Understanding and quantifying the success of your security program is crucial in today’s dynamic threat landscape. This guide delves into the critical aspects of evaluating your security posture, providing a structured approach to assess performance and ensure alignment with your business objectives. From defining clear goals to implementing continuous improvement strategies, this overview will equip you with the knowledge to make informed decisions and optimize your security investments.
We will explore key performance indicators (KPIs), data collection techniques, and the importance of measuring security awareness and the impact of security controls. We’ll also cover incident response effectiveness, compliance adherence, and the crucial role of reporting and communication. This comprehensive approach will help you not only measure your current security program’s effectiveness but also foster a culture of continuous improvement, ensuring your organization remains resilient against evolving threats.
Defining Security Program Goals and Objectives
Establishing clear goals and objectives is the cornerstone of any successful security program. Without well-defined targets, it’s impossible to measure effectiveness, allocate resources efficiently, or demonstrate the program’s value to the organization. This section focuses on the crucial steps involved in defining, aligning, and maintaining a robust security program that supports overall business success.
Creating SMART Security Program Goals
Developing goals that are SMART (Specific, Measurable, Achievable, Relevant, and Time-bound) ensures clarity and facilitates progress tracking. This approach provides a framework for creating actionable objectives that can be realistically achieved. Here are examples of SMART security program goals:
- Specific: Reduce the number of successful phishing attacks targeting employees.
- Measurable: Decrease the number of successful phishing attacks by 25% within the next six months.
- Achievable: Implement a multi-layered phishing awareness training program and deploy a phishing simulation tool.
- Relevant: Protecting sensitive data and maintaining business continuity.
- Time-bound: Achieve a 25% reduction in successful phishing attacks by December 31st, 2024.
- Specific: Improve the organization’s vulnerability management program.
- Measurable: Reduce the average time to remediate critical vulnerabilities from 60 days to 30 days.
- Achievable: Implement automated vulnerability scanning and patching tools.
- Relevant: Minimize the risk of exploitation by known vulnerabilities.
- Time-bound: Reduce the average time to remediate critical vulnerabilities to 30 days by the end of Q2 2025.
- Specific: Enhance incident response capabilities.
- Measurable: Reduce the mean time to detect (MTTD) a security incident from 48 hours to 24 hours.
- Achievable: Implement a Security Information and Event Management (SIEM) system and improve incident response playbooks.
- Relevant: Minimize the impact of security incidents on business operations.
- Time-bound: Reduce the MTTD to 24 hours by the end of Q4 2024.
Aligning Security Goals with Business Objectives
Security goals must be directly aligned with the organization’s overall business objectives to ensure they contribute to the company’s success. This alignment demonstrates the value of the security program and secures necessary resources. Consider the following examples:
- Business Objective: Increase revenue by expanding into a new market.
- Aligned Security Goal: Ensure data security and compliance with relevant regulations in the new market.
- Action: Conduct a security risk assessment of the new market, implement data encryption, and ensure compliance with data privacy laws.
- Business Objective: Improve customer satisfaction and retention.
- Aligned Security Goal: Protect customer data and prevent data breaches.
- Action: Implement robust access controls, conduct regular security audits, and provide employee training on data privacy best practices.
- Business Objective: Reduce operational costs.
- Aligned Security Goal: Automate security tasks and improve incident response efficiency.
- Action: Implement security automation tools, deploy a SIEM system, and develop incident response playbooks.
Reviewing and Updating Security Program Objectives
Regularly reviewing and updating security program objectives is essential to ensure they remain relevant and effective. This process should be conducted periodically, at least annually, or more frequently if there are significant changes in the threat landscape, business environment, or regulatory requirements.
- Conduct a Security Program Review: Assess the current state of the security program, including its strengths, weaknesses, and areas for improvement.
- Analyze the Threat Landscape: Stay informed about the latest cyber threats, vulnerabilities, and attack trends.
- Review Business Objectives: Ensure that security goals continue to align with the organization’s overall business objectives.
- Update Objectives: Based on the review and analysis, revise or create new SMART security goals.
- Develop an Action Plan: Artikel the specific steps required to achieve the updated security goals, including resource allocation, timelines, and responsibilities.
- Communicate Changes: Inform relevant stakeholders about the updated security goals and action plan.
- Track Progress: Regularly monitor progress towards achieving the security goals and make adjustments as needed.
Identifying Key Performance Indicators (KPIs)
Selecting the right Key Performance Indicators (KPIs) is crucial for evaluating the effectiveness of your security program. KPIs provide measurable values that track progress toward security goals and identify areas needing improvement. Choosing appropriate KPIs involves understanding your program’s objectives, the assets you’re protecting, and the threats you face. This section details how to select, measure, and utilize KPIs for a robust security program evaluation.
Selecting Appropriate KPIs for Different Aspects of a Security Program
Choosing relevant KPIs requires aligning them with specific security goals. For instance, if a goal is to reduce the time to detect and respond to incidents, the KPIs should directly reflect those activities. A thorough understanding of the organization’s risk profile and security priorities is also essential.
- Incident Detection: Measures related to identifying security incidents.
- Incident Response: Metrics for how quickly and effectively incidents are handled.
- Vulnerability Management: Indicators for how vulnerabilities are identified, assessed, and remediated.
- Compliance: Metrics for adhering to regulatory requirements and internal policies.
- Security Awareness: KPIs for evaluating the effectiveness of security training and employee awareness.
To illustrate, consider a financial institution. Their primary goal might be to protect customer data and prevent financial fraud. Relevant KPIs would include the number of successful phishing attempts, the time taken to detect and contain a data breach, and the percentage of systems patched within a specified timeframe. These metrics would directly reflect the institution’s ability to safeguard its assets.
Methods for Measuring KPIs Related to Incident Response
Measuring incident response KPIs involves tracking several key aspects of the incident lifecycle, from detection to recovery. Accurate measurement requires the implementation of robust logging, monitoring, and reporting systems. Analyzing these data points provides valuable insights into the efficiency and effectiveness of the incident response process.
- Mean Time to Detect (MTTD): This KPI measures the average time taken to identify a security incident. It is calculated from the time an incident begins to the time it is detected.
- Mean Time to Respond (MTTR): This KPI represents the average time taken to contain and mitigate a security incident, from detection to containment.
- Mean Time to Resolve (MTTR): This KPI measures the average time taken to fully resolve a security incident, from detection to complete remediation and recovery.
- Number of Incidents: Tracking the total number of security incidents helps assess the overall security posture.
- Incident Severity: Categorizing incidents based on their severity (e.g., critical, high, medium, low) provides insights into the impact of security events.
For example, if an organization aims to reduce its MTTR, it might implement automated incident response tools and improve its incident response playbooks. Analyzing the trend of these KPIs over time reveals whether the implemented measures are improving the response efficiency.
Using KPIs to Track Progress Toward Security Goals
KPIs are not just about measuring; they are essential for tracking progress toward security goals. Regularly reviewing KPIs helps identify trends, evaluate the effectiveness of security controls, and make data-driven decisions. This process involves setting targets, monitoring performance, and adjusting strategies as needed.
| KPI | Goal | Baseline | Target | Current Value | Trend |
|---|---|---|---|---|---|
| Mean Time to Detect (MTTD) | Reduce time to detect incidents | 24 hours | 12 hours | 18 hours | Improving |
| Mean Time to Respond (MTTR) | Reduce time to contain incidents | 8 hours | 4 hours | 6 hours | Improving |
| Vulnerability Patching Rate | Patch vulnerabilities promptly | 70% | 90% | 85% | Improving |
By continuously monitoring these metrics, organizations can proactively address security gaps, allocate resources effectively, and demonstrate the value of their security investments. If, for instance, the “Vulnerability Patching Rate” is consistently below target, it might indicate issues with patching processes, requiring investigation and improvements.
Data Collection and Measurement Techniques
Effectively measuring the effectiveness of a security program hinges on the ability to gather, analyze, and interpret relevant data. This involves employing various techniques and utilizing appropriate tools to capture information that reflects the program’s performance against established goals and objectives. Robust data collection and measurement are critical for identifying areas of strength, pinpointing vulnerabilities, and making informed decisions to enhance the overall security posture.
Techniques for Data Collection
Data collection for security program performance assessment encompasses a variety of methods designed to gather information from different sources. These techniques are often used in combination to provide a comprehensive view of the security program’s effectiveness.
- Security Information and Event Management (SIEM) Systems: SIEM systems are central to security data collection. They aggregate logs from various sources, including network devices, servers, and applications, providing a centralized view of security events. SIEM systems facilitate real-time monitoring, incident detection, and security analysis.
- Vulnerability Scanning: Regular vulnerability scans identify weaknesses in systems and applications. These scans assess for known vulnerabilities, misconfigurations, and other security flaws. The results provide data on the effectiveness of vulnerability management processes and the overall security posture.
- Penetration Testing: Penetration testing, or ethical hacking, simulates real-world attacks to assess the effectiveness of security controls. Penetration tests provide valuable insights into the exploitability of vulnerabilities and the organization’s ability to detect and respond to attacks.
- Incident Response Metrics: Data on incident response activities, such as the number of incidents, time to detection, time to containment, and time to recovery, are crucial for measuring the efficiency of incident response processes. This data helps identify areas for improvement in incident handling and response capabilities.
- User Surveys and Feedback: Gathering feedback from users through surveys and other means provides insights into security awareness, training effectiveness, and user experiences with security tools and policies. This qualitative data complements the quantitative data collected through other techniques.
- Compliance Audits: Compliance audits assess adherence to relevant security standards, regulations, and policies. Audit findings provide data on the effectiveness of security controls and the organization’s compliance posture.
- Network Traffic Analysis: Analyzing network traffic patterns helps identify suspicious activity, unauthorized access attempts, and potential security breaches. Network traffic analysis tools capture and analyze data packets to detect anomalies and security threats.
Tools and Technologies for Security Data Collection and Analysis
A variety of tools and technologies are used to collect, analyze, and visualize security data. The selection of tools depends on the specific needs of the organization, the complexity of the security environment, and the types of data that need to be collected.
- SIEM Systems: Examples include Splunk, IBM QRadar, and ArcSight. SIEM systems collect and analyze security logs, providing real-time monitoring, incident detection, and reporting capabilities. They also often integrate with other security tools.
- Vulnerability Scanners: Examples include Nessus, OpenVAS, and Qualys. These tools automatically scan systems and applications for vulnerabilities, providing reports on identified weaknesses and recommended remediation steps.
- Endpoint Detection and Response (EDR) Tools: EDR tools, such as CrowdStrike Falcon and Microsoft Defender for Endpoint, monitor endpoint devices for malicious activity and provide threat detection and response capabilities. They collect data on endpoint events and behaviors.
- Network Intrusion Detection and Prevention Systems (IDS/IPS): Examples include Snort and Suricata. IDS/IPS monitor network traffic for suspicious activity and can automatically block or alert on malicious events. They collect data on network attacks and security incidents.
- Security Orchestration, Automation, and Response (SOAR) Platforms: SOAR platforms, like Splunk Phantom and Demisto, automate security tasks and workflows, such as incident response and threat hunting. They integrate with various security tools to streamline operations and improve efficiency.
- Threat Intelligence Feeds: These feeds, such as those from Recorded Future and Mandiant, provide information on emerging threats, vulnerabilities, and indicators of compromise (IOCs). They help security teams stay informed about the latest threats and proactively defend against them.
- Data Visualization Tools: Tools like Tableau and Power BI are used to create dashboards and reports that visualize security data, making it easier to identify trends, patterns, and anomalies.
Establishing a Data Governance Framework
A robust data governance framework is essential for ensuring the accuracy, integrity, and security of security data. This framework establishes policies, procedures, and responsibilities for managing data throughout its lifecycle, from collection to analysis and retention.
- Data Classification: Classifying data based on its sensitivity and criticality is the first step. This involves categorizing data into different levels (e.g., public, internal, confidential, restricted) to determine the appropriate security controls and access restrictions.
- Data Ownership and Stewardship: Assigning clear ownership and stewardship responsibilities for data ensures accountability and facilitates effective data management. Data owners are responsible for defining data quality standards, while data stewards ensure those standards are met.
- Data Quality Standards: Establishing data quality standards, such as accuracy, completeness, consistency, and timeliness, is crucial for ensuring the reliability of data. These standards should be documented and consistently applied.
- Data Access Controls: Implementing access controls, such as role-based access control (RBAC) and least privilege, restricts access to data based on the principle of least privilege. This limits the risk of unauthorized access and data breaches.
- Data Security and Privacy: Implementing security measures, such as encryption, access controls, and regular security audits, protects data from unauthorized access, modification, or disclosure. Compliance with relevant privacy regulations, such as GDPR and CCPA, is essential.
- Data Retention and Disposal: Defining data retention policies and procedures ensures that data is retained for the appropriate period and securely disposed of when no longer needed. This helps to comply with legal and regulatory requirements and minimizes the risk of data breaches.
- Data Monitoring and Auditing: Implementing data monitoring and auditing mechanisms tracks data access, modifications, and other activities. This provides visibility into data usage and helps detect and respond to security incidents.
- Regular Review and Updates: Regularly reviewing and updating the data governance framework ensures its continued effectiveness. This includes assessing data quality, compliance with regulations, and the evolving threat landscape.
Measuring Security Awareness and Training Effectiveness
Measuring the effectiveness of security awareness and training is crucial for ensuring that employees understand and comply with security policies. This evaluation helps organizations identify areas where training needs improvement and ensures that the investment in training programs yields tangible results. It involves a multi-faceted approach that goes beyond simply delivering the training; it includes assessing knowledge retention, behavioral changes, and the program’s overall impact on the organization’s security posture.
Demonstrating the Impact of Security Awareness Training Programs
Demonstrating the impact of security awareness training requires a strategic approach that links training to measurable outcomes. This involves establishing clear objectives, tracking key metrics, and analyzing the data to determine whether the training has achieved its goals. A well-designed program can significantly reduce security incidents, improve compliance rates, and foster a security-conscious culture.
- Pre- and Post-Training Assessments: Administering assessments before and after training allows for a direct comparison of employee knowledge and understanding. These assessments can take the form of quizzes, simulations, or real-world scenarios to gauge comprehension of key security concepts. For example, a pre-training assessment might reveal that only 30% of employees can correctly identify a phishing email. After training, a post-training assessment might show that this number increases to 85%, indicating a significant improvement in awareness.
- Tracking Security Incident Reduction: Monitor the frequency and severity of security incidents, such as phishing attacks, malware infections, and data breaches, before and after the training program is implemented. A decrease in these incidents suggests that the training is effective in changing employee behavior and reducing risks. For instance, a company that experiences 10 phishing attacks per month before training might see this number drop to 2-3 attacks per month after the training, a clear indicator of the program’s success.
- Measuring Compliance with Security Policies: Assess employee adherence to security policies, such as password management, data handling, and access control, before and after training. This can be done through audits, spot checks, or system logs. Increased compliance rates indicate that employees are internalizing and applying the knowledge gained from the training. For example, an audit might reveal that 60% of employees are using strong passwords before training.
After training, this might increase to 90%, demonstrating improved password security practices.
- Analyzing Phishing Simulation Results: Conduct simulated phishing attacks to assess employee susceptibility to phishing attempts. Track the click-through rates, the number of employees who provide their credentials, and the reporting rates. A decrease in click-through rates and an increase in reporting rates after training suggest that employees are better equipped to recognize and respond to phishing attacks. For example, a company that has a 20% click-through rate on phishing simulations before training might see this drop to 5% or less after training, indicating a substantial improvement in employee awareness.
- Evaluating User Behavior on Systems: Review system logs and data access patterns to identify any changes in employee behavior related to security protocols. This includes assessing whether employees are following data handling procedures, using approved tools, and avoiding risky behaviors. This analysis provides insights into whether the training has influenced employee actions in the workplace.
Identifying Methods for Assessing Employee Understanding of Security Policies
Assessing employee understanding of security policies requires employing various methods that go beyond simple quizzes. These methods aim to evaluate not only what employees know but also how they apply that knowledge in real-world situations. This holistic approach ensures that training effectively translates into improved security practices.
- Knowledge-Based Assessments: Utilize quizzes, tests, and examinations to evaluate employees’ comprehension of security policies and procedures. These assessments should cover key concepts, such as password management, data protection, and incident reporting. The questions should be designed to test not only recall but also the ability to apply the learned information to various scenarios.
- Scenario-Based Simulations: Employ simulations that present employees with realistic security threats and challenges. These simulations can involve phishing emails, social engineering attempts, or data breaches. Employees are required to respond to these scenarios in a manner that aligns with security policies, thus demonstrating their understanding and application of the training.
- Practical Exercises: Conduct hands-on exercises that require employees to apply their knowledge of security policies. These exercises might involve tasks such as creating strong passwords, identifying phishing emails, or reporting security incidents. The exercises should be designed to reinforce the training and provide employees with practical experience.
- Reviewing Employee Actions: Monitor employee actions on systems and networks to assess their adherence to security policies. This can involve reviewing system logs, data access patterns, and incident reports. The goal is to identify any instances of non-compliance and to provide feedback and additional training where necessary.
- Peer-to-Peer Discussions and Role-Playing: Facilitate peer-to-peer discussions and role-playing exercises to encourage employees to share their understanding of security policies and to learn from each other. These activities can help to reinforce the training and to promote a security-conscious culture. Role-playing can simulate real-world scenarios, such as a phishing attempt, where employees must respond according to the established policies.
Designing a Survey to Gather Feedback on the Effectiveness of Security Training
A well-designed survey is a powerful tool for gathering feedback on the effectiveness of security training. It allows organizations to understand what employees learned, how they perceive the training, and how it has impacted their behavior. This feedback is invaluable for improving future training programs.
- Survey Objectives: Clearly define the objectives of the survey. What specific information do you want to gather? Examples include assessing knowledge retention, evaluating the training’s relevance, and identifying areas for improvement.
- Survey Structure: Design a clear and concise survey structure. Use a combination of question types, such as multiple-choice, Likert scales (strongly agree to strongly disagree), and open-ended questions, to gather both quantitative and qualitative data.
- Question Types: Include a variety of question types to gather comprehensive feedback:
- Knowledge-Based Questions: Assess employees’ understanding of key security concepts. For example: “What is the definition of phishing?”
- Relevance and Applicability Questions: Determine the relevance of the training to employees’ daily tasks. For example: “How relevant was the training to your job role?”
- Behavioral Questions: Evaluate changes in employee behavior. For example: “Have you changed your password habits after the training?”
- Training Evaluation Questions: Gather feedback on the training’s format, content, and delivery. For example: “How would you rate the clarity of the training materials?”
- Survey Distribution: Choose an appropriate method for distributing the survey. This might involve email, an online survey platform, or a combination of both. Ensure that the survey is accessible to all employees and that they understand how to participate.
- Survey Sample Questions: Include the following examples:
- “On a scale of 1 to 5 (1 being Not at all, 5 being Extremely), how would you rate your understanding of phishing after completing the training?”
- “Since completing the training, have you been more cautious about clicking on links in emails? (Yes/No)”
- “What, if anything, could be improved about the training?”
- Data Analysis: Plan how you will analyze the survey data. This might involve using statistical analysis to identify trends and patterns or reviewing open-ended responses to gain a deeper understanding of employee feedback.
- Confidentiality and Anonymity: Assure employees that their responses will be kept confidential and anonymous to encourage honest feedback.
- Feedback Loop: Communicate the results of the survey to employees and explain how their feedback will be used to improve future training programs. This closes the feedback loop and demonstrates that their input is valued.
Assessing the Impact of Security Controls
Evaluating the effectiveness of security controls is crucial for any organization’s security program. This assessment provides valuable insights into how well implemented controls mitigate identified risks, protect valuable assets, and ensure compliance with relevant regulations and standards. Regular evaluation allows for informed decision-making, resource allocation, and continuous improvement of the overall security posture.
Measuring the Effectiveness of Technical Security Controls
Technical security controls, such as firewalls, intrusion detection systems (IDS), and endpoint detection and response (EDR) solutions, form the backbone of an organization’s defense-in-depth strategy. Their effectiveness is determined by their ability to prevent, detect, and respond to security threats.To measure the effectiveness of firewalls, consider the following:
- Firewall Rule Analysis: Regularly review firewall rules to ensure they are up-to-date, necessary, and aligned with the organization’s security policy. Inefficient or overly permissive rules can create vulnerabilities. Automated tools can assist in identifying redundant, conflicting, or overly broad rules.
- Log Analysis: Monitor firewall logs for blocked and allowed traffic, unusual activity, and potential attack attempts. Analyze the volume and nature of blocked traffic to identify trends and potential threats. This data can highlight successful and unsuccessful attacks.
- Performance Metrics: Track firewall performance metrics such as throughput, latency, and resource utilization (CPU, memory). Sustained high resource utilization can indicate a need for optimization or hardware upgrades.
- Vulnerability Scanning: Conduct regular vulnerability scans of systems behind the firewall to identify weaknesses that could be exploited. Compare scan results before and after firewall configuration changes to assess the impact on the attack surface.
For Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), effectiveness can be measured by:
- Alert Volume and Accuracy: Assess the number of alerts generated and the rate of false positives and false negatives. A high false positive rate can lead to alert fatigue, while false negatives indicate that malicious activity is going undetected. Tuning the IDS/IPS to reduce false positives is critical.
- Detection of Attacks: Analyze alerts to determine the types of attacks detected and the effectiveness of the system in blocking or mitigating them. Track the number of successful and unsuccessful attacks.
- Response Time: Measure the time it takes to respond to detected incidents. Faster response times can limit the impact of successful attacks.
- Signature Updates: Ensure that the IDS/IPS signature database is regularly updated to detect the latest threats. Track the frequency and timeliness of signature updates.
Endpoint Detection and Response (EDR) tools require a different set of metrics:
- Detection of Malicious Activity: Track the number of malicious activities detected, the types of threats identified, and the effectiveness of the EDR solution in preventing or containing them.
- Response Actions: Measure the time it takes to respond to detected incidents, including actions such as isolating infected endpoints, quarantining files, and remediating vulnerabilities.
- Endpoint Visibility: Assess the level of visibility into endpoint activity, including process execution, network connections, and file system changes.
- Threat Hunting: Evaluate the effectiveness of threat hunting activities in proactively identifying and responding to threats.
Comparing Methodologies for Assessing Security Control Performance
Different methodologies can be employed to assess the performance of security controls, each with its own strengths and weaknesses.
- Vulnerability Scanning: This automated process identifies known vulnerabilities in systems and applications. It is a proactive approach to identify weaknesses before attackers can exploit them. Vulnerability scans can be internal, external, or both. External scans simulate attacks from the internet. Internal scans assess vulnerabilities from within the network.
- Penetration Testing: Penetration testing simulates real-world attacks to identify vulnerabilities and assess the effectiveness of security controls. Ethical hackers attempt to exploit vulnerabilities to gain access to systems and data. Penetration tests provide a more in-depth assessment than vulnerability scans, but they are typically more expensive and time-consuming.
- Security Audits: Security audits assess compliance with security policies, standards, and regulations. Audits can be internal or external. External audits are often required for regulatory compliance.
- Red Teaming: Red teaming is a more advanced form of penetration testing that simulates a real-world attack scenario. Red teams attempt to achieve specific objectives, such as gaining access to sensitive data or disrupting business operations.
- Tabletop Exercises: Tabletop exercises involve simulating a security incident and walking through the response procedures. They can help to identify gaps in incident response plans and improve team coordination.
The choice of methodology depends on the specific goals of the assessment, the organization’s risk profile, and its resources. Often, a combination of methodologies is used to provide a comprehensive assessment of security control effectiveness.
Examples of Reports Showing the Impact of Security Controls on Risk Reduction
Reports generated from security control assessments provide valuable insights into the impact of security controls on risk reduction. These reports should be tailored to the audience and should include clear, concise, and actionable information.A typical firewall effectiveness report might include the following:
- Blocked Traffic Summary: A chart showing the number of connections blocked by the firewall over a specific time period. This can illustrate the firewall’s ability to prevent unauthorized access attempts. For instance, a graph showing a consistent pattern of blocked traffic, with peaks during periods of known vulnerability announcements, would indicate effective protection.
- Top Blocked Ports: A list of the ports most frequently blocked by the firewall. This information helps identify potential attack vectors and the types of attacks being attempted. High traffic on unusual ports could indicate scanning activity.
- Firewall Rule Review: A table summarizing the firewall rules, including their status (enabled/disabled), source and destination IP addresses, ports, and action (allow/deny). This can be used to identify overly permissive or unnecessary rules.
- Vulnerability Scan Results: A comparison of vulnerability scan results before and after firewall configuration changes. This demonstrates how the firewall configuration has reduced the attack surface.
An IDS/IPS effectiveness report might include:
- Alert Volume and Severity: A chart showing the number of alerts generated by the IDS/IPS, categorized by severity level (critical, high, medium, low). This provides an overview of the threat landscape and the system’s ability to detect threats.
- Top Attack Types: A list of the most frequently detected attack types, such as port scans, malware infections, and web application attacks.
- False Positive/Negative Analysis: A summary of the false positive and false negative rates.
- Response Time Metrics: A table showing the average time to respond to alerts, including actions taken to contain or mitigate the threat.
An EDR effectiveness report could include:
- Malware Detection and Prevention: The report can provide details on the number of malware detections and successful prevention events. It can be illustrated with a graph showing the number of malware events over time, along with a comparison of the number of events before and after the EDR implementation.
- Incident Response Time: The report includes the average time taken to contain and remediate security incidents. This can be displayed with a bar chart showing the average incident response time.
- Threat Hunting Activities: The report can provide insights into threat hunting activities, detailing the number of threats discovered through proactive hunting, and the impact of these discoveries.
These reports provide concrete evidence of the impact of security controls on risk reduction. They are crucial for communicating the value of the security program to stakeholders, securing budget approvals, and driving continuous improvement.
Evaluating Incident Response and Recovery
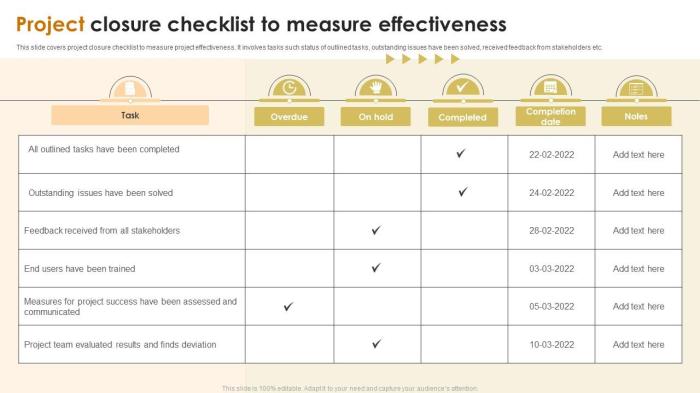
Effectively evaluating incident response and recovery is crucial for maintaining a robust security posture. This evaluation process allows organizations to identify strengths, pinpoint weaknesses, and continuously improve their ability to handle security incidents. Regular assessment ensures that incident response plans remain relevant and effective in the face of evolving threats.
Measuring Incident Response Efficiency and Effectiveness
Measuring the efficiency and effectiveness of incident response processes involves assessing various aspects of the response lifecycle. These assessments provide valuable insights into the overall performance and highlight areas for improvement.
- Mean Time to Detect (MTTD): This metric quantifies the average time it takes to discover a security incident. A shorter MTTD indicates a more efficient detection process. This is calculated as:
MTTD = (Total Time to Detect for All Incidents) / (Number of Incidents)
For example, if an organization experienced three incidents, and the time to detect each was 2 hours, 3 hours, and 4 hours, respectively, the MTTD would be 3 hours.
- Mean Time to Contain (MTTC): This metric measures the average time required to contain an incident, preventing further damage or spread. A lower MTTC signifies a more effective containment strategy.
MTTC = (Total Time to Contain for All Incidents) / (Number of Incidents)
Consider an organization that contained an incident in 1 hour, another in 1.5 hours, and a third in 2 hours. The MTTC would be approximately 1.5 hours.
- Mean Time to Recover (MTTR): MTTR calculates the average time it takes to restore systems and services to their normal operational state after an incident. Minimizing MTTR is crucial for minimizing downtime and business disruption.
MTTR = (Total Time to Recover for All Incidents) / (Number of Incidents)
For instance, if an incident took 3 hours to recover, another 4 hours, and a third 5 hours, the MTTR would be 4 hours.
- Number of Incidents Handled: This measures the total number of security incidents successfully addressed within a specific timeframe. Tracking this metric provides insight into the overall incident volume and the organization’s capacity to handle them.
- Incident Escalation Time: This metric assesses the time it takes to escalate an incident to the appropriate teams or individuals. Efficient escalation is critical for ensuring that the right resources are engaged promptly.
- False Positive Rate: This calculates the percentage of alerts that are incorrectly identified as security incidents. A high false positive rate can lead to wasted resources and alert fatigue.
- Adherence to SLAs: This measures whether incident response activities are completed within pre-defined Service Level Agreements (SLAs). Adherence to SLAs ensures that incidents are resolved within acceptable timeframes.
Metrics for Assessing Time to Detect, Contain, and Recover
Several metrics are crucial for assessing the time taken to detect, contain, and recover from security incidents. These metrics provide a clear understanding of the incident response lifecycle’s efficiency.
- Time to Detect: This measures the time elapsed from the start of a security incident to its discovery. The time is influenced by the effectiveness of security monitoring tools, alert systems, and threat intelligence.
- Time to Contain: This metric tracks the time it takes to contain an incident, preventing further damage. Containment actions might include isolating infected systems, blocking malicious network traffic, or disabling compromised accounts.
- Time to Recover: This assesses the time needed to restore systems and services to their normal operational state after an incident. Factors influencing recovery time include the availability of backups, the complexity of the incident, and the efficiency of recovery procedures.
- Incident Volume and Frequency: Monitoring the number and frequency of incidents over time provides insights into the overall security posture and the effectiveness of preventative measures.
- Cost of Incidents: Calculating the financial impact of security incidents, including direct costs (e.g., remediation efforts) and indirect costs (e.g., lost productivity, reputational damage), provides a comprehensive view of the incident’s overall impact.
Comparison of Incident Response Methodologies
Different incident response methodologies offer varied approaches to handling security incidents. The choice of methodology depends on the organization’s specific needs, resources, and risk profile. The following table compares some common incident response methodologies.
| Methodology | Key Features | Advantages | Disadvantages |
|---|---|---|---|
| NIST Cybersecurity Framework (CSF) | Focuses on five core functions: Identify, Protect, Detect, Respond, and Recover. It provides a comprehensive, risk-based approach to managing cybersecurity risk. | Provides a structured and flexible framework; offers broad applicability across various industries and organizational sizes. | Can be complex to implement fully; requires significant investment in time and resources; not prescriptive in its approach. |
| SANS Institute Incident Response Methodology | Emphasizes a six-step process: Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned. It offers detailed guidance on each phase. | Provides practical, step-by-step guidance; well-suited for technical teams; incorporates lessons learned to drive continuous improvement. | Can be resource-intensive; requires specialized skills and training; may not be ideal for organizations with limited resources. |
| ISO 27035 | Provides guidelines for managing information security incidents, including planning, preparation, detection, response, and recovery. It emphasizes a risk-based approach. | Offers a globally recognized standard; promotes a systematic and structured approach; facilitates compliance and interoperability. | Requires a good understanding of ISO standards; can be complex to implement; requires documentation and adherence to defined processes. |
| MITRE ATT&CK Framework | Focuses on the tactics, techniques, and procedures (TTPs) used by adversaries. It provides a knowledge base of real-world attack behaviors. | Helps identify and understand adversary behaviors; improves threat detection and analysis; supports proactive defense strategies. | Primarily focused on threat modeling and detection; does not provide detailed guidance on incident response processes; requires expertise in threat analysis. |
Measuring Compliance and Regulatory Adherence
Maintaining compliance with relevant industry regulations and standards is crucial for any security program. It not only mitigates legal and financial risks but also builds trust with stakeholders. Regularly measuring and verifying adherence to these requirements is a fundamental component of a robust security posture. This involves understanding the specific regulations applicable to your organization, implementing necessary controls, and establishing processes for ongoing monitoring and assessment.
Measuring Compliance with Relevant Industry Regulations and Standards
Measuring compliance involves a systematic approach to ensure adherence to legal and industry-specific requirements. This typically includes identifying applicable regulations, mapping controls to those regulations, conducting regular audits and assessments, and documenting findings and remediation efforts. Organizations must demonstrate a commitment to maintaining compliance, evidenced by policies, procedures, and documented evidence.
Tools and Techniques for Conducting Compliance Audits
A variety of tools and techniques are employed to conduct compliance audits. These methods provide assurance that security controls are effectively implemented and operating as intended, and that the organization meets the requirements of the relevant standards.
- Internal Audits: Conducted by internal teams to assess compliance against internal policies and procedures, and to identify potential gaps before external audits. This involves reviewing documentation, interviewing personnel, and testing security controls.
- External Audits: Performed by independent third-party auditors to provide an objective assessment of compliance with industry regulations and standards. External audits often result in formal reports and certifications.
- Vulnerability Scanning: Automated tools used to identify weaknesses in systems and applications. These scans help identify vulnerabilities that could be exploited by attackers and that may violate compliance requirements.
- Penetration Testing: Simulated attacks performed by security professionals to assess the effectiveness of security controls. Penetration testing helps identify vulnerabilities and weaknesses that could be exploited by attackers.
- Compliance Management Software: Software solutions designed to automate and streamline the compliance process. These tools can help organizations track compliance requirements, manage controls, and generate reports.
- Log Analysis: Analyzing system and security logs to detect anomalies, security incidents, and potential compliance violations. Log analysis is critical for monitoring security events and detecting unauthorized activities.
Checklist for Assessing Adherence to a Specific Security Framework (e.g., NIST, ISO 27001)
Creating a checklist based on a specific security framework, such as NIST or ISO 27001, is an effective way to assess adherence. The checklist should align with the framework’s specific controls and requirements. The following is an example, focused on a simplified version of the NIST Cybersecurity Framework’s Identify function. Remember that real-world frameworks contain many more controls and requirements.
| NIST Cybersecurity Framework Category | Control/Requirement | Assessment Method | Compliance Status (Yes/No/Partial) | Evidence/Comments |
|---|---|---|---|---|
| Asset Management | Identify and document all critical assets (hardware, software, data). | Review asset inventory, interviews with IT staff. | e.g., Asset inventory up-to-date? | |
| Asset Management | Categorize assets based on criticality and sensitivity. | Review asset classification policy and documentation. | e.g., Data classified according to policy? | |
| Business Environment | Understand the organization’s business objectives, mission, and legal and regulatory requirements. | Review strategic plans, legal documentation, and risk assessments. | e.g., Legal and regulatory requirements documented and understood? | |
| Risk Assessment | Identify and assess potential threats and vulnerabilities. | Review risk assessment documentation and methodology. | e.g., Risk assessment conducted regularly? | |
| Risk Assessment | Determine the likelihood and impact of potential security incidents. | Review risk assessment documentation. | e.g., Impact of potential incidents documented? | |
| Risk Management Strategy | Develop a risk management strategy that aligns with the organization’s risk appetite. | Review risk management policy and procedures. | e.g., Risk management strategy documented? |
This checklist provides a basic example; a real-world assessment would involve many more controls and detailed evaluation criteria. Each row represents a specific control or requirement from the framework. The “Assessment Method” column describes how to verify compliance, and the “Compliance Status” column indicates the result of the assessment. The “Evidence/Comments” section provides space for documenting supporting evidence and observations.
Regular use of such checklists ensures continuous monitoring and provides the organization with an understanding of its compliance posture.
Reporting and Communication of Results
Effectively communicating the performance of your security program is crucial for gaining stakeholder support, justifying investments, and driving continuous improvement. This involves creating clear, concise reports and tailoring the information to the specific audience. Transparency and consistent reporting build trust and demonstrate the value of your security efforts.
Design of a Template for Regular Security Program Performance Reports
Creating a standardized template ensures consistency and efficiency in reporting. This template should be adaptable to various audiences and reporting frequencies (e.g., monthly, quarterly, annually). A well-designed template facilitates the tracking of progress against goals and objectives.Here’s a recommended structure for a security program performance report template:
- Executive Summary: A brief overview of the report’s key findings, including overall program performance, significant achievements, and any critical issues. This section should be concise and written for senior management.
- Key Performance Indicators (KPIs): A summary of the KPIs tracked, including the current values, target values, and trends over time. This section should present data clearly, using visualizations where appropriate.
- Security Incidents: A summary of security incidents that occurred during the reporting period, including the type of incident, impact, and any remediation efforts. This section should maintain confidentiality and avoid disclosing sensitive information.
- Security Control Effectiveness: An assessment of the effectiveness of security controls, including any identified gaps or weaknesses. This section should be based on data collected through testing, audits, and vulnerability assessments.
- Compliance and Regulatory Adherence: A summary of compliance activities and any findings related to regulatory requirements. This section should include information on audits, assessments, and any corrective actions taken.
- Security Awareness and Training: A summary of security awareness and training activities, including participation rates and effectiveness metrics. This section should highlight any improvements in employee knowledge and behavior.
- Recommendations: A list of recommendations for improving the security program, based on the findings of the report. This section should be actionable and prioritized.
- Appendix: Supporting documentation, such as detailed KPI data, incident reports, and audit findings.
Communication of Security Program Results to Different Stakeholders
Different stakeholders require different levels of detail and emphasis in the reports. Tailoring your communication to the audience ensures that the information is relevant and easily understood. Consider the following stakeholders and how to communicate with them:
- Senior Management: Provide high-level summaries of overall program performance, key risks, and significant achievements. Focus on the business impact of security, such as cost savings, risk reduction, and regulatory compliance. Use concise language and avoid technical jargon.
- IT Department: Provide detailed technical information on security controls, vulnerabilities, and incidents. Focus on technical issues and remediation efforts. Use technical language and include supporting data.
- Security Team: Provide detailed information on security incidents, investigations, and remediation efforts. Focus on technical details and incident response activities. Use technical language and include detailed analysis.
- Legal and Compliance: Provide information on compliance with regulations and legal requirements. Focus on legal and regulatory aspects. Use legal and compliance terminology.
- Employees: Provide general awareness training and updates on security policies and procedures. Focus on practical steps employees can take to improve security. Use clear, concise language and avoid technical jargon.
Examples of Visualizations for Presenting Security Performance Data
Visualizations make data more accessible and understandable. They can help stakeholders quickly grasp key trends and patterns. The choice of visualization should depend on the type of data being presented and the message you want to convey.Here are some examples of visualizations commonly used in security program reporting:
- Line Chart: Used to show trends over time. For example, a line chart can track the number of phishing emails reported per month, demonstrating the effectiveness of phishing awareness training. The x-axis represents time (e.g., months), and the y-axis represents the number of reported emails. Different lines can represent different categories (e.g., successful phishing attempts, phishing emails blocked).
- Bar Chart: Used to compare different categories. For example, a bar chart can show the number of security incidents by type (e.g., malware, phishing, data breach). The x-axis represents the incident types, and the y-axis represents the number of incidents. Bars of different colors can represent different time periods.
- Pie Chart: Used to show proportions of a whole. For example, a pie chart can show the percentage of security incidents by source (e.g., internal, external). Each slice of the pie represents a different source, with the size of the slice corresponding to the percentage of incidents.
- Heatmap: Used to visualize data across a matrix. For example, a heatmap can show the risk level of different systems or assets. Colors represent different risk levels (e.g., green for low risk, red for high risk). This visualization allows for the quick identification of areas needing attention.
- Table: Used to present detailed data in a structured format. For example, a table can present the results of vulnerability scans, including the vulnerability name, severity, and affected systems. This provides a clear and concise way to display specific details.
- Radar Chart (Spider Chart): Used to visualize the performance of multiple KPIs in a single view, especially useful for comparing performance against targets or benchmarks. The chart has multiple axes, one for each KPI, radiating from a central point. The values for each KPI are plotted on their respective axes and connected to form a polygon. For example, a radar chart could display performance across several security domains (e.g., incident response, access control, vulnerability management), allowing for a quick assessment of strengths and weaknesses.
For example, consider a company, “SecureTech,” that implemented a new security awareness program. They tracked phishing email clicks before and after the program.
Before the Program: 15% of employees clicked on phishing emails.
After the Program: 5% of employees clicked on phishing emails.
This data could be presented using a bar chart to visually demonstrate the program’s effectiveness. The chart would have two bars: one representing “Before the Program” with a value of 15%, and another representing “After the Program” with a value of 5%. The visual contrast clearly highlights the reduction in phishing email clicks. This chart is easily understood by senior management, showing the program’s positive impact in a simple and effective way.
Continuous Improvement and Optimization
The security program’s effectiveness isn’t a static achievement; it’s a dynamic process that requires constant refinement. Continuous improvement ensures the program adapts to evolving threats, vulnerabilities, and business needs. By analyzing performance data, organizations can identify areas for enhancement, optimize existing controls, and proactively mitigate future risks. This iterative approach is crucial for maintaining a robust and resilient security posture.
Strategies for Utilizing Performance Data
Analyzing performance data is essential for driving improvements in the security program. This involves a systematic approach to identifying weaknesses, understanding trends, and implementing corrective actions.
- Identifying Weaknesses and Gaps: Reviewing KPIs and other metrics can pinpoint areas where the security program is underperforming. For instance, a consistently high rate of phishing email clicks indicates a weakness in security awareness training. Similarly, a high number of successful malware infections could highlight vulnerabilities in endpoint protection.
- Analyzing Trends and Patterns: Examining data over time reveals trends and patterns that can inform proactive security measures. For example, an increase in brute-force attacks targeting a specific application might necessitate strengthening access controls or implementing multi-factor authentication (MFA).
- Benchmarking Against Industry Standards: Comparing performance data against industry benchmarks or best practices provides valuable context. This allows organizations to assess their security posture relative to their peers and identify areas where they lag behind or excel.
- Prioritizing Remediation Efforts: Data-driven insights help prioritize remediation efforts. By focusing on the most significant vulnerabilities and risks, organizations can allocate resources effectively and maximize their impact. For example, addressing vulnerabilities that pose the greatest threat to critical assets should take precedence.
- Evaluating the Effectiveness of Changes: After implementing changes, it’s crucial to measure their impact. This involves tracking KPIs before and after the changes to determine whether they have improved the security posture. For example, if MFA is implemented, track the number of successful brute-force attacks before and after implementation to assess its effectiveness.
Methods for Continuous Monitoring and Optimization
Continuous monitoring and optimization are essential components of a robust security program. This involves proactively assessing the effectiveness of security controls and making adjustments as needed.
- Automated Security Control Monitoring: Employing automated tools to monitor security controls in real-time is crucial. These tools can detect anomalies, trigger alerts, and provide insights into potential security incidents. For example, a Security Information and Event Management (SIEM) system can analyze logs from various sources to identify suspicious activity.
- Regular Vulnerability Scanning and Penetration Testing: Conducting regular vulnerability scans and penetration tests helps identify weaknesses in systems and applications. These assessments provide valuable insights into potential attack vectors and the effectiveness of existing security controls. For instance, penetration tests can simulate real-world attacks to identify vulnerabilities that could be exploited by malicious actors.
- Threat Intelligence Integration: Integrating threat intelligence feeds into the security program provides insights into emerging threats and vulnerabilities. This allows organizations to proactively identify and mitigate risks before they can cause harm. For example, threat intelligence feeds can alert organizations to new phishing campaigns or zero-day vulnerabilities that could impact their systems.
- Configuration Management and Hardening: Regularly reviewing and updating system configurations is vital. This includes applying security patches, disabling unnecessary services, and implementing secure configurations based on industry best practices. For example, implementing CIS benchmarks for operating systems can significantly improve security posture.
- Performance Tuning and Optimization: Regularly reviewing the performance of security controls and making adjustments as needed can improve their effectiveness and efficiency. This might involve optimizing firewall rules, tuning intrusion detection systems, or adjusting security policies.
Implementing a Feedback Loop for Continuous Improvement
Establishing a feedback loop is essential for driving continuous improvement in the security program. This involves collecting feedback from various sources, analyzing the data, and making adjustments to improve the program’s effectiveness.
- Establish clear channels for feedback: Create channels for employees, customers, and other stakeholders to provide feedback on the security program. This could include surveys, incident reporting forms, and dedicated communication channels.
- Collect feedback from various sources: Gather feedback from various sources, including incident reports, security audits, penetration tests, and employee feedback. This provides a comprehensive view of the security program’s strengths and weaknesses.
- Analyze feedback to identify trends and patterns: Analyze the collected feedback to identify trends and patterns that can inform improvements to the security program. This might involve identifying common vulnerabilities, areas of confusion, or gaps in security controls.
- Implement corrective actions: Based on the analysis of feedback, implement corrective actions to address identified weaknesses and improve the security program. This could include updating security policies, providing additional training, or implementing new security controls.
- Measure the impact of changes: After implementing corrective actions, measure their impact to determine whether they have improved the security program. This involves tracking KPIs and other metrics to assess the effectiveness of the changes.
- Iterate and refine: The feedback loop is an iterative process. Continuously collect feedback, analyze the data, implement corrective actions, and measure the impact of the changes to ensure the security program remains effective.
Ultimate Conclusion
In conclusion, effectively measuring the effectiveness of your security program is not merely a technical exercise but a strategic imperative. By adopting a data-driven approach, focusing on continuous improvement, and aligning security efforts with overall business goals, organizations can build a robust and adaptable security posture. This guide provides a roadmap for achieving these objectives, enabling you to confidently navigate the complexities of cybersecurity and safeguard your valuable assets.
Popular Questions
What are the initial steps in measuring security program effectiveness?
Begin by defining clear security goals aligned with business objectives, identifying relevant KPIs, and establishing data collection methods. Regular review and updating of these elements are essential.
How often should we review our security program’s effectiveness?
The frequency of review depends on your organization’s risk profile and the pace of change in your environment. However, at a minimum, an annual review is recommended, with more frequent reviews for high-risk areas or after significant changes.
What are some common challenges in measuring security program effectiveness?
Challenges include data collection inconsistencies, difficulty in attributing cause and effect, and resistance to change. Establishing a robust data governance framework and ensuring stakeholder buy-in can help overcome these obstacles.
How do we communicate security program effectiveness to non-technical stakeholders?
Use clear, concise language, visual aids like charts and graphs, and focus on the business impact of security efforts. Tailor your communication to the specific interests and priorities of each stakeholder group.
Can small businesses effectively measure their security program’s effectiveness?
Yes, absolutely. Even with limited resources, small businesses can implement effective measurement strategies by focusing on key areas, using readily available tools, and prioritizing simplicity and clarity in their approach.