Embark on a journey into the world of Identity and Access Management (IAM) policies, the cornerstone of secure access control. This guide will delve into the core purpose of IAM policies, demystifying their structure, syntax, and the crucial role they play in safeguarding your resources. We’ll explore the fundamental components of these policies, from permissions and resources to actions, equipping you with the knowledge to navigate this essential aspect of modern security.
We’ll unravel the intricacies of policy writing, emphasizing the principle of least privilege and providing practical examples to illustrate best practices. From understanding the difference between identity-based and resource-based policies to leveraging policy variables for flexible access control, we’ll cover a wide spectrum of topics. Prepare to learn how to test, validate, and refine your policies, and discover advanced features that can bolster your security posture.
Ultimately, this exploration aims to equip you with the skills to create robust and secure IAM policies, ensuring your digital assets are protected.
Defining IAM Policies
IAM policies are the cornerstone of access control within any cloud environment, and understanding their function is critical for maintaining a secure and efficient infrastructure. They dictate who or what can access which resources and what actions they are permitted to perform. This control is fundamental for preventing unauthorized access, data breaches, and operational errors.
Core Purpose of IAM Policies in Access Management
IAM policies primarily serve to regulate and manage access to resources within a cloud platform. They enable organizations to implement the principle of least privilege, granting only the necessary permissions for users and applications to perform their tasks. This approach minimizes the attack surface and reduces the potential impact of security breaches. By carefully defining and applying these policies, administrators can ensure that resources are accessed and utilized in a controlled and secure manner, aligning with compliance requirements and best practices.
Definition of an IAM Policy
An IAM policy is a document that defines one or more permissions. Think of it as a set of rules that specify what actions are allowed or denied on specific resources. It’s a declaration of intent, outlining who is authorized to do what. These policies are attached to identities (users, groups, or roles) or directly to resources to control access.
The ultimate goal is to ensure that only authorized entities can interact with the resources they need, preventing unauthorized access and potential security vulnerabilities.
Fundamental Components of an IAM Policy
Understanding the components of an IAM policy is essential for effective access management. These components work together to define and enforce access controls.
- Permissions: Permissions are the heart of an IAM policy, specifying what actions are allowed or denied. They define the operations a user or service can perform, such as reading, writing, deleting, or modifying resources. Permissions are often expressed as “allow” or “deny” statements. For example, a permission might “allow” a user to “read” an object in an Amazon S3 bucket.
- Resources: Resources are the specific cloud assets to which the permissions apply. This could be an Amazon S3 bucket, an EC2 instance, a database, or any other service component. When defining a policy, you specify which resources the permissions apply to, limiting the scope of access. Specifying the correct resources is crucial for security.
- Actions: Actions define the specific operations that can be performed on a resource. These actions are service-specific and represent the various tasks a user or service can execute. For example, actions for Amazon S3 might include “GetObject,” “PutObject,” or “DeleteObject.” A policy specifies which actions are permitted or denied.
Example: A policy that allows a user to list objects in an S3 bucket might look like this (simplified):
"Version": "2012-10-17",
"Statement": [
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::your-bucket-name"
]
This policy grants the ability to list the contents of the specified S3 bucket.
Policy Structure and Syntax
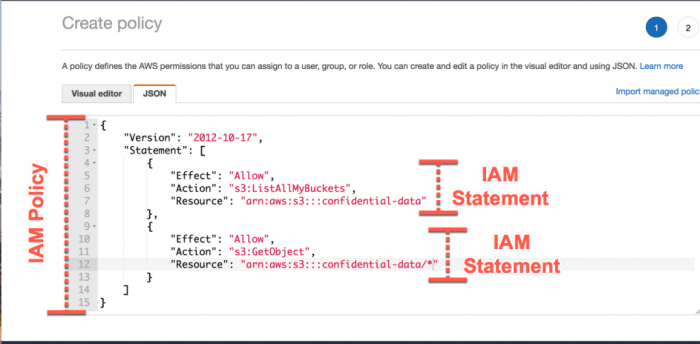
Understanding the structure and syntax of IAM policies is crucial for effectively managing access control within your AWS environment. Properly formatted policies ensure that resources are accessed only by authorized users and services, adhering to the principle of least privilege. This section will delve into the components of an IAM policy and illustrate how they are constructed using JSON.
Standard Structure of an IAM Policy Document
IAM policies are structured as JSON documents. These documents contain key elements that define the permissions granted. The basic structure is consistent, regardless of the specific permissions being defined.The standard structure of an IAM policy document consists of the following core elements:
- Version: Specifies the policy language version. The current version is “2012-10-17.” This element is required.
- Id (Optional): An identifier for the policy. This can be used for easier identification and management of the policy.
- Statement: An array of individual statements that define the permissions. Each statement contains further elements.
Each statement within the “Statement” array contains the following elements:
- Sid (Optional): A statement identifier, similar to the policy ID but for individual statements. It helps with organization and troubleshooting.
- Effect: Specifies whether the statement allows or denies access. Possible values are “Allow” or “Deny.”
- Principal (Optional): Specifies the user, role, or service that the statement applies to. This element is used in resource-based policies (e.g., bucket policies).
- Action: Specifies the API actions that are allowed or denied. This is a list of actions that the policy applies to. Examples include “s3:GetObject” or “ec2:RunInstances.”
- Resource: Specifies the AWS resources that the actions apply to. This can be a specific resource (e.g., an S3 bucket) or a wildcard (*).
- Condition (Optional): Specifies the conditions under which the statement applies. This allows for more granular control based on factors such as time, IP address, or user identity.
JSON Format in Defining IAM Policies
IAM policies are written in JSON (JavaScript Object Notation), a lightweight data-interchange format. JSON’s simple structure makes it easy to read and write, which is why it’s ideal for defining access control policies. Properly formatting the JSON is crucial, as even a minor syntax error can render a policy ineffective.Here’s a breakdown of why JSON is used and some best practices:
- Human-Readable and Machine-Parsable: JSON’s key-value pair structure is easy for humans to read and understand, while also being easily parsed by computers. This makes it straightforward to define and interpret access control rules.
- Structured Data: JSON’s hierarchical structure allows you to organize permissions logically, making it easier to manage complex access control scenarios.
- Consistency: JSON provides a consistent format for defining permissions across different AWS services. This simplifies the learning curve and allows you to apply your knowledge across various services.
- Error Handling: AWS provides validation tools and error messages to help you identify and correct syntax errors in your JSON policies. This ensures that your policies are properly formatted and that access control is enforced as intended.
Example of JSON formatting:“`json “Version”: “2012-10-17”, “Statement”: [ “Sid”: “AllowReadAccessToSpecificBucket”, “Effect”: “Allow”, “Action”: [ “s3:GetObject”, “s3:ListBucket” ], “Resource”: [ “arn:aws:s3:::my-example-bucket”, “arn:aws:s3:::my-example-bucket/*” ] ]“`This example shows a basic policy allowing read access to an S3 bucket and its objects.
The use of `arn:aws:s3:::my-example-bucket` and `arn:aws:s3:::my-example-bucket/*` specifies the bucket and all its objects.
Basic IAM Policy Example Granting Read-Only Access to a Specific Service
Let’s design a basic IAM policy that grants read-only access to Amazon S3. This example demonstrates how to allow a user or role to view objects in an S3 bucket but not modify or delete them.Here’s the JSON policy:“`json “Version”: “2012-10-17”, “Statement”: [ “Sid”: “AllowReadOnlyS3Access”, “Effect”: “Allow”, “Action”: [ “s3:GetObject”, “s3:ListBucket” ], “Resource”: [ “arn:aws:s3:::your-bucket-name”, “arn:aws:s3:::your-bucket-name/*” ] ]“`Explanation:
- Version: Specifies the policy language version.
- Statement: An array containing a single statement.
- Sid: A unique identifier for the statement.
- Effect: Set to “Allow,” granting access.
- Action: Specifies the actions allowed:
s3:GetObject: Allows retrieving objects from the specified S3 bucket.s3:ListBucket: Allows listing the contents of the S3 bucket.
- Resource: Specifies the S3 bucket and its objects.
arn:aws:s3:::your-bucket-name: Represents the specific S3 bucket. Replaceyour-bucket-namewith the actual name of your bucket.arn:aws:s3:::your-bucket-name/*: Represents all objects within the specified S3 bucket.
This policy, when attached to a user or role, will allow them to view the contents of the specified S3 bucket and download the objects. However, they will not be able to upload, modify, or delete any objects, thus adhering to the principle of least privilege. The use of a specific bucket name ensures that access is restricted to the intended resources.
Actions, Resources, and Conditions
IAM policies are built on the core elements of actions, resources, and conditions, which together define what a principal (user, group, or role) is permitted to do within an AWS account. Understanding these elements is crucial for creating effective and secure policies that grant only the necessary access. Properly configuring these elements minimizes the risk of unauthorized access and data breaches.
IAM Actions and Permissions
Actions specify the permitted operations on AWS resources. Each AWS service defines its own set of actions. These actions are the verbs that a principal can perform, such as “read,” “write,” “delete,” or “list.” Permissions are granted by allowing or denying specific actions within a policy.
- Action Granularity: Actions can range from broad permissions (e.g., `s3:*` which allows all actions on S3) to very specific actions (e.g., `s3:GetObject` which allows retrieving a specific object from S3).
- Common Action Prefixes: Actions typically use a prefix that corresponds to the AWS service. For example, actions for Amazon S3 start with `s3:`, actions for EC2 start with `ec2:`, and so on.
- Permission Levels: AWS defines different permission levels, such as “List,” “Read,” “Write,” “Permissions management,” and “Tagging.” Each level represents a set of actions. For example, the “Read” permission level for Amazon S3 typically includes actions like `GetObject` and `GetObjectVersion`.
Resources and Resource Specification
Resources are the specific AWS objects that a principal can access. Each AWS service has its own resource types. These resources can be anything from an S3 bucket to an EC2 instance or a DynamoDB table. Resources are identified by their Amazon Resource Name (ARN).
- ARN Structure: The ARN format is consistent across AWS services, although the specific components will vary. The general format is: `arn:partition:service:region:account-id:resource-type/resource-id`.
- Resource Specification in Policies: You specify resources in the `Resource` element of a policy statement. You can specify a single resource using its ARN, or you can use wildcards (`*`) to match multiple resources.
- `*` Wildcard: Using the wildcard `*` in the resource section means that the policy applies to all resources of the specified type. Use this cautiously, as it can grant excessive permissions.
Conditions and Conditional Access
Conditions allow you to further refine access based on specific criteria. You can restrict access based on factors like the time of day, the IP address of the request, or the tags associated with a resource.
- Condition Keys: AWS provides a set of condition keys that you can use to define conditions. These keys are specific to each service and describe different attributes that can be evaluated.
- Operators: Condition operators, such as `StringEquals`, `DateGreaterThan`, and `IpAddress`, compare the values of the condition keys against the values specified in the policy.
- Example: You could use a condition to allow access to an S3 bucket only from a specific IP address range. This enhances security by limiting access to trusted networks.
Resource Table Examples
Here are examples of resources and how they are specified in an IAM policy.
| Resource Type | ARN Format | Example ARN | Policy Snippet |
|---|---|---|---|
| S3 Bucket | `arn:aws:s3:::bucket-name` | `arn:aws:s3:::my-example-bucket` | `”Resource”: “arn:aws:s3:::my-example-bucket”` |
| EC2 Instance | `arn:aws:ec2:region:account-id:instance/instance-id` | `arn:aws:ec2:us-east-1:123456789012:instance/i-0abcdef1234567890` | `”Resource”: “arn:aws:ec2:*:*:instance/*”` |
| DynamoDB Table | `arn:aws:dynamodb:region:account-id:table/table-name` | `arn:aws:dynamodb:us-east-1:123456789012:table/my-table` | `”Resource”: “arn:aws:dynamodb:*:*:table/my-table”` |
| IAM User | `arn:aws:iam::account-id:user/user-name` | `arn:aws:iam::123456789012:user/Alice` | `”Resource”: “arn:aws:iam::123456789012:user/Alice”` |
Principle of Least Privilege
The Principle of Least Privilege (PoLP) is a cornerstone of secure access management. It dictates that users and applications should be granted only the minimum necessary permissions required to perform their intended functions. This approach significantly reduces the potential attack surface and limits the damage that can result from compromised credentials or vulnerabilities. Applying PoLP is crucial for maintaining a robust security posture within any cloud environment.
Concept of Least Privilege in IAM
In the context of IAM, the principle of least privilege means that IAM policies should be designed to grant only the specific permissions required for a user, group, or role to accomplish their tasks. This involves carefully evaluating the actions, resources, and conditions needed for each function and explicitly denying all other access. Implementing PoLP reduces the risk of unauthorized actions and data breaches.
It is not about blocking access but about providing the correct access.
Applying the Principle of Least Privilege in Policies
Implementing PoLP requires a methodical approach to IAM policy design. Here’s a breakdown of the key steps involved:
- Identify Needs: Determine the precise tasks a user or application needs to perform. Analyze the job functions and associated responsibilities to identify the required access.
- Grant Specific Permissions: Instead of granting broad, wildcard permissions (e.g., `*`), specify the exact actions and resources required. This limits the scope of potential damage.
- Use Conditions: Leverage IAM policy conditions to further restrict access based on factors like time of day, IP address, or Multi-Factor Authentication (MFA) status. This provides granular control and strengthens security.
- Regular Auditing: Regularly review and audit IAM policies to ensure they still align with the principle of least privilege and that permissions remain appropriate for the current needs. Remove any unnecessary or overly permissive access.
- Avoid Excessive Permissions: Refrain from granting permissions that are not directly required for a specific task. If in doubt, err on the side of caution and start with less permissive policies, then add permissions as needed.
Scenario and Secure IAM Policy Design
Consider a scenario where a developer needs to deploy and manage applications within an AWS environment. They require access to deploy code to an Elastic Container Service (ECS) cluster and pull images from an Elastic Container Registry (ECR). The goal is to create an IAM policy adhering to the principle of least privilege.Here’s an example of a secure IAM policy designed for this developer:“`json “Version”: “2012-10-17”, “Statement”: [ “Sid”: “AllowECRImagePull”, “Effect”: “Allow”, “Action”: [ “ecr:GetAuthorizationToken”, “ecr:BatchCheckLayerAvailability”, “ecr:GetDownloadUrlForLayer”, “ecr:BatchGetImage” ], “Resource”: “*” , “Sid”: “AllowECSDeploy”, “Effect”: “Allow”, “Action”: [ “ecs:RegisterTaskDefinition”, “ecs:DeregisterTaskDefinition”, “ecs:UpdateService”, “ecs:RunTask”, “ecs:DescribeServices”, “ecs:DescribeTaskDefinition”, “ecs:ListTaskDefinitions” ], “Resource”: [ “arn:aws:ecs:*:*:task-definition/*”, “arn:aws:ecs:*:*:service/*” ] , “Sid”: “AllowCloudWatchLogs”, “Effect”: “Allow”, “Action”: [ “logs:CreateLogStream”, “logs:PutLogEvents”, “logs:DescribeLogStreams” ], “Resource”: “arn:aws:logs:*:*:log-group:/aws/ecs/*” ]“`The policy adheres to PoLP in several ways:
- Specific Actions: It grants only the necessary actions for ECR image pulling and ECS deployment, such as `ecr:GetAuthorizationToken`, `ecs:RegisterTaskDefinition`, and `ecs:UpdateService`. It does not allow any other actions.
- Resource-Level Permissions: The policy uses resource-level permissions to restrict access to specific resources. For instance, `ecs:UpdateService` is limited to specific ECS services using ARNs. The use of `arn:aws:logs:*:*:log-group:/aws/ecs/*` specifies access to log groups associated with ECS.
- Limited Scope: The policy avoids using broad wildcard actions or resource permissions where possible.
This policy allows the developer to perform their tasks while minimizing the potential for misuse or unauthorized access. If the developer doesn’t need to create new task definitions, the `ecs:RegisterTaskDefinition` permission can be removed. This iterative approach is central to implementing the principle of least privilege.
Best Practices for Secure Policy Writing
Writing secure IAM policies is an ongoing process, not a one-time task. It requires a proactive approach to identify and mitigate potential risks, ensuring that only the necessary permissions are granted and that the overall security posture of your AWS environment is maintained. This section delves into the crucial best practices for crafting robust and secure IAM policies.
Common Security Vulnerabilities in IAM Policies
Several common vulnerabilities can compromise the security of your AWS environment if they exist within your IAM policies. Understanding these weaknesses is the first step toward mitigating them.
- Overly Permissive Policies: These policies grant excessive privileges, potentially allowing attackers to escalate their access or perform actions beyond their intended scope. A classic example is a policy that grants full access to all S3 buckets (
"s3:*") when the user only needs to read from a specific bucket. - Wildcard Usage: While wildcards (
*) can be convenient, excessive use can lead to unintended consequences. For instance, using"s3:*"in the Actions section grants access to all S3 actions, potentially exposing sensitive data. Similarly, using"arn:aws:s3:::*"in the Resources section grants access to all S3 resources, including those you might not intend to allow access to. - Lack of Least Privilege: Failing to adhere to the principle of least privilege is a major security risk. Granting users more permissions than they require increases the attack surface. For example, providing administrative access (
"AdministratorAccess") to users who only need to manage EC2 instances is a significant security flaw. - Trusting External Entities: Improperly configured trust relationships in roles can allow unauthorized access. For example, if a role trusts an external account without proper restrictions, that account could potentially assume the role and gain access to your resources.
- Misconfigured Conditions: Conditions are powerful, but incorrect usage can introduce vulnerabilities. For instance, if a condition is designed to restrict access based on the source IP address but is configured incorrectly, it might not effectively block unauthorized access from specific networks.
- Unmanaged or Unused Policies: Policies that are no longer needed or that are not regularly reviewed can pose a security risk. They may grant access that is no longer necessary, or they may contain outdated configurations that are vulnerable to attack.
Methods to Prevent Overly Permissive IAM Policies
Preventing overly permissive policies is critical to maintaining a strong security posture. This involves a combination of proactive measures, careful policy design, and ongoing monitoring.
- Implement the Principle of Least Privilege: Grant only the minimum necessary permissions required for a user or role to perform their tasks. Regularly review and refine policies to ensure they remain aligned with the principle of least privilege. For instance, if a user only needs to start and stop EC2 instances, the policy should only include
"ec2:StartInstances"and"ec2:StopInstances", not"ec2:*". - Use Specific Actions and Resources: Instead of using wildcards, explicitly specify the actions and resources that a user or role needs access to. This minimizes the scope of potential damage if a policy is compromised. For example, instead of granting access to all S3 buckets (
"arn:aws:s3:::*"), specify the specific bucket(s) and object(s) the user needs to access (e.g.,"arn:aws:s3:::my-bucket/*"). - Utilize Resource-Based Policies: For services like S3 and KMS, use resource-based policies to control access to specific resources. This allows you to define who can access a particular resource and under what conditions. For example, an S3 bucket policy can restrict access to specific IAM users or roles.
- Leverage IAM Policy Simulator: Use the IAM Policy Simulator to test and validate your policies before deploying them. This tool allows you to simulate different scenarios and verify that the policies behave as expected. It helps identify potential issues and ensures that the policies are not overly permissive.
- Employ Policy Templates and Standardization: Use pre-approved policy templates or create a standardized approach for policy creation. This ensures consistency and reduces the likelihood of errors. This could involve defining templates for common use cases, such as granting access to specific AWS services or resources.
- Employ AWS Managed Policies with Caution: While AWS managed policies can be helpful, they often grant broad permissions. Carefully review these policies before attaching them to users or roles. Consider creating custom policies that provide a more granular level of control.
- Implement Tagging and Attribute-Based Access Control (ABAC): Use tags to categorize your AWS resources and implement ABAC to control access based on these tags. This allows for more dynamic and flexible access control. For example, you could tag EC2 instances based on their environment (e.g., “production,” “staging”) and use ABAC to grant access to instances based on their environment tag.
Guidelines for Regular Policy Reviews and Audits
Regularly reviewing and auditing IAM policies is essential to maintain a secure environment. This process helps identify and address potential vulnerabilities, ensuring that policies remain aligned with your security requirements.
- Establish a Regular Review Schedule: Define a schedule for reviewing your IAM policies, such as quarterly or annually. The frequency of reviews should depend on the sensitivity of your data and the complexity of your environment.
- Automate Policy Validation: Use automated tools to validate your policies. These tools can identify potential issues such as overly permissive policies, unused permissions, and compliance violations. AWS provides tools like IAM Access Analyzer to help with this.
- Conduct Manual Reviews: Supplement automated checks with manual reviews. Involve security experts and the teams responsible for managing the resources to review the policies. Manual reviews can identify issues that automated tools might miss, such as unintended consequences of policy changes.
- Analyze Policy Usage: Monitor the usage of IAM policies to identify unused permissions or excessive access. This can help you identify opportunities to refine your policies and apply the principle of least privilege more effectively. AWS CloudTrail can be used to monitor API calls and assess policy usage.
- Document Policy Changes: Maintain a detailed record of all policy changes, including the rationale for the changes and the date they were implemented. This documentation is essential for auditing and troubleshooting purposes.
- Incorporate Security Audits: Integrate IAM policy reviews into your broader security audit program. This ensures that your IAM policies are aligned with your overall security strategy and that any vulnerabilities are addressed promptly.
- Implement a Change Management Process: Establish a formal change management process for IAM policies. This process should include approvals, testing, and rollback procedures to minimize the risk of introducing vulnerabilities.
Identity-Based vs. Resource-Based Policies
IAM policies in AWS come in two primary flavors: identity-based and resource-based. Understanding the distinctions between these policy types is crucial for effectively managing access to your AWS resources. Each type serves a specific purpose and is employed in different scenarios, contributing to a comprehensive security posture.
Comparing Identity-Based and Resource-Based IAM Policies
Identity-based and resource-based policies differ in how they grant permissions. Identity-based policies attach permissions to an IAM user, group, or role. These policies define what actions a principal (user or role) can perform and on which resources. Resource-based policies, on the other hand, are attached directly to a resource, such as an S3 bucket or a KMS key. They specify who (principal) can access the resource and what actions they are allowed to perform.Here’s a comparison table outlining the key differences:
| Feature | Identity-Based Policy | Resource-Based Policy |
|---|---|---|
| Attachment | Attached to IAM users, groups, or roles (principals). | Attached to AWS resources (e.g., S3 buckets, KMS keys). |
| Who is affected? | Determines what a principal can do. | Determines who can access the resource. |
| Use Case | Granting permissions to users and roles to perform actions. | Granting access to a specific resource. |
| Focus | Principal’s permissions. | Resource’s access control. |
Use Cases for Each Policy Type
Identity-based policies are ideal for managing user and role permissions. They enable you to grant fine-grained access control based on the principle of least privilege. Resource-based policies are useful when you need to control access to a specific resource, such as allowing another AWS account to access an S3 bucket.
- Identity-Based Policies: These are commonly used to manage access for users and roles within an AWS account. For example:
- Granting an IAM user permission to launch EC2 instances.
- Allowing an IAM role to read objects from an S3 bucket.
- Granting an IAM user the ability to manage CloudWatch alarms.
- Resource-Based Policies: These are typically used when the access control is centered around a specific resource. Examples include:
- Allowing cross-account access to an S3 bucket. This can be done by attaching a policy to the bucket that specifies which AWS account can access it.
- Defining access to a KMS key. You can use a resource-based policy to grant other AWS accounts or IAM users permission to encrypt or decrypt data using the key.
- Controlling access to an SNS topic, specifying which accounts or IAM users can publish messages to it.
Examples of Each Policy Type
Here are examples illustrating the differences between identity-based and resource-based policies:
- Identity-Based Policy Example: An IAM user needs permission to list objects in an S3 bucket named “my-example-bucket”. An identity-based policy attached to the user would look like this:
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::my-example-bucket" ] ]
This policy allows the user to list the contents of the specified S3 bucket.
The policy is attached to the user’s identity.
- Resource-Based Policy Example: An S3 bucket named “my-example-bucket” needs to allow another AWS account (account ID: 123456789012) to upload objects to it. A resource-based policy attached to the bucket would look like this:
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Principal": "AWS": "arn:aws:iam::123456789012:root" , "Action": [ "s3:PutObject" ], "Resource": [ "arn:aws:s3:::my-example-bucket/*" ] ]
This policy allows the specified AWS account to upload objects to the bucket.
The policy is attached to the S3 bucket (the resource). Note the use of the
Principalelement, which specifies who is granted access.
The key distinction lies in where the policy is applied and what it controls. Identity-based policies control what a user or role
-can* do, while resource-based policies control who
-can* access a resource. In many cases, both policy types are used in conjunction to achieve the desired access control. For instance, a user might need an identity-based policy to allow them to use the `s3:PutObject` action and a resource-based policy on the S3 bucket to allow them to upload objects.
The permissions must align for the action to be successful.
Policy Evaluation Logic
Understanding how AWS IAM policies are evaluated is crucial for predicting access behavior and ensuring your security posture aligns with your intended design. This process determines whether a request to access a resource is allowed or denied, based on the combination of policies applicable to the principal and the resource.
Evaluation Process Overview
The IAM policy evaluation process is a systematic approach AWS uses to determine if a request to access a resource should be permitted. It involves analyzing all relevant policies and applying a set of rules to arrive at a final decision. This process can be broken down into a few key steps.
- Request Received: A user, role, or service (the principal) initiates a request to perform an action on a resource. This request includes information about the principal, the action being requested (e.g., “s3:GetObject”), and the target resource (e.g., an S3 bucket and object).
- Policy Identification: AWS identifies all the relevant policies that apply to the request. This includes:
- Identity-based policies attached to the user or role making the request.
- Resource-based policies attached to the resource being accessed.
- Permissions boundaries (if applicable), which set the maximum permissions that an identity-based policy can grant.
- Service Control Policies (SCPs) in AWS Organizations, which can set permissions limits for all accounts in an organization.
- Policy Evaluation: AWS evaluates each relevant policy to determine if it allows or denies the requested action. The evaluation logic follows the principle of “explicit deny overrides allow.” This means that if any policy explicitly denies the action, the request is denied, regardless of any “allow” statements in other policies.
- Decision: Based on the evaluation of all relevant policies, AWS makes a final decision:
- Allow: If no policies explicitly deny the action, and at least one policy allows the action, the request is allowed.
- Deny: If any policy explicitly denies the action, the request is denied.
- Implicit Deny: If no policy allows the action, the request is implicitly denied. This is the default behavior.
Interaction of Multiple Policies
When multiple policies are in effect, the evaluation process becomes more complex. The interactions between different policy types can lead to different outcomes, highlighting the importance of understanding the evaluation order.
- Deny Takes Precedence: As mentioned, an explicit “Deny” in any policy overrides any “Allow” statements in other policies. This ensures that security restrictions are enforced effectively.
- Multiple Allow Statements: If multiple policies allow the same action, the request is allowed. The presence of multiple “Allow” statements does not conflict; the request is permitted.
- Policy Types and Evaluation Order: AWS evaluates policies in a specific order:
- Service Control Policies (SCPs) – Applied first (if applicable). If the SCP denies, the request is denied.
- Permissions Boundaries – If the permissions boundary denies, the request is denied.
- Resource-based policies – Evaluated next.
- Identity-based policies – Evaluated last.
- Permissions Boundaries Impact: Permissions boundaries restrict the maximum permissions an identity can have. They limit what identity-based policies can allow. If a permissions boundary denies an action, even if the identity-based policy allows it, the request will be denied.
- SCPs in AWS Organizations: SCPs provide centralized control over permissions within an organization. They can be used to set guardrails and restrict the actions that can be performed by users and roles in member accounts.
Flowchart of IAM Policy Evaluation
The following flowchart provides a visual representation of the IAM policy evaluation process.
Flowchart Description: The flowchart depicts the decision-making process AWS uses when a principal requests an action on a resource. It begins with the request and progresses through a series of evaluations, considering various policy types and their respective outcomes.
Flowchart Elements:
- Start: The process begins when a request is received.
- Check SCPs (if applicable): The first step involves checking for Service Control Policies. If an SCP denies the request, the process immediately ends with a “Deny” result. If the SCP allows the request, the process continues.
- Check Permissions Boundary (if applicable): Next, the system checks for a permissions boundary. If the boundary denies the request, the process ends with a “Deny” result. If the boundary allows the request, the process continues.
- Check Resource-Based Policies: The system evaluates resource-based policies. If any resource-based policy explicitly denies the request, the process ends with a “Deny” result. If no resource-based policy denies the request, the process continues.
- Check Identity-Based Policies: The system then evaluates identity-based policies. If any identity-based policy explicitly denies the request, the process ends with a “Deny” result.
- Allow/Deny Decision:
- If the request has not been denied by any policy, and at least one policy allows the action, the request is allowed.
- If the request has not been explicitly allowed by any policy, it is implicitly denied.
- End: The process concludes with either an “Allow” or “Deny” decision.
Using Policy Variables
IAM policy variables provide a powerful mechanism for creating more flexible and manageable access control policies. They allow you to write policies that adapt to the context of the request, such as the user’s identity, the time of day, or the source IP address. This reduces the need to create and maintain a large number of specific policies, simplifying administration and improving security.
How Policy Variables Enhance Access Control
Policy variables act as placeholders that are evaluated at runtime. This means that the values used to determine access are determined at the time the request is made, rather than being hardcoded into the policy. This dynamic behavior is crucial for several reasons:
- Contextual Access: Variables allow policies to consider the context of the request. For example, a policy can grant access to resources only if the request originates from a specific IP address range.
- Reduced Policy Proliferation: Instead of creating multiple policies for different users or groups, a single policy can use variables to apply different rules based on user attributes or other factors.
- Simplified Management: Changes to user attributes or network configurations can be managed centrally, and policies automatically adapt without requiring updates.
Examples of Using Variables in IAM Policies
Here are some examples demonstrating how to use variables in IAM policies:
Example 1: Restricting Access Based on User’s Email Address
This policy allows users to access S3 objects only if the object name starts with their email address.
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::your-bucket-name/$aws:username/*", "Condition": "StringLike": "s3:prefix": [ "$aws:username*" ] ]
Explanation:
$aws:username: This variable represents the user’s IAM username.- The policy allows
s3:GetObjecton resources (objects) in S3, using the username as part of the object’s path. - The
Conditionchecks if the object key (prefix) starts with the user’s username, ensuring that users can only access objects they “own” based on their username.
Example 2: Allowing Access Based on Source IP Address
This policy allows access to a specific EC2 instance only from a defined IP address range.
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": "ec2:DescribeInstances", "Resource": "*", "Condition": "IpAddress": "aws:SourceIp": "192.0.2.0/24" ]
Explanation:
$aws:SourceIp: This variable represents the source IP address of the request.- The policy allows the
ec2:DescribeInstancesaction, which is used to get information about EC2 instances. - The
ConditionusesIpAddressto check if the source IP address falls within the specified CIDR block (192.0.2.0/24).
Use Case: Enhancing Security and Manageability with Policy Variables
Consider a scenario where a company wants to provide access to sensitive data in S3 buckets to its employees, but only when they are connected to the company’s internal network. Using policy variables, they can implement this requirement effectively.
Implementation:
- Define a Policy: Create an IAM policy that grants access to the S3 buckets, but includes a condition that checks the source IP address using the
aws:SourceIpvariable. The condition restricts access to the company’s internal IP address range. - Attach the Policy: Attach this policy to the IAM roles or users who need access to the S3 data.
- Network Configuration: Ensure that the company’s internal network has a defined IP address range.
Benefits:
- Enhanced Security: Access to sensitive data is restricted to the company’s internal network, reducing the risk of data breaches.
- Simplified Management: If the company’s internal network IP address range changes, only the policy needs to be updated. No need to modify individual user permissions.
- Improved Auditability: The policy clearly defines the access control rules, making it easier to audit and monitor access to the data.
Testing and Validation of Policies
Testing and validating IAM policies is crucial to ensure they function as intended and do not inadvertently grant excessive permissions. Rigorous testing minimizes the risk of security breaches and operational disruptions. This section details methods and tools for effectively testing and validating your IAM policies before deployment.
Methods for Testing IAM Policies Before Deployment
Before implementing any IAM policy, thorough testing is essential. This involves simulating various scenarios to verify the policy’s behavior and identify potential issues.
- Unit Testing: Unit testing involves testing individual policy components, such as specific actions or conditions, in isolation. This allows you to verify that each component functions correctly before integrating them into a larger policy.
- Integration Testing: Integration testing focuses on testing how different policy components interact with each other. This helps identify any conflicts or unexpected behavior when multiple components are combined.
- User Simulation: Simulate user access scenarios by assuming different roles and permissions. This helps verify that users can access only the resources and perform only the actions they are authorized to perform.
- Scenario-Based Testing: Create specific scenarios that simulate real-world use cases. This approach tests the policy’s effectiveness in a realistic context. For example, a scenario might involve a user attempting to access a specific S3 bucket or launch an EC2 instance.
- Automated Testing: Automate the testing process using scripts or tools to repeatedly test the policy against various scenarios. This can help identify issues quickly and efficiently.
Tools or Techniques for Validating Policy Syntax and Logic
Several tools and techniques are available to validate the syntax and logic of IAM policies, ensuring they are correctly formatted and behave as expected.
- Policy Validator: Cloud providers, such as AWS, offer built-in policy validators that can check for syntax errors, identify potential security risks, and suggest improvements. These tools analyze the policy’s structure, actions, resources, and conditions.
- IAM Policy Simulator: The IAM Policy Simulator allows you to test the effects of a policy by simulating access attempts. You can input a user, role, or policy and then specify the actions they want to perform on specific resources. The simulator will then determine whether the access is allowed or denied based on the policy’s logic.
- Static Analysis Tools: Utilize static analysis tools that scan the policy code for potential vulnerabilities, such as overly permissive permissions or misconfigurations. These tools can help identify security flaws early in the development process.
- Policy Template Validation: When using policy templates, validate the templates to ensure they meet security requirements and are free from errors before using them to generate policies.
- Code Reviews: Conduct code reviews of IAM policies to have other team members examine the policy’s code. Code reviews can help identify potential issues and ensure the policy adheres to best practices.
Procedures for Simulating Access Attempts to Verify Policy Effectiveness
Simulating access attempts is a crucial part of validating IAM policies. This involves testing how the policy behaves under different access scenarios.
- Identify Test Cases: Define a set of test cases that cover various scenarios, including successful access, denied access, and edge cases. These test cases should be based on the intended use of the policy.
- Use the IAM Policy Simulator: Use the IAM Policy Simulator to simulate access attempts for each test case. Specify the user, role, or policy and the actions they are attempting to perform on specific resources.
- Analyze the Results: Examine the results of the simulation to determine whether access is allowed or denied. Verify that the policy behaves as expected for each test case.
- Review Logs: Review CloudTrail logs to see the actual requests made by users and the outcome of those requests. This can provide additional insights into how the policy is being applied.
- Iterate and Refine: Based on the simulation results, iterate on the policy and refine it to address any issues or unexpected behavior. Repeat the testing process until the policy functions as intended.
Advanced Policy Features
IAM policies can be significantly enhanced by incorporating advanced features that provide granular control over access and strengthen security postures. These features allow for more sophisticated access control mechanisms, enabling administrators to enforce security best practices and adapt to evolving security threats.
Multi-Factor Authentication (MFA) and Session Duration
Implementing MFA and managing session duration are critical components of a robust security strategy. MFA adds an extra layer of protection beyond passwords, while controlling session length minimizes the potential impact of compromised credentials.
- Multi-Factor Authentication (MFA): MFA requires users to provide multiple verification factors to access resources. This typically involves something the user knows (password), something the user has (a mobile device or security key), and/or something the user is (biometric data). Integrating MFA into IAM policies can significantly reduce the risk of unauthorized access, even if an attacker obtains a user’s password. For example, a policy might require MFA for any actions that modify security-sensitive resources.
- Session Duration: Session duration defines the length of time a user’s session remains active. Shorter session durations reduce the window of opportunity for attackers to exploit compromised credentials. Policies can be configured to enforce specific session lengths for different user roles or resource access scenarios.
Conditions for Restricting Access
Conditions within IAM policies provide the flexibility to restrict access based on various factors, including time of day, IP address, and other contextual information. This enables administrators to create highly customized access control rules tailored to specific security requirements.
- Time-Based Restrictions: Access can be restricted to specific times or days. For instance, a policy might allow access to a database only during business hours or prevent access to a production environment outside of a maintenance window.
- IP Address Restrictions: Access can be limited based on the source IP address or IP address range. This is particularly useful for restricting access to internal networks or for allowing access only from trusted locations.
- User Agent Restrictions: Policies can restrict access based on the user agent string, which identifies the client application (e.g., web browser). This can be used to enforce the use of specific browsers or prevent access from outdated or potentially vulnerable applications.
- Context-Specific Restrictions: Conditions can also be used to control access based on other contextual information, such as the user’s geographical location, the type of device being used, or the presence of a specific tag on a resource.
Examples of Policies with Advanced Features
Here are several examples demonstrating how to incorporate advanced features into IAM policies:
- MFA Enforcement: This policy requires MFA for any action that modifies IAM policies.
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": "iam:*", "Resource": "*", "Condition": "BoolIfExists": "aws:MultiFactorAuthPresent": "true" ]In this policy, the `aws:MultiFactorAuthPresent` condition checks if the user has authenticated with MFA. If MFA is not present, the action is denied.
- Time-Based Access Restriction: This policy restricts access to a specific S3 bucket to business hours (9 AM to 5 PM, Monday to Friday).
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": "s3:*", "Resource": "arn:aws:s3:::my-bucket/*", "Condition": "DateGreaterThan": "aws:CurrentTime": "2024-01-01T09:00:00Z" , "DateLessThan": "aws:CurrentTime": "2024-01-01T17:00:00Z" , "StringEquals": "aws:DayOfWeek": ["Monday", "Tuesday", "Wednesday", "Thursday", "Friday"] ]The `DateGreaterThan` and `DateLessThan` conditions restrict access based on the current time, and the `StringEquals` condition restricts access to weekdays.
- IP Address Restriction: This policy allows access to a specific EC2 instance only from a specific IP address range.
"Version": "2012-10-17", "Statement": [ "Effect": "Allow", "Action": "ec2:DescribeInstances", "Resource": "*", "Condition": "IpAddress": "aws:SourceIp": "192.0.2.0/24" ]The `IpAddress` condition restricts access based on the source IP address.
Common IAM Policy Mistakes and How to Avoid Them
Writing effective and secure IAM policies is crucial for maintaining a robust security posture. However, it’s easy to make mistakes that can lead to vulnerabilities, unauthorized access, and data breaches. This section identifies common errors in IAM policy creation and provides practical guidance to avoid them, along with a helpful checklist for review.
Overly Permissive Policies
A frequent error is granting excessive permissions, often by using wildcards or broad statements. This approach, while seemingly convenient, violates the principle of least privilege, potentially exposing resources to unnecessary risks.
- Using Wildcards Excessively: Wildcards, such as `*`, should be used judiciously. Granting access to all actions (`”Action”: “*”`) or all resources (`”Resource”: “*”`) is highly discouraged unless absolutely necessary. For example, allowing a user to manage all objects in all S3 buckets (`”Resource”: “arn:aws:s3:::*/*”`) is overly broad.
- Granting Access to Unnecessary Actions: Carefully evaluate which actions are truly needed for a user or role. Granting permissions like `ec2:Describe*` (allowing description of all EC2 resources) when only a specific action like `ec2:StartInstances` is required increases the attack surface.
- Ignoring Resource-Specific Permissions: When possible, define permissions at the resource level. For instance, instead of allowing access to all S3 buckets, specify access to only the required buckets. This minimizes the impact of a compromised identity.
Neglecting the Principle of Least Privilege
The principle of least privilege dictates that users and roles should only have the minimum permissions required to perform their tasks. Failing to adhere to this principle is a major security flaw.
- Providing More Permissions Than Necessary: Carefully analyze the required tasks and grant only the permissions needed for those tasks. Regularly review and remove unused permissions.
- Defaulting to ‘Allow’ Instead of ‘Deny’: Always consider the impact of granting ‘Allow’ permissions. Where possible, start with a ‘Deny’ all approach and then explicitly allow only the necessary actions and resources.
- Lack of Regular Auditing: Implement a process for regularly reviewing and auditing IAM policies to identify and remediate overly permissive configurations. Consider using automated tools to help with this.
Incorrect Syntax and Formatting
Errors in syntax and formatting can render policies ineffective or, worse, grant unintended access.
- Typos and Incorrect Values: Typos in action names, resource ARNs, or condition keys can lead to unexpected behavior. For example, a typo in the `s3:GetObject` action could prevent access.
- Incorrect Use of JSON: IAM policies are written in JSON. Ensure the syntax is valid, including correct use of commas, colons, and quotation marks. Use a JSON validator to check the policy before deployment.
- Misunderstanding Policy Elements: A thorough understanding of the different policy elements (e.g., `Action`, `Resource`, `Condition`) is essential. Incorrectly defining these elements can lead to security vulnerabilities.
Insufficient Testing and Validation
Failing to adequately test and validate IAM policies before deployment can lead to unforeseen consequences.
- Lack of Testing in a Staging Environment: Always test policies in a non-production environment before applying them to production. This allows you to identify and correct any issues without affecting live systems.
- Insufficient User Testing: Test policies from the perspective of the users or roles they are intended for. Ensure they can perform their required tasks without unnecessary permissions.
- Failure to Use Policy Simulators: Utilize AWS Policy Simulator or similar tools to simulate the effects of a policy before deployment. This can help identify potential issues and ensure the policy behaves as expected.
Ignoring Security Best Practices
Overlooking established security best practices in policy writing can lead to serious security vulnerabilities.
- Not Using MFA: Enforce multi-factor authentication (MFA) for all IAM users with console access. This significantly reduces the risk of unauthorized access.
- Not Rotating Access Keys Regularly: Regularly rotate access keys to minimize the impact of compromised keys.
- Not Monitoring IAM Activity: Implement monitoring and logging for IAM activity to detect and respond to suspicious behavior. Use services like AWS CloudTrail to track API calls.
Checklist for Reviewing IAM Policies
Implementing a consistent review process is crucial for catching mistakes before they become security issues. Use the following checklist when reviewing IAM policies:
- Principle of Least Privilege: Does the policy grant only the minimum necessary permissions?
- Wildcard Usage: Are wildcards used appropriately and sparingly?
- Action Permissions: Are only the required actions permitted?
- Resource-Specific Permissions: Are resources specified as narrowly as possible?
- Syntax and Formatting: Is the JSON syntax valid and free of errors?
- Testing and Validation: Has the policy been tested in a non-production environment? Has user testing been performed?
- Security Best Practices: Does the policy adhere to security best practices (e.g., MFA, key rotation)?
- Regular Review: Is there a schedule for regularly reviewing and updating IAM policies?
- Use of Policy Variables: Are policy variables used appropriately to enhance flexibility and security?
- Compliance with Organizational Standards: Does the policy adhere to your organization’s security policies and compliance requirements?
Final Review
In conclusion, mastering IAM policies is paramount for any organization aiming to secure its digital infrastructure. By understanding the fundamentals, adhering to best practices, and continuously refining your approach, you can effectively control access to your resources and mitigate potential security risks. Remember that secure policy writing is an ongoing process, demanding vigilance, regular reviews, and a commitment to the principle of least privilege.
Embrace these practices, and you’ll be well-equipped to navigate the complexities of IAM and fortify your defenses against evolving threats.
Common Queries
What is the difference between IAM and MFA?
IAM (Identity and Access Management) is the overall framework for managing user identities and their access to resources, while MFA (Multi-Factor Authentication) is a security measure that adds an extra layer of protection by requiring users to provide multiple forms of verification, such as a password and a one-time code from a mobile device.
How often should I review my IAM policies?
IAM policies should be reviewed regularly, ideally at least quarterly or whenever significant changes are made to your infrastructure or user roles. This helps ensure policies remain aligned with your security needs and adapt to evolving threats.
What are some common mistakes to avoid when writing IAM policies?
Common mistakes include granting overly permissive access (e.g., using wildcards excessively), failing to adhere to the principle of least privilege, not regularly reviewing policies, and not testing policies thoroughly before deployment. Avoid these pitfalls by carefully considering each policy’s purpose and continuously validating its effectiveness.