can offer more competitive rates on their dedicated network infrastructure. The savings are especially significant for organizations that frequently transfer large amounts of data between their on-premises infrastructure and the cloud.
- Elimination of Internet Congestion Costs: Internet connections are susceptible to congestion, which can lead to increased latency and reduced throughput. This can negatively impact application performance and user experience. Direct Connect and ExpressRoute bypass the public internet, eliminating the potential for congestion-related performance degradation. This can lead to improved application performance and reduced costs associated with troubleshooting and resolving network issues.
- Predictable Costs: Direct Connect and ExpressRoute offer predictable costs, allowing organizations to accurately forecast their network expenses. This is in contrast to internet-based connections, where costs can fluctuate based on network congestion and other factors. This predictability is particularly valuable for organizations that need to budget their IT expenses carefully.
- Example: Consider a company transferring 10 TB of data per month to AWS. Using standard internet data transfer rates, the cost could be $900. Using Direct Connect, the cost might be $600. While there’s an initial setup fee, the monthly savings accumulate over time, demonstrating the financial advantages of the dedicated connection. The savings depend on the region, the amount of data transferred, and the specific pricing tiers selected.
This illustrates a simplified example; actual costs depend on various factors.
Use Cases for Direct Connect and ExpressRoute
The selection of Direct Connect or ExpressRoute for hybrid cloud deployments hinges on specific requirements, encompassing factors such as bandwidth needs, latency sensitivity, security protocols, and the target cloud provider. Understanding these nuanced differences allows organizations to optimize their network connectivity, enhancing performance and cost-effectiveness. The following sections Artikel distinct use cases for each service, providing guidance for architectural decisions.
Direct Connect Preferred Solutions
Direct Connect is often the preferred solution when high bandwidth, low latency, and predictable performance are paramount, particularly when connecting to providers other than Azure. Several scenarios benefit significantly from Direct Connect’s dedicated network connections.
- High-Bandwidth Data Transfers: Organizations regularly transferring large datasets, such as those involved in scientific research, media production, or disaster recovery, often choose Direct Connect. The dedicated connection guarantees consistent bandwidth, preventing congestion that can occur over the public internet. For example, a genomic research institution transferring terabytes of sequencing data to a hybrid cloud environment might utilize Direct Connect to ensure timely and reliable data transfer.
- Low-Latency Applications: Applications sensitive to latency, such as financial trading platforms or real-time gaming services, can benefit significantly from Direct Connect. The direct connection minimizes network hops, reducing the time data takes to travel between the on-premises environment and the cloud.
- Connecting to Multiple Cloud Providers: When an organization uses multiple cloud providers, Direct Connect can offer a unified approach to network connectivity. This can simplify network management and provide consistent performance across all cloud environments.
- Meeting Compliance Requirements: Certain industries have strict regulatory requirements for data security and privacy. Direct Connect can facilitate compliance by providing a private, isolated network connection that bypasses the public internet.
- Predictable Performance Requirements: When consistent and predictable network performance is critical, Direct Connect provides a stable connection. It is less susceptible to the fluctuations in bandwidth and latency often experienced on the public internet.
ExpressRoute Optimal Choices
ExpressRoute is specifically designed for seamless and private connectivity to Microsoft Azure. Its features are optimized for Azure services, making it the preferred solution in several scenarios.
- Connecting to Azure Services: ExpressRoute provides direct, private connectivity to Azure, offering optimized performance and reliability for Azure services like virtual machines, storage, and databases.
- Hybrid Cloud Deployments with Azure: Organizations building hybrid cloud architectures that leverage Azure services extensively will find ExpressRoute beneficial. It allows for a consistent experience across on-premises and Azure environments.
- Integrating with Azure Virtual WAN: ExpressRoute integrates seamlessly with Azure Virtual WAN, enabling organizations to create a fully managed, global wide-area network (WAN) with integrated connectivity to Azure.
- Cost Optimization for Azure Data Transfer: ExpressRoute offers cost-effective data transfer rates compared to transferring data over the public internet, particularly for high-volume data transfers.
- Simplified Network Management: ExpressRoute provides simplified network management and monitoring tools specifically tailored for Azure connectivity.
Hybrid Cloud Architecture Design: Direct Connect and ExpressRoute
A hybrid cloud architecture can be designed to leverage both Direct Connect and ExpressRoute, optimizing connectivity for different workloads and cloud providers. This architecture allows organizations to take advantage of the benefits of both services.
The following components are key to this design:
- On-Premises Network: This is the existing network infrastructure, including routers, firewalls, and servers.
- Direct Connect Connection: A dedicated connection to a cloud provider other than Azure, providing high bandwidth and low latency.
- ExpressRoute Connection: A dedicated, private connection to Microsoft Azure, enabling secure and reliable access to Azure services.
- Cloud Provider Networks: These are the virtual networks in the cloud environments, such as Amazon Web Services (AWS) or Azure Virtual Networks.
- Routers and Gateways: These components are responsible for routing traffic between the on-premises network, the Direct Connect connection, the ExpressRoute connection, and the cloud provider networks.
- Network Address Translation (NAT): Used to translate private IP addresses to public IP addresses.
- Security Devices: Firewalls and intrusion detection systems (IDS) are implemented to protect the network from unauthorized access and malicious attacks.
Example:
An organization might deploy a hybrid cloud architecture where they use Direct Connect to connect to AWS for their data storage and backup solutions, while using ExpressRoute to connect to Azure for their application workloads. This approach allows them to leverage the strengths of both services, achieving optimal performance and cost-effectiveness.
Data Flow:
Data destined for AWS would traverse the on-premises network, through the Direct Connect connection, and into the AWS network. Data intended for Azure would follow a similar path, but instead utilize the ExpressRoute connection to reach the Azure Virtual Network.
Illustrative Diagram (Conceptual):
Imagine a diagram depicting an on-premises network (rectangle) connected via two lines (representing dedicated connections) to two cloud providers: AWS and Azure (each represented by a cloud icon). The line connecting the on-premises network to AWS is labeled “Direct Connect”, and the line to Azure is labeled “ExpressRoute”. Within the on-premises network, a router (represented by a box) directs traffic appropriately based on destination IP addresses.
Security devices (firewalls, represented by boxes) are placed at the edges of the on-premises network and within the cloud networks for protection. Each cloud provider’s network also contains servers and other resources (represented by various icons). This setup allows for secure, high-performance hybrid cloud connectivity, with traffic intelligently routed to the correct destination cloud.
Network Infrastructure Requirements
Establishing a robust hybrid cloud environment using Direct Connect or ExpressRoute necessitates careful consideration of network infrastructure prerequisites. The specific requirements vary depending on the chosen service, but both demand a solid foundation of connectivity and compatibility to ensure optimal performance, security, and reliability. These requirements span across physical and logical network components, and understanding them is crucial for successful implementation.
Network Infrastructure Prerequisites for Direct Connect
Direct Connect, offering dedicated network connections, mandates specific infrastructure to facilitate a secure and reliable connection to the cloud provider. These prerequisites ensure a direct physical link, bypassing the public internet, for improved performance and reduced latency.
- Physical Connectivity: A dedicated physical connection, often a fiber optic cable, is required between your on-premises network and the cloud provider’s Direct Connect location. This necessitates having the necessary cross-connects in a colocation facility or direct fiber runs. The type of fiber optic cable and the required connectors depend on the cloud provider’s specifications and the distance involved. For example, Amazon Web Services (AWS) Direct Connect supports 1 Gbps, 10 Gbps, and 100 Gbps connections.
The specific type of connection must align with the provider’s supported speeds and the distance to the Direct Connect location.
- Router Configuration: A compatible router that supports Border Gateway Protocol (BGP) is essential. This router acts as the gateway for traffic between your on-premises network and the cloud provider. The router must be configured to establish BGP peering sessions with the cloud provider’s edge routers. Proper configuration involves setting up the Autonomous System Number (ASN), IP addresses, and routing policies to ensure proper traffic routing.
- Colocation Facility (Optional, but often necessary): If your on-premises network isn’t directly connected to the cloud provider’s Direct Connect location, you may need to utilize a colocation facility. This facility provides the physical space and infrastructure necessary to host your equipment and establish a cross-connect to the provider. The choice of colocation facility should be based on proximity to the Direct Connect location and the availability of required services.
- Network Address Translation (NAT) (Optional): In scenarios where your on-premises network uses private IP addresses, Network Address Translation (NAT) may be required to translate these private addresses to public IP addresses for communication with the cloud provider. This ensures that traffic can be routed correctly over the Direct Connect connection.
Network Infrastructure Requirements for Setting up ExpressRoute
ExpressRoute, providing a private connection to Microsoft Azure, also has specific infrastructure needs to establish and maintain a reliable connection. These requirements encompass both physical and logical components and ensure a secure and high-performance link to Azure services.
- Physical Connectivity: Similar to Direct Connect, ExpressRoute requires a physical connection to a Microsoft peering location. This connection can be established through a colocation facility or a network service provider (NSP) offering ExpressRoute connectivity. The physical connection can be a dedicated fiber optic cable or a virtual connection provided by the NSP.
- Router Configuration: A router that supports BGP is also essential for ExpressRoute. This router is configured to establish BGP peering sessions with Microsoft’s edge routers. The configuration involves setting up the ASN, IP addresses, and routing policies to facilitate traffic exchange. The router must also support the specific BGP attributes and settings required by Microsoft Azure.
- ExpressRoute Circuit: An ExpressRoute circuit is a logical connection that provides the dedicated link to Azure. This circuit is provisioned through the Azure portal and is associated with a specific bandwidth and service level agreement (SLA). The circuit acts as a dedicated channel for traffic between your on-premises network and Azure.
- Connectivity Provider: You can connect to Azure ExpressRoute via a connectivity provider (e.g., AT&T, Verizon, Equinix). The provider handles the physical connectivity and provides the necessary services to establish the ExpressRoute circuit. The provider’s network infrastructure is crucial for ensuring a reliable and high-performance connection. The choice of provider depends on your geographic location and the services offered.
- Virtual Network (VNet) Integration: ExpressRoute circuits need to be connected to Azure virtual networks (VNets) to enable communication with Azure resources. This integration involves associating the ExpressRoute circuit with the VNet using a gateway. This integration enables private connectivity to Azure resources.
Comparative Table of Network Infrastructure Requirements
The following table provides a comprehensive comparison of the network infrastructure requirements for both Direct Connect and ExpressRoute, categorized by requirement, description, and service.
| Requirement | Description | Direct Connect | ExpressRoute |
|---|---|---|---|
| Physical Connectivity | The physical connection required to link your on-premises network to the cloud provider. | Dedicated fiber optic cable or cross-connect in a colocation facility. | Dedicated fiber optic cable or virtual connection via a connectivity provider. |
| Router Configuration | Configuration of a router to establish BGP peering and route traffic. | Router supporting BGP, configured with ASN, IP addresses, and routing policies. | Router supporting BGP, configured with ASN, IP addresses, and routing policies, specific to Azure. |
| Colocation Facility | The optional facility to host your equipment and establish a cross-connect. | May be required if not directly connected to the cloud provider’s location. | Often utilized to connect to a Microsoft peering location. |
| Network Address Translation (NAT) | The process of translating private IP addresses to public IP addresses. | May be required if your on-premises network uses private IP addresses. | Generally not required, but can be used in specific configurations. |
| ExpressRoute Circuit | The logical connection that provides the dedicated link to Azure. | Not Applicable | A logical circuit provisioned through the Azure portal, associated with a specific bandwidth and SLA. |
| Connectivity Provider | A provider that offers services to connect to the cloud provider. | May be required if not directly connected to the cloud provider’s location. | A network service provider (NSP) or connectivity provider facilitates the connection. |
| Virtual Network (VNet) Integration | The integration of the ExpressRoute circuit with Azure virtual networks. | Not Applicable | Involves associating the ExpressRoute circuit with the VNet using a gateway. |
Implementation Steps: Direct Connect
Setting up AWS Direct Connect or Azure ExpressRoute involves a series of carefully orchestrated steps to establish a dedicated network connection between your on-premises infrastructure and the cloud provider’s resources. This process requires meticulous planning and execution to ensure seamless connectivity and optimal performance.
Setting up Direct Connect: Step-by-Step Guide
The following steps Artikel the process for establishing a Direct Connect connection to AWS. These steps ensure a secure and reliable connection for hybrid cloud environments.
- Planning and Prerequisites: Before initiating the setup, several prerequisites must be met. These include:
- Network Infrastructure: Identify the existing network infrastructure, including routers, firewalls, and network address translation (NAT) configurations. Ensure compatibility with the AWS Direct Connect requirements.
- AWS Account: An active AWS account is essential to proceed with the Direct Connect setup. This account will be used to manage and configure the Direct Connect connection.
- Connectivity Options: Determine the desired connectivity option. This includes choosing a hosted connection, a dedicated connection, or a Direct Connect partner. Hosted connections are managed by partners and are suitable for smaller bandwidth requirements, while dedicated connections provide higher bandwidth and greater control.
- Bandwidth Requirements: Define the required bandwidth based on the expected data transfer volume and application needs. This helps in selecting the appropriate connection type and port speed.
- Location Selection: Choose a Direct Connect location that is geographically closest to your on-premises network to minimize latency.
- Creating a Virtual Private Gateway (VGW) and a Virtual Interface (VIF): This step establishes the logical connection within the AWS environment.
- VGW Creation: Within the AWS console, create a VGW within your AWS Virtual Private Cloud (VPC). This gateway acts as the AWS side of the connection.
- VIF Configuration: Configure a public or private VIF, depending on your network requirements. The VIF provides the logical connection between your network and the VGW. Private VIFs are used when connecting to a VPC, while public VIFs allow access to public AWS services.
- Ordering a Direct Connect Connection: Based on your chosen connectivity option, order the Direct Connect connection.
- Dedicated Connection: If choosing a dedicated connection, select the appropriate port speed (e.g., 1 Gbps or 10 Gbps) and location. This requires coordination with a colocation facility where your network equipment will reside.
- Hosted Connection: If utilizing a hosted connection, work with an AWS Direct Connect partner to establish the connection. The partner will provide the necessary configuration details.
- Configuring Network Devices: Configure your on-premises network devices (e.g., routers) to establish the BGP peering session with AWS.
- BGP Configuration: Configure Border Gateway Protocol (BGP) on your routers to exchange routing information with AWS. This is crucial for routing traffic between your network and AWS.
- ASN and IP Addresses: Configure the Autonomous System Number (ASN) and IP addresses provided by AWS for the BGP peering.
- MTU Configuration: Configure the Maximum Transmission Unit (MTU) on your network devices to match the AWS Direct Connect MTU (typically 1500 or 9001 for jumbo frames).
- Testing and Validation: After configuration, thoroughly test the connection to ensure it functions as expected.
- Connectivity Testing: Verify connectivity by pinging resources within your VPC from your on-premises network.
- Route Propagation: Confirm that routes are being exchanged correctly between your network and AWS.
- Bandwidth Testing: Perform bandwidth tests to validate the connection’s performance and ensure it meets your requirements.
Demonstrating Configuration of Direct Connect Components
Configuring the necessary components for Direct Connect involves setting up resources within both your on-premises network and the AWS cloud environment. The following details the critical elements and their configuration.
- On-Premises Network Configuration: The configuration on the on-premises side involves setting up your network devices to establish a BGP peering session with AWS. This requires configuring the following:
- Router Configuration: Configure your routers with the ASN, IP addresses, and BGP parameters provided by AWS. This ensures proper routing and traffic exchange.
- Firewall Rules: If you have a firewall, create rules to allow traffic to flow between your network and the AWS Direct Connect endpoint.
- MTU Settings: Adjust the MTU settings on your network devices to match the AWS Direct Connect configuration.
- AWS Configuration: Within the AWS console, configure the necessary components to establish the Direct Connect connection:
- VGW Configuration: Create a VGW and attach it to your VPC. The VGW acts as the endpoint for the Direct Connect connection within AWS.
- VIF Configuration: Configure a VIF, either public or private, and associate it with your VGW. This establishes the logical connection between your network and the VGW.
- Route Propagation: Enable route propagation on the VGW to automatically import routes from your on-premises network.
- BGP Peering: BGP peering establishes the dynamic exchange of routing information between your on-premises network and AWS. It ensures that traffic can be routed correctly.
- ASN Configuration: Use the ASN provided by AWS to configure BGP on your on-premises routers.
- BGP Session Establishment: Establish a BGP session with the AWS Direct Connect endpoint using the configured IP addresses.
Illustrating the Direct Connect Setup Process with a Diagram
The following diagram illustrates the setup process for AWS Direct Connect. This visual representation provides a clear understanding of the components involved and the flow of data.
+---------------------+ +---------------------+ +---------------------+ | On-Premises |-----| Network Provider |-----| AWS Direct Connect | | Network | | (Colocation Facility)| | Location | +---------------------+ +---------------------+ +---------------------+ | (Router) | | | +--------------------------+ | | | BGP Peering | | | +--------------------------+ | | | (ASN, IP Addresses) | | | +--------------------------+ | | | | | | (Cross Connect) | | | | | | +------------------------------------------+ | | | | AWS Side | | | | | +---------------------+ +-----------+ | | | | | Virtual Private |----| VGW | | | | | | Gateway (VGW) | +-----------+ | | | | +---------------------+ | (BGP) | | | | | | VIF (Private) |----| Routing | | | | | +---------------------+ +-----------+ | | | +------------------------------------------+ | | | | | | (Data Flow) | | | | +--------------+ | | | | (Traffic) | V V +---------------------+ +---------------------+ | On-Premises | | AWS VPC | | Applications | | Resources | +---------------------+ +---------------------+
The diagram illustrates the following key components and their interactions:
* On-Premises Network: This represents the customer’s existing network infrastructure, including routers, firewalls, and applications. The router is configured for BGP peering.
– Network Provider (Colocation Facility): This represents the colocation facility or network provider that facilitates the physical connection between the on-premises network and the AWS Direct Connect location. This is where the cross-connect is established.
– AWS Direct Connect Location: This is the AWS facility where the Direct Connect connection terminates.
– Virtual Private Gateway (VGW): This is the AWS side of the connection and is attached to the customer’s VPC.
– Virtual Interface (VIF): The VIF (Private) establishes a logical connection between the on-premises network and the VGW. The VIF is associated with the VGW.
– BGP Peering: BGP is used to exchange routing information between the on-premises network and AWS, enabling dynamic routing.
– Data Flow: The diagram shows the flow of traffic from the on-premises network, through the network provider, to the AWS Direct Connect location, and finally to the customer’s VPC resources.
The diagram visually represents the critical steps involved in setting up Direct Connect, including physical connections, logical configurations, and data flow. This visual aid simplifies understanding the complex interactions within the hybrid cloud environment.
Implementation Steps: ExpressRoute
Setting up Azure ExpressRoute involves a series of well-defined steps to establish a private, dedicated network connection between your on-premises infrastructure and Microsoft Azure. This process requires careful planning and configuration of both your local network and the Azure environment. Successful implementation ensures a reliable and high-performance connection, crucial for hybrid cloud deployments.
ExpressRoute Setup Process
The ExpressRoute setup process can be broken down into several key stages, each with specific configuration requirements. This structured approach ensures a smooth and efficient deployment.
- Planning and Preparation: Before initiating the ExpressRoute setup, several preparatory steps are essential. This involves assessing your network infrastructure, identifying the appropriate ExpressRoute connectivity model (e.g., point-to-point Ethernet, any-to-any network), selecting a connectivity provider, and determining the bandwidth requirements based on your projected data transfer needs. Consider factors such as geographical proximity to Azure regions and the availability of providers in your area.
- Ordering and Provisioning: Once the planning phase is complete, the next step involves ordering the ExpressRoute circuit from your selected connectivity provider. This provider will handle the physical provisioning of the connection, which may involve laying fiber optic cables or establishing other necessary network infrastructure. During this phase, you will also configure the circuit’s properties, such as bandwidth and service level agreements (SLAs).
- Creating an ExpressRoute Circuit in Azure: After the circuit is provisioned by the connectivity provider, you will need to create an ExpressRoute circuit within the Azure portal. This involves specifying the circuit’s properties, such as the peering type (Microsoft peering, private peering), the service provider, and the location of the ExpressRoute circuit.
- Configuring Peering: Peering configurations are crucial for establishing the network connectivity between your on-premises network and Azure. You must configure at least one type of peering: Microsoft peering or private peering. Microsoft peering allows you to access Azure services like Office 365 and Azure PaaS services. Private peering allows you to connect to your virtual networks within Azure. Configuration involves defining the IP address ranges, Autonomous System Numbers (ASNs), and routing policies for each peering type.
- Configuring Virtual Network Gateway: For connectivity to your virtual networks, you must create and configure an ExpressRoute virtual network gateway within Azure. This gateway acts as the entry point for the ExpressRoute connection to your virtual network. During configuration, you’ll specify the gateway type (e.g., ExpressRoute), the virtual network, and the connection to the ExpressRoute circuit.
- Connecting the ExpressRoute Circuit to the Virtual Network Gateway: Once the virtual network gateway is created, you need to link it to your ExpressRoute circuit. This establishes the logical connection between your on-premises network and your virtual network within Azure. This involves specifying the ExpressRoute circuit’s authorization key and other relevant parameters.
- Testing and Validation: After the configuration is complete, it is essential to thoroughly test and validate the ExpressRoute connection. This includes verifying network connectivity, testing data transfer speeds, and monitoring the connection’s performance. Tools like ping and traceroute can be used to diagnose connectivity issues, and monitoring tools can provide insights into bandwidth utilization and latency.
Configuration of ExpressRoute Components
Configuring the necessary components for ExpressRoute involves several key tasks within both your on-premises network and the Azure environment. These configurations ensure secure and reliable connectivity.
- On-Premises Network Configuration: This includes configuring your routers and firewalls to support the ExpressRoute connection. This involves setting up Border Gateway Protocol (BGP) peering with the Microsoft Enterprise Edge (MSEE) routers, configuring routing tables, and implementing security policies to protect the connection. The specific configuration steps will depend on the network devices used in your environment.
- Azure Configuration: Within Azure, you must configure the ExpressRoute circuit, peering, and virtual network gateway. This involves setting up IP address spaces, ASNs, and routing policies. You will also need to define the virtual network and the subnets to which the ExpressRoute connection will be routed. The Azure portal or Azure CLI can be used to manage these configurations.
- BGP Peering: BGP is used to exchange routing information between your on-premises network and the Microsoft network. Configuring BGP involves establishing peering sessions with the MSEE routers and exchanging routing prefixes. This ensures that traffic can be routed correctly between your network and Azure.
- Network Security Group (NSG) Configuration: NSGs are used to control inbound and outbound traffic to your virtual network resources. You will need to configure NSG rules to allow traffic from your on-premises network to reach your virtual machines and other resources within Azure. Ensure that the NSG rules are properly configured to allow the necessary ports and protocols.
ExpressRoute Setup Diagram
The following diagram illustrates the ExpressRoute setup process, demonstrating the interaction between the on-premises network, the connectivity provider, and the Azure environment.
+---------------------+ | On-Premises Network | +---------+-----------+ | | (BGP peering, routing) | +---------v-----------+ | Customer Router | +---------+-----------+ | | (Physical Connection) | +----------------v-----------+ | Connectivity Provider Network| +---------+-----------+ | | (Physical Connection) | +----------------v-----------+ +---------------------+ | Microsoft Network |------| Azure Virtual | | (MSEE Routers, ExpressRoute)| | Network (VNet) | +---------+-----------+ | +---------+-----------+ | | | | (BGP peering, routing) | | | | +---------v-----------+ +---------v-----------+ | Azure ExpressRoute | | Azure Virtual | | Circuit | | Network Gateway | +---------------------+ +---------------------+
Diagram Annotations:
- On-Premises Network: Represents your existing local network infrastructure, including routers, firewalls, and other network devices.
- Customer Router: The router on your premises responsible for establishing BGP peering with Microsoft. It manages routing to Azure and on-premises resources.
- Connectivity Provider Network: The network infrastructure provided by your chosen connectivity provider. This provider facilitates the physical connection to Microsoft.
- Microsoft Network (MSEE Routers, ExpressRoute): The Microsoft network infrastructure, including the MSEE routers, which handle the ExpressRoute connection and BGP peering.
- Azure ExpressRoute Circuit: A logical representation of the connection within Azure. It is linked to the physical connection provided by the connectivity provider.
- Azure Virtual Network (VNet): Your virtual network within Azure, where your virtual machines and other resources reside.
- Azure Virtual Network Gateway: The gateway within your Azure virtual network that facilitates the connection to the ExpressRoute circuit. It handles routing and traffic management.
- Physical Connection: The physical connection, such as a fiber optic cable, provided by the connectivity provider, that links your on-premises network to the Microsoft network.
- BGP Peering, Routing: The exchange of routing information between your on-premises router and the MSEE routers, enabling traffic to be routed correctly between your network and Azure.
Security Considerations
The implementation of Direct Connect and ExpressRoute necessitates a robust security posture to protect data in transit and ensure the integrity and confidentiality of hybrid cloud connections. Proper security configurations are crucial to mitigating potential threats and vulnerabilities. Understanding the security measures specific to each service is essential for a secure hybrid cloud architecture.
Security Measures with Direct Connect
Direct Connect, offering a dedicated network connection, allows for granular control over security configurations. This direct connection bypasses the public internet, reducing the attack surface. Several security measures can be implemented to enhance the security posture of Direct Connect connections.
- Physical Security: The physical security of the Direct Connect connection, including the cross-connects and the associated infrastructure, is paramount. Access control, surveillance, and environmental controls within the colocation facility are crucial. This is often managed by the colocation provider, but it’s vital to understand their security protocols.
- Network Segmentation: Implementing network segmentation isolates sensitive workloads from less critical ones. This limits the impact of a security breach. For instance, using Virtual Local Area Networks (VLANs) to separate different types of traffic, such as production, development, and management, enhances security.
- Encryption: Data encryption in transit is essential. This can be achieved using protocols like IPsec (Internet Protocol Security) to encrypt traffic between the on-premises network and the cloud environment. IPsec provides confidentiality, integrity, and authentication for data packets. The specific configuration depends on the requirements of the cloud provider and the on-premises infrastructure.
- Access Control Lists (ACLs): ACLs on network devices, such as routers and firewalls, restrict network traffic based on source and destination IP addresses, ports, and protocols. ACLs provide a basic level of traffic filtering. Properly configured ACLs can prevent unauthorized access to sensitive resources.
- Monitoring and Logging: Continuous monitoring of network traffic and logging of security events are critical for detecting and responding to security incidents. Tools like intrusion detection systems (IDS) and security information and event management (SIEM) systems can be used to analyze logs and identify suspicious activity.
- Regular Security Audits and Assessments: Conducting regular security audits and vulnerability assessments helps identify and address security weaknesses. These assessments should include penetration testing to simulate attacks and evaluate the effectiveness of security controls.
Security Features and Best Practices for ExpressRoute
ExpressRoute, leveraging private network connections through Microsoft’s network of connectivity providers, offers enhanced security features compared to connections over the public internet. These features are designed to provide secure and reliable access to cloud resources. Adhering to best practices is essential for maximizing the security benefits of ExpressRoute.
- Private Connectivity: ExpressRoute connections are private, meaning traffic does not traverse the public internet. This reduces the risk of exposure to internet-based threats, such as denial-of-service attacks and eavesdropping.
- Network Isolation: ExpressRoute provides network isolation, ensuring that traffic is isolated from other customer traffic on the same physical network infrastructure. This is achieved through the use of dedicated circuits.
- Encryption Options: While ExpressRoute itself doesn’t encrypt traffic by default, customers can implement encryption using IPsec to encrypt data in transit between their on-premises network and the cloud environment. This provides an additional layer of security. The encryption is configured at the customer’s end.
- Microsoft Managed Security: Microsoft manages the security of the ExpressRoute infrastructure, including physical security, network security, and operational security. This includes regular security audits and vulnerability assessments. Microsoft implements and maintains robust security measures.
- Routing Policies: Implementing proper routing policies is essential for controlling traffic flow and preventing unauthorized access. Customers can use Border Gateway Protocol (BGP) to exchange routing information between their on-premises network and the cloud environment. Configuring BGP appropriately is crucial.
- Access Control: Access to ExpressRoute circuits and associated resources can be controlled using role-based access control (RBAC) and other access management tools. This allows for granular control over who can manage and access ExpressRoute resources.
- Monitoring and Alerting: Microsoft provides monitoring and alerting capabilities to detect and respond to security incidents. Customers can also integrate their own monitoring and alerting tools to monitor their ExpressRoute connections.
- Compliance Certifications: ExpressRoute is compliant with various industry standards and certifications, such as ISO 27001, SOC 1, and SOC 2. This helps customers meet their own compliance requirements.
Security Protocols and Configurations for Direct Connect and ExpressRoute
Implementing specific security protocols and configurations is vital for securing connections established with Direct Connect and ExpressRoute. These configurations provide the means to establish a secure and reliable connection to cloud resources.
- IPsec Configuration (Direct Connect and ExpressRoute): IPsec is a suite of protocols that provides secure, authenticated, and encrypted communication over IP networks. Properly configuring IPsec is essential for securing data in transit. This involves defining security associations (SAs), which specify the cryptographic algorithms, keys, and other parameters for encrypting and decrypting traffic. Examples of algorithms include AES (Advanced Encryption Standard) for encryption and SHA-256 for hashing.
- Example: IPsec Configuration with Pre-Shared Key: For a basic IPsec configuration, you might use a pre-shared key (PSK) for authentication. The configuration involves setting up the same PSK on both the on-premises firewall and the cloud provider’s VPN gateway. This requires careful management of the PSK.
- Example: IPsec Configuration with Certificates: For a more robust configuration, you can use digital certificates for authentication. This involves obtaining certificates from a trusted certificate authority (CA) and installing them on both the on-premises firewall and the cloud provider’s VPN gateway. This is more secure than using a PSK.
- BGP Configuration (ExpressRoute): BGP is a routing protocol used to exchange routing information between the on-premises network and the cloud environment. Properly configuring BGP is essential for controlling traffic flow and preventing unauthorized access. This involves configuring BGP peering with the cloud provider and defining routing policies to advertise and receive routes.
- Example: BGP Configuration with MD5 Authentication: To secure BGP peering, you can use MD5 authentication. This involves configuring a shared secret key on both the on-premises router and the cloud provider’s router. This helps to prevent unauthorized routers from establishing BGP peering.
- Firewall Rules (Direct Connect and ExpressRoute): Firewall rules are used to control network traffic based on source and destination IP addresses, ports, and protocols. Implementing appropriate firewall rules is essential for preventing unauthorized access to cloud resources. This involves creating rules to allow only necessary traffic and to block all other traffic.
- Example: Firewall Rule to Allow SSH Traffic: To allow SSH (Secure Shell) traffic from a specific IP address to a specific virtual machine in the cloud, you would create a firewall rule that allows traffic on port 22 from that IP address to the virtual machine’s IP address. This is a common configuration.
- Example: Firewall Rule to Block Unnecessary Traffic: To enhance security, you should block all unnecessary traffic. For example, if you are not using FTP, you should block traffic on port 21. This reduces the attack surface.
- Network Security Groups (NSGs) and Security Groups (Cloud Provider Specific): Many cloud providers offer network security groups (NSGs) or security groups to control network traffic to and from virtual machines and other cloud resources. These are like firewall rules. Properly configuring NSGs/Security Groups is essential for protecting cloud resources. The specifics depend on the cloud provider.
- Example: NSG Rule to Allow Web Traffic: To allow web traffic to a web server, you would create an NSG rule that allows traffic on ports 80 and 443 from the internet. This is a basic example.
- Regular Security Audits and Penetration Testing: Conducting regular security audits and penetration testing helps identify and address security weaknesses. These assessments should include testing the effectiveness of IPsec configurations, firewall rules, BGP configurations, and NSG/Security Group rules.
Monitoring and Management
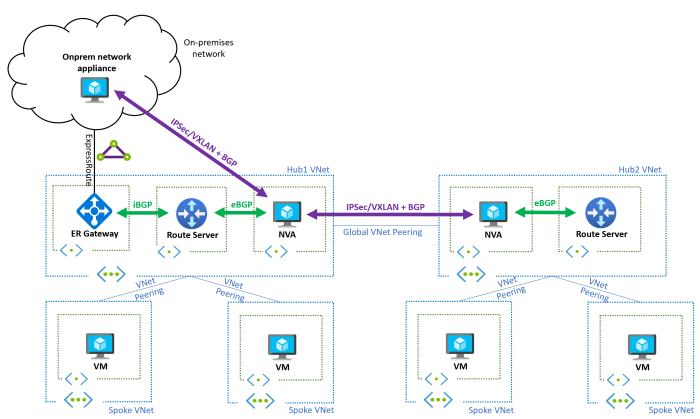
Effective monitoring and management are critical for ensuring the performance, availability, and security of Direct Connect and ExpressRoute connections. These tools provide visibility into network traffic, latency, and connection health, allowing for proactive identification and resolution of issues. Robust management capabilities enable administrators to configure, troubleshoot, and optimize these connections to meet evolving business needs.
Monitoring Direct Connect Connections
Monitoring Direct Connect connections involves assessing the health and performance of the physical connection between the on-premises network and the cloud provider. This typically includes monitoring the Layer 1 and Layer 2 aspects of the connection, as well as tracking the utilization of the associated virtual interfaces.The methods for monitoring Direct Connect connections include:
- Cloud Provider Console: The cloud provider’s console (e.g., AWS Management Console, Azure portal) offers dashboards and metrics that provide insights into the Direct Connect connection. These metrics often include bandwidth utilization, packet loss, and connection status.
- Network Monitoring Tools: Traditional network monitoring tools, such as SolarWinds Network Performance Monitor or PRTG Network Monitor, can be used to monitor the network interfaces on the customer’s side of the connection. These tools can collect data on interface traffic, errors, and discards.
- Simple Network Management Protocol (SNMP): SNMP is a standard protocol used for monitoring network devices. Direct Connect connections often support SNMP, allowing administrators to monitor the connection’s health and performance using SNMP-enabled monitoring tools.
- CloudWatch (AWS): In AWS, CloudWatch can be used to monitor various metrics related to Direct Connect, such as bytes in/out, packets in/out, and connection status. Alarms can be configured to trigger notifications when metrics exceed predefined thresholds.
- Azure Monitor (Azure): In Azure, Azure Monitor provides similar monitoring capabilities for ExpressRoute connections, which can also be leveraged to monitor the virtual interfaces associated with Direct Connect, if applicable.
Managing ExpressRoute Connections
Managing ExpressRoute connections involves configuring and maintaining the virtual circuits, peering relationships, and associated routing configurations. Effective management ensures optimal performance, security, and availability of the connection.Management tasks for ExpressRoute connections encompass:
- Virtual Circuit Configuration: This includes creating, modifying, and deleting virtual circuits, which are logical connections over the ExpressRoute circuit. This is typically done through the cloud provider’s portal.
- Peering Configuration: Establishing and managing peering relationships with the cloud provider’s edge routers. This involves configuring Border Gateway Protocol (BGP) sessions to exchange routing information.
- Routing Configuration: Configuring routing tables and policies to ensure traffic is routed correctly between the on-premises network and the cloud. This includes advertising prefixes and filtering routes.
- Bandwidth Allocation: Adjusting the bandwidth allocated to the ExpressRoute circuit to meet changing traffic demands.
- Service Key Management: Managing the service key used to authenticate the ExpressRoute connection.
- Troubleshooting: Diagnosing and resolving issues related to connectivity, routing, and performance.
Comparison of Monitoring Tools
A comparison of monitoring tools available for Direct Connect and ExpressRoute is presented in the following table. This comparison highlights the key features and capabilities of each tool, enabling administrators to choose the most appropriate solution for their specific needs.
| Feature | Direct Connect | ExpressRoute |
|---|---|---|
| Cloud Provider Console | Provides basic metrics (bandwidth, connection status) | Provides detailed metrics (bandwidth, packet loss, latency, circuit status) |
| Network Monitoring Tools (e.g., SolarWinds, PRTG) | Monitors network interfaces, traffic, and errors on the customer side. | Monitors network interfaces, traffic, and errors on the customer side. |
| SNMP Support | Often supported, allowing monitoring of physical interfaces. | Often supported, allowing monitoring of physical interfaces. |
| Cloud-Specific Monitoring Services (e.g., CloudWatch, Azure Monitor) | Provides detailed metrics and alerting for AWS Direct Connect. | Provides detailed metrics, alerting, and diagnostic tools for Azure ExpressRoute. |
| Alerting and Notification | Available through cloud provider consoles and third-party tools. | Available through cloud provider consoles and third-party tools. |
| Logging and Auditing | Logging of connection events and configuration changes. | Comprehensive logging of connection events, configuration changes, and performance metrics. |
Troubleshooting Common Issues
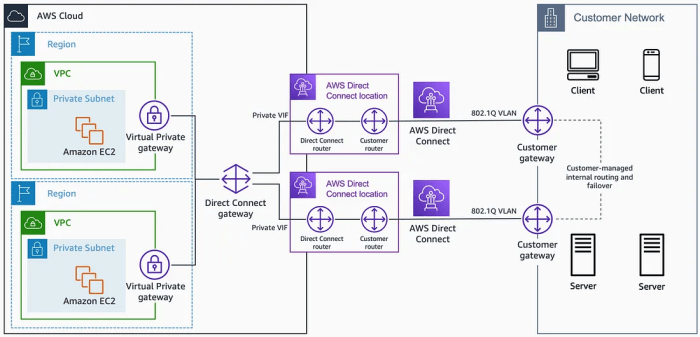
Troubleshooting is a critical aspect of managing Direct Connect and ExpressRoute connections. It involves systematically identifying and resolving issues that can disrupt connectivity, impact performance, and compromise security. Effective troubleshooting requires a thorough understanding of the underlying network infrastructure, configuration settings, and potential points of failure. This section Artikels common problems and their solutions, providing a structured approach to diagnosing and resolving connectivity issues.
Common Issues and Solutions for Direct Connect
Direct Connect, while offering dedicated network connections, can experience various problems. Resolving these issues requires a methodical approach, involving verification of physical connections, network configurations, and peering relationships.
- Physical Layer Issues: Problems at the physical layer often manifest as connectivity failures.
- Issue: Fiber optic cable damage, faulty port configurations, or incorrect cross-connects at the colocation facility.
- Solution: Inspect physical connections, test fiber optic cables using an optical time-domain reflectometer (OTDR) to identify breaks or degradation, and verify port configurations on both the customer’s router and the AWS Direct Connect router. Proper fiber optic cable testing can identify issues, such as excessive attenuation, ensuring a robust physical connection.
- Layer 2 Issues: These issues involve data link layer protocols and configurations.
- Issue: Incorrect VLAN configuration, mismatched MTU settings, or issues with the Address Resolution Protocol (ARP).
- Solution: Verify VLAN tagging on both the customer’s router and the AWS Direct Connect router. Ensure MTU settings are consistent across the entire path, considering the overhead of encapsulation. Use network monitoring tools to diagnose ARP issues, such as duplicate IP addresses or ARP poisoning. A common configuration mistake is the incorrect MTU setting. Direct Connect connections can support a maximum MTU of 9001 bytes, while the default MTU on many devices is 1500 bytes.
Mismatched MTU settings can lead to fragmentation and performance degradation.
- Layer 3 Issues: These problems pertain to network layer protocols and routing.
- Issue: Routing protocol misconfigurations (BGP), incorrect IP address assignments, or network reachability problems.
- Solution: Verify BGP peering sessions are established and that routes are being exchanged correctly. Use tools like `traceroute` and `ping` to diagnose network reachability issues. Examine the routing tables on both the customer’s router and the AWS Direct Connect router to ensure routes to the AWS network are present. For example, if a customer is using BGP to advertise their on-premises network to AWS, a misconfigured Autonomous System Number (ASN) or incorrect route filters can prevent the customer’s network from being reachable from AWS.
- Bandwidth Saturation: Exceeding the provisioned bandwidth can cause performance degradation.
- Issue: Excessive network traffic, leading to packet loss and slow transfer speeds.
- Solution: Monitor network traffic using tools like `iftop` or network performance monitoring (NPM) solutions. Identify and address traffic bottlenecks. Consider upgrading the Direct Connect connection to a higher bandwidth option if necessary. For instance, if a company consistently experiences high network utilization during peak hours, upgrading from a 1 Gbps connection to a 10 Gbps connection can alleviate the bottleneck and improve performance.
- Configuration Errors: Incorrect configurations are a frequent source of problems.
- Issue: Misconfigured VLANs, incorrect BGP settings, or firewall rules blocking traffic.
- Solution: Review and validate all configurations. Use configuration management tools to track changes and ensure consistency. Utilize the AWS Direct Connect console and customer router logs to identify configuration errors. Regularly auditing the configuration settings helps to minimize these errors.
Common Problems and Resolutions for ExpressRoute
ExpressRoute, offering a private connection to Microsoft Azure, encounters distinct issues. The following details the most common problems and their respective resolutions, covering various aspects from physical connectivity to network configurations.
- Physical Connectivity Problems: Issues with the physical connection to the Microsoft network are fundamental.
- Issue: Physical cable damage, port errors, or cross-connect problems at the colocation facility.
- Solution: Check the physical connections between the customer’s network equipment and the ExpressRoute provider’s equipment. Examine the port status on both ends and replace any damaged cables. Contact the ExpressRoute provider to verify the cross-connects are properly configured. Using an OTDR to test the fiber optic cables and ensure that the physical connection is functioning correctly.
- Routing Issues: Incorrect routing configurations can prevent traffic from reaching the Azure network.
- Issue: BGP peering problems, incorrect route advertisements, or routing table inconsistencies.
- Solution: Verify the BGP peering sessions are established and stable. Ensure that the correct prefixes are being advertised to Microsoft. Check the routing tables on both the customer’s router and the Microsoft ExpressRoute router to confirm that routes to Azure are present. Common routing problems include misconfigured ASN or route filters, which can prevent the customer’s on-premises network from being reachable from Azure.
- Bandwidth and Performance Problems: Insufficient bandwidth or network congestion can lead to performance degradation.
- Issue: High network utilization, packet loss, or slow transfer speeds.
- Solution: Monitor network traffic using tools like Azure Network Watcher or third-party network monitoring tools. Identify and address traffic bottlenecks. Consider upgrading the ExpressRoute circuit to a higher bandwidth if necessary. For instance, if a company consistently experiences high network utilization during peak hours, upgrading from a 1 Gbps connection to a 10 Gbps connection can alleviate the bottleneck and improve performance.
- Authentication and Authorization Problems: Issues with authentication can prevent access to Azure resources.
- Issue: Incorrect authentication credentials, misconfigured access control lists (ACLs), or network security group (NSG) rules blocking traffic.
- Solution: Verify the authentication credentials are correct. Review the ACLs and NSG rules to ensure that the appropriate traffic is allowed. Ensure that the correct security policies are applied to the ExpressRoute circuit and associated virtual networks. For example, an incorrect configuration of NSG rules could prevent access to a specific virtual machine in Azure.
- Configuration Errors: Errors in the ExpressRoute configuration can lead to connectivity issues.
- Issue: Incorrect circuit configuration, misconfigured peering, or incorrect IP address assignments.
- Solution: Review the ExpressRoute circuit configuration in the Azure portal. Verify the peering configurations, including the private and Microsoft peering. Check the IP address assignments to ensure they are correct. A common configuration mistake is the incorrect selection of the peering type (private or Microsoft). Incorrectly configured peering types can lead to connectivity problems.
Troubleshooting Steps for Connectivity Problems
A systematic approach to troubleshooting connectivity problems is essential for effective issue resolution. The following steps provide a structured methodology for diagnosing and resolving issues with both Direct Connect and ExpressRoute.
- Verify Basic Connectivity: Start by confirming basic network connectivity.
- Action: Use `ping` and `traceroute` to test reachability between on-premises and cloud resources. Check the physical layer by verifying cable connections and port status.
- Explanation: This initial step helps to quickly identify fundamental connectivity issues, such as physical layer problems or basic network configuration errors.
- Action: Review the configuration of routers, switches, and firewalls. Verify VLAN tagging, MTU settings, and BGP configurations.
- Explanation: Configuration errors are a common cause of connectivity problems. Mismatched settings or incorrect configurations can prevent traffic from flowing correctly.
- Action: Check BGP peering sessions and route advertisements. Examine routing tables to ensure routes to the cloud network are present. Use tools like `show ip bgp summary` and `show ip route`.
- Explanation: Routing problems can prevent traffic from reaching the cloud resources. Incorrect route advertisements or routing table inconsistencies can cause traffic to be dropped or misdirected.
- Action: Use network monitoring tools to analyze traffic patterns, bandwidth utilization, and packet loss. Look for signs of congestion or high latency.
- Explanation: Monitoring network traffic helps to identify performance bottlenecks and potential sources of packet loss or latency. Tools such as `iftop` and `Wireshark` are useful.
- Action: Check system logs, router logs, and cloud service logs for error messages or warnings. Review any alerts generated by monitoring systems.
- Explanation: Logs and alerts often contain valuable information about the root cause of connectivity problems. Error messages can point to specific configuration errors or network issues.
- Action: Test connectivity from different locations or devices. Temporarily disable firewalls or security rules to see if they are blocking traffic.
- Explanation: Isolating the problem helps to identify the specific component or configuration causing the issue. Testing from different locations or devices can help determine if the problem is localized.
- Action: If the problem cannot be resolved, contact the cloud provider’s support team or the ExpressRoute provider for assistance.
- Explanation: Support teams have expertise in resolving complex network issues and can provide guidance and assistance.
Cost Analysis and Optimization
Cost analysis and optimization are crucial considerations when evaluating Direct Connect and ExpressRoute for hybrid cloud deployments. Understanding the pricing models, identifying potential cost drivers, and implementing optimization strategies ensures efficient resource allocation and minimizes operational expenditures. This section delves into the cost elements associated with each service and provides insights into optimizing costs.
Cost Analysis for Direct Connect
Direct Connect pricing typically involves several components. These include port fees, data transfer charges, and potential cross-connect fees. Understanding each of these elements is essential for accurate cost forecasting.
- Port Fees: These are recurring charges for the physical connection to the AWS Direct Connect or Azure Direct Connect location. The fees vary based on the port speed (e.g., 1 Gbps, 10 Gbps) and the region. For example, a 1 Gbps port in a US East region might have a different monthly fee than a 10 Gbps port in a European region.
Higher bandwidth options often incur higher port fees.
- Data Transfer Charges: These charges apply to data transferred
-out* of AWS or Azure over the Direct Connect connection. Data transfer
-into* the cloud provider is generally free. The cost per gigabyte varies depending on the region and the amount of data transferred. Volume discounts may be available for significant data transfer volumes. - Cross-Connect Fees: If the customer’s network equipment is not located at the Direct Connect location, they may need to establish a cross-connect. This involves a physical connection from the customer’s equipment to the Direct Connect port. These fees are typically charged by the colocation provider and can vary depending on the location and the specific cross-connect requirements.
Pricing Structure and Cost Optimization Strategies for ExpressRoute
ExpressRoute pricing is structured around different service tiers and data transfer options, and optimization requires careful consideration of these factors.
- Service Tiers: ExpressRoute offers various service tiers (e.g., Standard, Premium, Local) with different features and pricing. The choice of tier impacts the monthly cost and the features available, such as the number of public and private IP addresses that can be used. Premium tiers often include higher bandwidth and more features, but they also come with higher costs.
- Data Transfer Options: ExpressRoute provides options for data transfer pricing. There are options like metered data (pay-per-GB) and unlimited data (flat fee for a specific bandwidth). The best choice depends on the expected data transfer volume. For predictable, high-volume data transfer, the unlimited option can be more cost-effective. For less predictable, lower-volume data transfer, metered data may be more suitable.
- Cost Optimization Strategies:
- Choose the Right Bandwidth: Analyze data transfer needs to select the appropriate bandwidth. Over-provisioning can lead to unnecessary costs.
- Optimize Data Transfer: Implement data compression and caching techniques to reduce the amount of data transferred.
- Leverage Region-Specific Pricing: Consider regional pricing differences and select the most cost-effective region for the deployment.
- Monitor and Analyze Usage: Regularly monitor data transfer volumes and costs to identify areas for optimization. Cloud provider dashboards and third-party monitoring tools can be used for this purpose.
Comparison of Cost Elements: Direct Connect vs. ExpressRoute
A comparison table provides a structured view of the cost elements involved in Direct Connect and ExpressRoute. This helps in making informed decisions about which service best aligns with specific needs and budget constraints.
| Cost Element | Direct Connect | ExpressRoute | Notes |
|---|---|---|---|
| Port Fees | Yes (Recurring, based on port speed) | Yes (Recurring, based on circuit speed and service tier) | Port speeds (1 Gbps, 10 Gbps, etc.) and service tier (Standard, Premium, etc.) impact costs. |
| Data Transfer (Outbound) | Yes (Pay-per-GB) | Yes (Pay-per-GB or Unlimited, based on data transfer option) | Pricing varies by region and volume. Unlimited data transfer options available for ExpressRoute. |
| Cross-Connect Fees | Yes (If not co-located) | Potentially (If not co-located) | Fees charged by colocation providers. |
| Service Level Agreement (SLA) | Yes | Yes | Both services offer SLAs, which may impact cost through credits in case of downtime. |
| Setup Fees | Potentially (One-time fees may be charged by the colocation provider or the cloud provider) | Potentially (One-time fees may be charged by the cloud provider) | Setup fees, if applicable, are typically associated with initial provisioning. |
Concluding Remarks
In conclusion, Direct Connect and ExpressRoute represent essential tools for organizations leveraging hybrid cloud strategies. They provide the dedicated network connections required to facilitate seamless data transfer, enhanced security, and optimized performance. From understanding the foundational differences to navigating implementation, security protocols, and cost considerations, the knowledge of these services is paramount. As organizations continue to embrace hybrid cloud models, mastering Direct Connect and ExpressRoute becomes increasingly crucial for maximizing the benefits of cloud computing while maintaining control and compliance.
Therefore, these tools represent a cornerstone in modern cloud architecture.
Top FAQs
What is the primary advantage of using Direct Connect or ExpressRoute over a standard internet connection?
The primary advantage lies in improved performance, reduced latency, and enhanced security due to the dedicated, private network connection, which bypasses the public internet and its inherent vulnerabilities.
Are Direct Connect and ExpressRoute suitable for all types of workloads?
While beneficial for many workloads, they are particularly advantageous for those requiring high bandwidth, low latency, and stringent security, such as data migration, disaster recovery, and applications with sensitive data.
What are the typical costs associated with Direct Connect and ExpressRoute?
Costs typically include port fees, data transfer charges, and potential fees for third-party network providers. The specific costs vary depending on the region, bandwidth requirements, and service provider chosen.
How do I choose between Direct Connect and ExpressRoute?
The choice depends on your cloud provider (AWS for Direct Connect, Azure for ExpressRoute), existing network infrastructure, and specific performance, security, and cost requirements. Consider factors such as latency, bandwidth needs, and data transfer volumes.