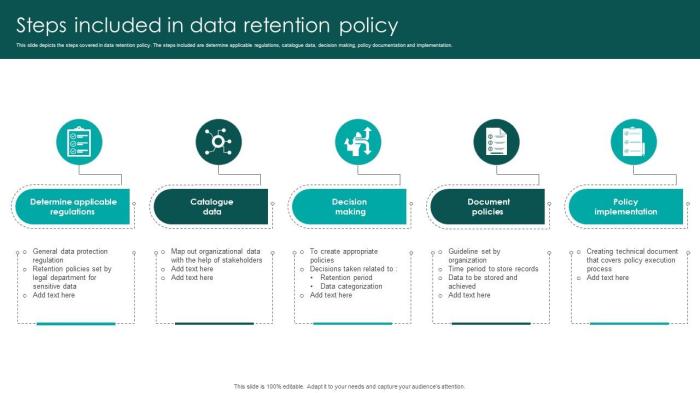
Embarking on the journey of data governance can seem daunting, but understanding how to create a data retention policy for compliance is essential in today’s regulatory landscape. This guide will illuminate the path to establishing a robust data retention policy, safeguarding your organization from potential legal pitfalls and financial penalties while enhancing data management practices.
We’ll delve into the critical components of a successful data retention strategy, from identifying and classifying data assets to defining retention periods and secure disposal methods. You’ll discover the importance of legal and regulatory considerations, the role of technology in supporting data retention, and strategies for monitoring and auditing compliance. This exploration will equip you with the knowledge to create a policy that not only meets compliance requirements but also optimizes your data management processes.
Understanding the Need for a Data Retention Policy
A data retention policy is essential for any organization that handles personal or sensitive information. It defines how long data should be stored, when it should be deleted, and the methods for its secure disposal. This proactive approach to data management is crucial for legal compliance, risk mitigation, and operational efficiency.
Legal and Regulatory Drivers
Numerous laws and regulations mandate data retention, varying by industry and jurisdiction. Failure to comply can result in severe penalties.
- General Data Protection Regulation (GDPR): The GDPR, applicable to organizations processing the data of individuals within the European Union, does not specify exact retention periods but requires data to be kept “no longer than is necessary” for the purposes for which it was collected. Organizations must justify their retention periods and provide a legal basis for processing. For example, if a company processes customer data for marketing purposes, the retention period should be limited to the duration of the customer relationship and a reasonable period afterward, considering consent withdrawal.
- California Consumer Privacy Act (CCPA): The CCPA, applicable to businesses that collect and sell California residents’ personal information, grants consumers rights to access, delete, and opt-out of the sale of their data. This necessitates clear data retention policies to facilitate these requests. A company must retain records of consumer requests for deletion and the company’s response for at least 24 months.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA, relevant to healthcare providers and their business associates in the United States, sets standards for the protection of sensitive patient health information (PHI). HIPAA mandates specific retention periods for various types of records, such as documentation related to privacy and security policies. For example, documentation related to a breach must be retained for at least six years from the date of the breach.
- Sarbanes-Oxley Act (SOX): SOX mandates specific retention periods for financial records, including audit trails, financial statements, and supporting documentation. This law is critical for publicly traded companies in the United States. SOX requires the retention of all audit or review work papers for a period of not less than seven years.
- Payment Card Industry Data Security Standard (PCI DSS): While PCI DSS doesn’t mandate specific data retention periods, it strongly recommends that cardholder data be retained only as long as necessary for business or legal reasons. This minimizes the risk of data breaches. For example, businesses must securely store and dispose of cardholder data, and retention periods must be justified by business needs.
Potential Risks of Inadequate Data Retention Practices
Failing to implement and adhere to a robust data retention policy can expose an organization to considerable risks.
- Financial Penalties: Non-compliance with data protection regulations can result in substantial fines. For instance, under GDPR, fines can reach up to 4% of a company’s annual global turnover or €20 million, whichever is greater. The CCPA allows for fines of up to $7,500 per violation.
- Legal Liability: Improper data retention practices can lead to costly litigation. If an organization fails to produce relevant data during a legal proceeding due to improper disposal or retention, it can face significant penalties, including adverse judgments.
- Reputational Damage: Data breaches or mishandling of personal information can severely damage an organization’s reputation, leading to a loss of customer trust and business. This damage can be difficult and expensive to repair.
- Data Breaches and Security Risks: Retaining data longer than necessary increases the risk of data breaches. The more data stored, the larger the attack surface for cybercriminals.
- Increased Storage Costs: Storing unnecessary data leads to higher storage costs, consuming valuable IT resources and increasing operational expenses.
- Operational Inefficiencies: Difficulty in retrieving relevant data due to poor organization and lack of a clear retention policy can hinder business operations, slowing down decision-making and impacting productivity.
Benefits of a Well-Defined Data Retention Policy
A well-defined data retention policy offers numerous advantages, enhancing operational efficiency and mitigating risks.
- Improved Data Management: A clear policy helps organize and categorize data, making it easier to find and retrieve information when needed. This improves data quality and facilitates informed decision-making.
- Reduced Storage Costs: By defining retention periods and establishing secure disposal methods, organizations can eliminate unnecessary data, reducing storage costs and freeing up valuable IT resources.
- Enhanced Legal Compliance: A data retention policy ensures adherence to relevant laws and regulations, minimizing the risk of fines and legal action. This includes the ability to demonstrate compliance during audits.
- Minimized Risk of Data Breaches: By reducing the amount of data stored, organizations decrease the attack surface for cybercriminals, mitigating the risk of data breaches and associated reputational damage.
- Streamlined eDiscovery: When litigation or investigations arise, a data retention policy facilitates eDiscovery by providing a clear framework for identifying and retrieving relevant data, thus reducing legal costs and time.
- Increased Efficiency: A well-defined policy helps employees locate and access the information they need quickly, improving productivity and streamlining business processes.
Identifying Data Assets and Categories
Understanding and properly categorizing your organization’s data assets is a crucial step in developing an effective data retention policy. This involves identifying the different types of data you possess, understanding their sources, and determining who is responsible for them. This categorization helps in applying appropriate retention periods and security measures, ensuring compliance and minimizing risk.
Data Types, Sources, and Ownership
Data comes in many forms, and classifying it correctly is essential for effective data governance. Data can be categorized by its type, the source from which it originates, and who is responsible for its management. This information provides a clear framework for implementing and enforcing data retention policies.
Here’s a table illustrating how data can be categorized. The table includes examples of data types, their common sources, and potential data owners within an organization.
This categorization helps streamline data management and retention strategies.
| Data Type | Description | Data Source | Data Owner (Example) |
|---|---|---|---|
| Customer Personally Identifiable Information (PII) | Information that can be used to identify an individual, such as names, addresses, and contact details. | CRM systems, order processing systems, marketing databases. | Head of Marketing, Head of Sales, Data Protection Officer. |
| Financial Data | Records related to financial transactions, including invoices, payment details, and bank statements. | Accounting software, banking portals, payment gateways. | Chief Financial Officer (CFO), Finance Department. |
| Employee Data | Information related to employees, including HR records, performance reviews, and payroll information. | HR management systems, payroll systems, internal communication platforms. | Head of Human Resources, HR Department. |
| Intellectual Property | Confidential business information, including trade secrets, patents, and proprietary designs. | Legal documents, research and development files, design software. | General Counsel, Head of Research and Development. |
This table is a simplified example. Real-world data classifications can be much more complex, depending on the size and nature of the organization. Each data type requires a tailored retention strategy, considering its sensitivity, regulatory requirements, and business needs.
Data Discovery and Classification Methods
Effectively identifying and classifying data involves a combination of automated tools and manual processes. These methods help in locating and categorizing data assets, which is the foundation of a sound data retention policy.
There are several methods to discover and classify data:
- Automated Data Discovery Tools: These tools scan your systems and identify data based on predefined criteria. They can locate sensitive information, classify data types, and provide insights into data storage locations. These tools often use techniques such as searching, pattern matching, and metadata analysis.
- Data Mapping: Data mapping involves documenting the flow of data within an organization. This includes identifying data sources, destinations, and transformations. Data mapping helps in understanding the data lifecycle and the relationships between different data elements.
- Manual Data Audits: Manual audits involve reviewing data manually to classify it. This can be time-consuming but is crucial for ensuring accuracy and identifying nuances that automated tools may miss. This often involves interviewing data owners and reviewing documentation.
- Data Inventory: Creating a data inventory involves cataloging all data assets, including their type, location, owner, and retention requirements. This provides a comprehensive overview of the organization’s data landscape.
Implementing a combination of these methods ensures a thorough and accurate data classification process. Regularly reviewing and updating these classifications is also essential to adapt to changing business needs and regulatory requirements.
Determining Retention Periods

Establishing appropriate data retention periods is a critical step in building a robust data retention policy. This process requires a careful balance of legal compliance, business operational needs, and the practicalities of data management. Setting these periods correctly minimizes risk, optimizes storage costs, and ensures data is available when needed.
Factors Influencing Retention Periods
Several key factors must be considered when determining how long data should be retained. These factors often interact, requiring a comprehensive and well-informed approach.
- Legal and Regulatory Requirements: Compliance with laws and regulations is paramount. This includes industry-specific regulations (e.g., HIPAA for healthcare, GDPR for data privacy in Europe), as well as general data protection laws. These regulations often mandate specific retention periods for certain types of data. For instance, financial records typically have retention requirements tied to tax regulations, often spanning several years. Non-compliance can result in significant fines and legal repercussions.
- Business Needs and Operational Requirements: Businesses must retain data long enough to support their operations, including customer service, dispute resolution, and strategic decision-making. This includes data needed for business continuity, auditing, and performance analysis. For example, customer transaction data might need to be retained for several years to handle potential disputes or provide historical context for customer interactions.
- Data Lifecycle: Understanding the data lifecycle—from creation to archival or deletion—is crucial. Data’s value often diminishes over time. Therefore, retention periods should be aligned with its relevance and usefulness. Data that is actively used and accessed frequently might have a shorter retention period than data stored for archival or compliance purposes. For instance, real-time operational data might be retained for weeks or months, while archived data might be retained for years.
- Data Value: The value of the data to the organization should be a factor in retention period decisions. High-value data, such as intellectual property or sensitive customer information, might warrant longer retention periods to protect the organization’s interests. Conversely, data with minimal value, such as temporary log files, might have shorter retention periods.
- Risk Assessment: Assessing the risks associated with data retention and deletion is essential. This includes the potential for data breaches, legal liabilities, and operational disruptions. Retention periods should be adjusted to mitigate these risks. For example, sensitive personal data should be retained only as long as necessary, considering the potential risks associated with its storage.
Examples of Retention Periods by Data Type
Retention periods vary significantly depending on the data type and the industry. Here are some examples, referencing industry best practices and legal precedents:
- Financial Records: Typically retained for 7-10 years after the end of the tax year, based on IRS regulations in the United States. This includes invoices, receipts, bank statements, and tax returns. This duration allows for audits and ensures compliance with tax laws.
- Human Resources Data: Employee records, including payroll, performance reviews, and termination documents, often have a retention period of 3-7 years after the employee leaves the company, or longer, depending on the jurisdiction. Legal requirements, such as those related to potential litigation or government audits, influence these durations.
- Customer Data: Customer data, including contact information, purchase history, and communications, may be retained for varying periods, often driven by business needs and legal requirements. The retention period can range from a few years to indefinitely, depending on the type of data and its use. For example, credit card information should be retained for a limited time, according to PCI DSS compliance standards.
- Legal Documents: Contracts, legal correspondence, and litigation-related documents are usually retained for the duration of the contract or potential litigation, plus a statute of limitations period, which can be several years. This ensures the availability of critical information for legal defense.
- Healthcare Records: In healthcare, patient records are often retained for many years, sometimes indefinitely, depending on the state and the age of the patient. This ensures continuity of care and supports medical research. HIPAA regulations in the United States also influence these retention periods.
- Email and Communications: Retention periods for emails and other communications can vary. Some organizations may retain all emails for a certain period for compliance purposes, while others may implement shorter retention periods for less critical communications.
- Backup Data: Backups should be retained long enough to recover from disasters or data loss incidents. This period is often determined by the business’s recovery time objective (RTO) and recovery point objective (RPO).
Decision-Making Process for Setting Retention Periods
Establishing a systematic decision-making process is essential for setting data retention periods effectively. This process should consider both the value and the risk associated with the data.
- Data Classification: Revisit the data classification process to ensure all data assets are correctly categorized and tagged. This helps identify data types and associated sensitivity levels.
- Legal and Regulatory Research: Research and identify all relevant legal and regulatory requirements applicable to each data category. Consult with legal counsel to ensure compliance.
- Business Requirements Analysis: Determine the business needs for each data category. Consider how long the data needs to be available for operational purposes, customer service, and decision-making.
- Risk Assessment: Assess the risks associated with retaining or deleting each data category. Consider the potential impact of data breaches, legal liabilities, and operational disruptions.
- Retention Period Determination: Based on the above factors, determine the appropriate retention period for each data category. Prioritize legal and regulatory requirements, then consider business needs and risk.
- Documentation: Document the retention periods for each data category in the data retention policy, including the rationale behind each decision.
- Implementation and Enforcement: Implement the retention policy through technical controls and employee training. Regularly monitor and enforce the policy to ensure compliance.
- Review and Update: Regularly review and update the data retention policy to reflect changes in legal requirements, business needs, and technology.
The key is to balance legal obligations, business needs, and risk mitigation to create a data retention policy that is both compliant and effective.
Defining Data Storage and Disposal Methods
Effectively managing data storage and disposal is crucial for a robust data retention policy. This involves choosing secure storage solutions that align with compliance requirements and defining approved methods for data disposal when retention periods expire. Proper implementation of these practices ensures data integrity, protects sensitive information, and minimizes legal and financial risks.
Secure Data Storage Options
Choosing the right data storage solution is a critical component of a data retention policy. Different storage options offer varying levels of security, scalability, and cost-effectiveness. The optimal choice depends on the organization’s specific needs, data volume, compliance obligations, and available resources.
- On-Premise Storage: This involves storing data on servers and infrastructure owned and managed by the organization within its physical premises.
- Pros: Provides greater control over data security and access, potentially meeting stringent compliance requirements. Offers data residency control, allowing data to remain within a specific geographic location.
- Cons: Requires significant upfront investment in hardware and infrastructure. Demands dedicated IT staff for maintenance, security, and updates. Scalability can be challenging and expensive.
- Cloud-Based Storage: This involves storing data on servers managed by a third-party cloud provider, such as Amazon Web Services (AWS), Microsoft Azure, or Google Cloud Platform (GCP).
- Pros: Offers scalability, allowing organizations to easily adjust storage capacity as needed. Reduces capital expenditure as the cloud provider handles infrastructure costs. Provides enhanced accessibility and collaboration capabilities.
- Cons: Relies on the security and compliance practices of the cloud provider. Requires a reliable internet connection. Data residency may be a concern depending on the provider’s data center locations.
- Hybrid Storage: This combines on-premise and cloud-based storage solutions, allowing organizations to leverage the benefits of both. Data is stored in a combination of both environments, determined by factors such as data sensitivity, access frequency, and compliance needs.
- Pros: Offers flexibility in data management, allowing organizations to store data in the most appropriate environment. Improves disaster recovery capabilities by distributing data across multiple locations.
Provides cost optimization by leveraging both on-premise and cloud resources.
- Cons: Requires careful planning and integration to ensure seamless data management and security. Can be more complex to manage than either on-premise or cloud-based solutions. May require expertise in both on-premise and cloud technologies.
- Pros: Offers flexibility in data management, allowing organizations to store data in the most appropriate environment. Improves disaster recovery capabilities by distributing data across multiple locations.
Approved Data Disposal Methods
Once data retention periods expire, secure data disposal is essential to prevent unauthorized access and maintain compliance. Organizations must implement approved methods for data disposal, ensuring that data is irretrievable and permanently removed from storage media.
- Secure Deletion: This involves using software to overwrite data on storage media, making it unrecoverable. This method is suitable for deleting data from hard drives, solid-state drives (SSDs), and other storage devices.
- Examples: Utilizing tools like the “shred” command in Linux or specialized data wiping software that adheres to industry standards like the National Institute of Standards and Technology (NIST) 800-88 guidelines.
These tools overwrite the data multiple times, ensuring that the original information is unrecoverable.
- Examples: Utilizing tools like the “shred” command in Linux or specialized data wiping software that adheres to industry standards like the National Institute of Standards and Technology (NIST) 800-88 guidelines.
- Data Sanitization: This is a broader term encompassing various methods to render data on storage media unrecoverable. It can include secure deletion, but also extends to methods like degaussing (for magnetic media) and physical destruction.
- Examples: For magnetic tapes, degaussing involves using a powerful magnetic field to erase the data. For SSDs, secure erasure methods must consider the wear-leveling and garbage collection features.
- Physical Destruction: This involves physically destroying the storage media, rendering the data irretrievable. This is the most secure method of data disposal, particularly for highly sensitive information.
- Examples: Shredding hard drives, crushing SSDs, or incinerating storage media. Organizations often use third-party vendors specializing in secure data destruction to ensure compliance with regulations. The process includes detailed documentation, including serial numbers and destruction certificates, to maintain a comprehensive audit trail.
Workflow for Data Disposal
Implementing a well-defined workflow for data disposal is essential for consistent and compliant data management. This workflow should include clear steps for identifying data eligible for disposal, selecting the appropriate disposal method, documenting the process, and verifying its completion.
- Identification: Identify data that has reached the end of its retention period. This should be based on the data retention policy and the specific data categories.
- Method Selection: Determine the appropriate data disposal method based on the sensitivity of the data, the storage media type, and regulatory requirements. Consider factors like cost, security, and the potential for data recovery.
- Disposal Execution: Execute the chosen data disposal method. This may involve using secure deletion software, sanitizing the storage media, or physically destroying the hardware.
- Documentation: Document the data disposal process. This should include details such as the date of disposal, the method used, the data that was disposed of, and the serial numbers of the storage devices. The documentation must be auditable.
- Verification: Verify the data disposal process. This may involve conducting spot checks to ensure that data has been securely deleted or that the storage media has been physically destroyed. Maintain the documentation for the required period, in accordance with the data retention policy.
Creating a Data Retention Policy Document
Now that you’ve identified your data assets, categorized them, and determined retention periods, it’s time to formalize everything into a comprehensive data retention policy document. This document serves as the official guide for your organization, ensuring consistent and compliant data management practices. It provides clarity, reduces risk, and streamlines operations related to data storage and disposal.
Structure of a Data Retention Policy Document
The structure of your data retention policy document should be clear, concise, and easy to understand. It should be organized in a logical manner, allowing employees to quickly find the information they need. A well-structured document will facilitate adherence and reduce the likelihood of misunderstandings.The key sections typically include:
- Scope: Defines the data covered by the policy, specifying the types of data, departments, and geographical locations the policy applies to. For example, the scope might include all electronic data, regardless of its format or storage location, generated by employees within the company’s global operations.
- Definitions: Provides clear definitions of key terms used throughout the policy. This ensures everyone understands the terminology, such as “data retention,” “disposal,” “archiving,” and “personally identifiable information (PII).” For instance, define “data retention” as the period of time data is stored, accessible, and retrievable.
- Responsibilities: Artikels the roles and responsibilities of individuals and departments involved in data retention, storage, and disposal. This section clarifies who is accountable for each aspect of the policy, such as the data owner, IT department, legal counsel, and compliance officer.
- Data Retention Schedules: This is the core of the policy, detailing the retention periods for each data category. This section often includes a table or matrix specifying the data category, the retention period (e.g., 7 years), the legal or business justification for the retention period, and the storage method (e.g., active, archive).
- Data Storage Procedures: Describes the methods and systems used for storing data, including considerations for security, accessibility, and backup. It might specify the use of specific cloud storage providers, on-premise servers, or other storage solutions.
- Data Disposal Procedures: Artikels the procedures for securely disposing of data when the retention period expires. This section should detail the methods for data destruction, such as secure deletion, physical destruction of storage media, and chain-of-custody procedures.
- Policy Enforcement and Review: Describes how the policy will be enforced, including monitoring, audits, and consequences for non-compliance. It should also specify the frequency of policy reviews and updates, typically annually or whenever there are changes in regulations or business needs.
- Policy Exceptions: Artikels the process for requesting exceptions to the policy, such as for legal holds or special business needs. This section should clearly state the circumstances under which exceptions are permitted and the required approval process.
Writing Clear and Concise Policy Statements
Clear and concise policy statements are essential for ensuring employees understand and adhere to the data retention policy. Avoid jargon and technical language whenever possible, and use plain language that is easily understood by all employees, regardless of their technical expertise.Here are some examples of clear and concise policy statements:
- Data Retention: “All financial records, including invoices, receipts, and bank statements, will be retained for a period of seven years from the end of the fiscal year in which they were created.”
- Data Storage: “Employee data, including personal information and performance reviews, will be stored securely on the company’s network drives and backed up daily. Access to this data is restricted to authorized personnel only.”
- Data Disposal: “Upon expiration of the retention period, all data must be securely disposed of by permanent deletion from all storage media. This includes hard drives, servers, and cloud storage. The IT department is responsible for overseeing the disposal process and documenting the destruction.”
- Legal Holds: “In the event of a legal hold, all data relevant to the legal matter must be preserved, even if the retention period has expired. The legal department will notify the relevant departments of the legal hold and provide instructions on how to preserve the data.”
Use active voice and avoid passive constructions. Instead of “Data should be disposed of securely,” write “The IT department will securely dispose of data.”
Incorporating Data Retention Policies into Existing Company Policies and Procedures
Integrating your data retention policy into existing company policies and procedures ensures consistency and promotes compliance across all departments. This integration simplifies training, reduces the risk of conflicting instructions, and reinforces the importance of data governance.Here are some ways to incorporate data retention policies:
- Employee Handbook: Include a summary of the data retention policy in the employee handbook, highlighting key responsibilities and data management practices.
- Training Programs: Develop training programs for employees, covering the data retention policy, their responsibilities, and best practices for data handling.
- IT Procedures: Integrate data retention procedures into IT protocols, such as data backup, archiving, and deletion processes.
- Contractual Agreements: Include data retention clauses in contracts with vendors and third-party service providers, ensuring they comply with your data retention requirements.
- Document Management System: Implement a document management system that automatically applies data retention rules to documents based on their type and content.
- Regular Audits: Conduct regular audits to ensure compliance with the data retention policy. The audits should review data storage practices, disposal procedures, and adherence to retention schedules.
For example, when onboarding new employees, include data retention training as part of the onboarding process. Similarly, update the company’s IT procedures to automatically archive email communications after a specific period, in line with the retention schedule.
Implementing and Communicating the Policy
Successfully implementing and communicating your data retention policy is crucial for ensuring compliance and minimizing risk. This section focuses on practical strategies to roll out your policy effectively, including training, technology integration, and ongoing maintenance. Clear communication and consistent enforcement are vital for the policy’s long-term success.
Communicating the Data Retention Policy to Employees
Communicating the data retention policy effectively requires a multi-faceted approach. This includes clear and concise explanations, accessible resources, and ongoing reinforcement to ensure employees understand and adhere to the policy.
- Training Programs: Implement comprehensive training programs for all employees. Training should cover the policy’s purpose, scope, and specific requirements. Use real-world examples to illustrate how the policy applies to different job roles and data types.
- Awareness Campaigns: Launch ongoing awareness campaigns to reinforce the policy’s importance. This could include regular email reminders, posters, and intranet articles. Use visual aids and interactive elements to keep employees engaged.
- Policy Accessibility: Make the data retention policy easily accessible to all employees. This could involve publishing the policy on the company intranet, providing physical copies, and making it available in employee handbooks. Ensure the policy is readily searchable.
- Regular Updates and Refreshers: Schedule regular refresher training sessions to update employees on any policy changes or new data types. Consider annual reviews and quizzes to test employee understanding.
- Role-Based Training: Tailor training programs to specific job roles. Employees who handle sensitive data, for example, might require more in-depth training on data security and privacy.
- Feedback Mechanisms: Establish channels for employees to ask questions and provide feedback on the policy. This can help identify areas where the policy needs clarification or improvement.
Checklist for Implementing the Data Retention Policy
Implementing a data retention policy involves several steps, from technological integration to process adjustments. This checklist provides a structured approach to ensure a smooth and successful implementation.
- Technology Integration: Integrate the data retention policy with existing technology infrastructure. This includes email systems, document management systems, and cloud storage platforms. Ensure that data retention settings are configured correctly across all relevant systems.
- Example: Configure Microsoft 365 retention policies to automatically delete emails and documents after a defined period.
- Data Classification and Tagging: Implement a system for classifying and tagging data based on its sensitivity and retention requirements. This will enable automated data management and ensure compliance with the policy.
- Process Documentation: Document all processes related to data retention, including data archiving, deletion, and retrieval. This documentation should be readily available to all relevant personnel.
- Employee Communication and Training: Communicate the policy to all employees and provide adequate training on its requirements. This should include training on how to identify and handle different types of data.
- Data Auditing and Monitoring: Implement regular data audits to ensure compliance with the policy. Monitor data storage systems to identify and address any issues.
- Vendor Management: Ensure that all third-party vendors comply with the data retention policy. This includes reviewing vendor contracts and conducting regular audits.
- Legal Review: Have the data retention policy reviewed by legal counsel to ensure it complies with all applicable laws and regulations.
- Executive Sponsorship: Secure executive sponsorship to ensure the policy is supported at all levels of the organization. This will help ensure that resources are allocated appropriately.
Maintaining and Updating the Data Retention Policy
A data retention policy is not a static document. It must be regularly reviewed and updated to reflect changes in legal requirements, business needs, and technology.
- Regular Reviews: Conduct regular reviews of the data retention policy, at least annually, or more frequently if there are significant changes in the legal or regulatory landscape.
- Legal and Regulatory Updates: Stay informed about changes in data privacy laws and regulations. Update the policy to reflect any new requirements.
- Example: The General Data Protection Regulation (GDPR) requires specific data retention practices for personal data.
- Business Needs Assessment: Assess the organization’s business needs and data requirements. Ensure that the policy aligns with current business operations.
- Technology Updates: Review the policy to ensure it is compatible with current technology. This includes cloud storage, data management systems, and other relevant platforms.
- Feedback and Incident Review: Collect feedback from employees and review any incidents related to data retention. Use this information to identify areas for improvement.
- Policy Documentation: Maintain clear documentation of all policy updates, including the rationale for the changes and the date of implementation.
- Communication of Updates: Communicate all policy updates to employees and provide additional training as needed.
Monitoring and Auditing Data Retention

Effective data retention isn’t a set-it-and-forget-it process. It demands ongoing vigilance to ensure compliance, minimize risk, and maintain the integrity of your data. This involves continuous monitoring, regular audits, and a clearly defined process for addressing any deviations from the established policy. This section will delve into the specifics of monitoring and auditing your data retention practices.
Monitoring Compliance Methods
Ongoing monitoring is crucial to ensure your data retention policy is consistently followed. This involves implementing various methods to track data lifecycle activities and identify potential issues.
- Automated Monitoring Tools: Employ software solutions to automatically monitor data storage locations, retention periods, and disposal schedules. These tools can generate alerts when data is nearing its retention deadline or when unusual activity is detected. For instance, a tool might flag a file that has been stored for longer than the permitted retention period, triggering an investigation.
- Regular Data Reviews: Conduct periodic reviews of data across all systems and storage locations. This can involve manually reviewing data samples or using automated tools to scan for data that violates the policy. These reviews help to identify and correct any discrepancies.
- Access Control Audits: Regularly audit user access to data. This ensures that only authorized personnel can access and modify data, reducing the risk of unauthorized data modification or deletion. Reviewing access logs can identify potential security breaches or policy violations.
- Change Management Processes: Implement strict change management processes for data systems and storage infrastructure. Any changes to these systems should be reviewed to ensure they do not inadvertently impact data retention practices. For example, if a new storage system is introduced, it should be configured to adhere to the existing data retention policy.
Key Performance Indicators (KPIs) for Data Retention
Measuring the effectiveness of your data retention policy requires the use of Key Performance Indicators (KPIs). These metrics provide quantifiable data to assess compliance and identify areas for improvement.
- Percentage of Data Retained According to Policy: This KPI measures the proportion of data that is correctly stored and disposed of according to the retention schedule. For example, if 98% of data is retained correctly, it indicates strong compliance.
- Number of Policy Violations: This KPI tracks the number of instances where data is stored for longer or shorter than the prescribed retention period. A high number of violations indicates potential weaknesses in the implementation of the policy.
- Time to Remediation of Policy Violations: This KPI measures the time it takes to correct policy violations. A shorter remediation time demonstrates efficiency in addressing compliance issues.
- Cost of Data Storage: Monitor the costs associated with data storage. This KPI helps in assessing the efficiency of data disposal and optimizing storage costs. Reducing unnecessary data storage directly impacts costs.
- Audit Completion Rate: This KPI tracks the percentage of planned audits that are successfully completed within the specified timeframe. A high completion rate indicates a proactive approach to compliance monitoring.
Procedure for Addressing Policy Violations
A well-defined procedure for addressing policy violations is critical for maintaining compliance. This procedure should Artikel the steps to be taken when a violation is detected, including corrective actions and disciplinary measures.
- Violation Detection and Reporting: Establish a clear process for detecting and reporting policy violations. This should include reporting mechanisms for employees to report potential violations.
- Investigation: Conduct a thorough investigation to determine the cause of the violation. This involves identifying the data involved, the individuals responsible, and the extent of the violation.
- Corrective Actions: Implement corrective actions to address the violation. This may involve correcting data storage, restoring deleted data, or updating access controls. For instance, if data has been stored for too long, it should be disposed of according to the policy.
- Disciplinary Measures: Determine appropriate disciplinary measures for employees who violate the policy. These measures should be consistent with the company’s disciplinary policies and may range from warnings to termination.
- Policy Updates: Review and update the data retention policy based on the findings of the investigation. This helps to prevent future violations by addressing the root causes of the issue.
- Documentation: Maintain detailed records of all policy violations, investigations, corrective actions, and disciplinary measures. This documentation is essential for demonstrating compliance during audits.
Legal and Regulatory Considerations
Data retention policies are fundamentally shaped by legal and regulatory requirements. Organizations must navigate a complex web of laws and guidelines to ensure they are compliant, avoiding penalties and legal challenges. Understanding these obligations is critical for creating a robust and legally sound data retention policy.
Identifying Legal Requirements Impacting Data Retention
Various laws and regulations directly influence how long specific data types must be retained. These requirements vary based on industry, jurisdiction, and the nature of the data.
- Data Breach Notification Laws: These laws mandate timely notification to individuals and regulatory bodies when a data breach compromises personal information. Data retention policies must ensure the ability to identify affected individuals and provide the required information within the stipulated timeframe. For example, the General Data Protection Regulation (GDPR) in the European Union requires notification to supervisory authorities within 72 hours of becoming aware of a breach, if feasible.
This necessitates efficient data retrieval and analysis capabilities built into the retention policy.
- Privacy Laws: Laws like the California Consumer Privacy Act (CCPA) and GDPR grant individuals rights regarding their personal data, including the right to access, rectify, and erase data. Retention policies must facilitate these rights, ensuring data can be located, updated, and deleted as requested. For instance, under CCPA, businesses must respond to consumer requests within 45 days.
- Financial Regulations: Industries like finance are heavily regulated regarding data retention. Regulations such as the Sarbanes-Oxley Act (SOX) in the United States require the retention of financial records for specific periods to ensure accuracy and prevent fraud. The retention period often depends on the document type and the nature of the transaction.
- Healthcare Regulations: The Health Insurance Portability and Accountability Act (HIPAA) in the US sets standards for protecting patient health information (PHI). HIPAA regulations dictate retention periods for medical records and related data, which are vital for auditing, compliance, and patient care.
- Industry-Specific Regulations: Numerous other industry-specific regulations, such as those governing telecommunications, energy, and transportation, may mandate specific data retention practices. These often relate to record-keeping for auditing, consumer protection, or safety.
Addressing the Needs of Different Regulatory Bodies
A successful data retention policy must be adaptable to the requirements of various regulatory bodies. This involves understanding the specific regulations applicable to an organization’s operations and tailoring the policy accordingly.
- Understanding the Scope: First, organizations must identify all applicable regulations. This may involve legal counsel, industry experts, and regulatory compliance software. For example, a multinational corporation operating in the financial sector may need to comply with SOX in the US, GDPR in the EU, and potentially other financial regulations in different countries.
- Mapping Data to Regulations: The organization should map its data assets to the relevant regulations. This involves categorizing data and determining which regulations apply to each category. This can be achieved by creating a data inventory and cross-referencing it with the regulatory requirements.
- Establishing Retention Schedules: Based on the regulations, the organization must establish specific retention schedules for each data category. These schedules should clearly define how long data must be retained and the triggers for deletion. For instance, under SOX, certain financial documents may need to be retained for seven years.
- Implementing Technical Controls: Technical controls are crucial for enforcing the data retention policy. These include data storage solutions with automated deletion capabilities, access controls to restrict access to data, and audit trails to track data access and modifications.
- Documenting the Policy: A comprehensive data retention policy document should clearly Artikel all regulatory requirements, retention schedules, and technical controls. This document serves as a reference for employees and auditors and demonstrates the organization’s commitment to compliance.
- Regular Audits: Regular audits should be conducted to ensure compliance with the data retention policy and relevant regulations. Audits can identify gaps in the policy, technical controls, or employee training.
Maintaining Compliance in an Evolving Legal and Regulatory Landscape
The legal and regulatory landscape surrounding data privacy and retention is constantly changing. Organizations must adopt a proactive approach to stay compliant.
- Monitoring Regulatory Changes: Organizations should continuously monitor changes in laws and regulations that impact data retention. This may involve subscribing to legal updates, attending industry conferences, and consulting with legal professionals.
- Regular Policy Reviews: The data retention policy should be reviewed and updated regularly to reflect changes in regulations and business practices. A typical review cycle is annually or more frequently if significant regulatory changes occur.
- Employee Training: Employees must be trained on the data retention policy and any updates. Training should cover regulatory requirements, retention schedules, and the proper handling of data.
- Flexibility and Adaptability: The data retention policy should be designed to be flexible and adaptable to future changes. This may involve using modular data storage solutions and building in the capacity to quickly update retention schedules.
- Risk Assessment: Regularly assess the risks associated with data retention, including the potential for data breaches, non-compliance, and legal penalties. This risk assessment should inform policy updates and the implementation of technical controls.
- Legal Counsel: Maintaining a strong relationship with legal counsel is crucial. They can provide expert advice on navigating complex regulatory requirements and ensuring compliance.
Technology and Tools for Data Retention
Implementing a robust data retention policy requires more than just written guidelines; it necessitates the integration of appropriate technologies and tools. These technologies streamline the processes of data archiving, backup, and disposal, ensuring compliance and minimizing risk. The right technological infrastructure can significantly reduce the manual effort required, enhance data security, and improve overall efficiency.
Role of Technology in Supporting Data Retention
Technology plays a crucial role in enabling and enforcing data retention policies. This involves a range of solutions designed to manage the lifecycle of data, from its creation to its eventual disposal.Data archiving solutions are designed to store data that is no longer actively used but must be retained for compliance or historical purposes. These solutions typically compress and index data, making it accessible when needed.
For example, a healthcare provider might archive patient records that are no longer actively used for treatment but are required to be kept for a specified period under HIPAA regulations.Backup solutions are essential for creating copies of data to protect against data loss due to hardware failure, human error, or cyberattacks. These solutions often involve regular backups, which can be full, incremental, or differential, and can be stored on-site, off-site, or in the cloud.
A financial institution, for instance, relies heavily on backup solutions to ensure the integrity of financial transactions and customer data.Data storage solutions provide the infrastructure for storing both active and archived data. This can range from on-premise servers and storage area networks (SANs) to cloud-based storage services. The choice of storage solution depends on factors such as data volume, access requirements, and budget.Data disposal tools facilitate the secure and permanent deletion of data when its retention period expires.
These tools often employ methods like data wiping or physical destruction of storage media to prevent data recovery. A company handling sensitive customer information uses data disposal tools to securely erase data from hard drives before disposing of them.
Comparison of Data Retention Software and Tools
A variety of software and tools are available to support data retention efforts. The choice of the right tool depends on the specific needs of the organization, considering factors like the volume of data, the types of data, compliance requirements, and budget constraints. Below is a comparison of some common categories of data retention tools.* Data Archiving Software:
Features
Data archiving software focuses on moving inactive data to a separate storage location while retaining its accessibility. Features include data compression, indexing, search capabilities, and integration with various data sources.
Pricing
Pricing models vary, ranging from subscription-based fees to perpetual licenses. The cost depends on the features offered, the volume of data archived, and the number of users.
Ease of Use
User-friendliness varies among different vendors. Some solutions offer intuitive interfaces and automated workflows, while others require more technical expertise for setup and management.
Examples
Veritas Enterprise Vault, Micro Focus Retain, and Mimecast Cloud Archive.
Backup and Disaster Recovery Software
Features
These tools focus on creating copies of data for recovery purposes. They often include features like automated backup scheduling, data deduplication, and disaster recovery planning.
Pricing
Pricing is typically based on the amount of data backed up, the number of servers or endpoints, and the features included.
Ease of Use
Many backup solutions offer simplified interfaces and automated processes, making them relatively easy to use.
Examples
Veeam Backup & Replication, Commvault, and Acronis Cyber Protect.
Cloud Storage Solutions
Features
Cloud storage providers offer scalable and cost-effective storage options for both active and archived data. Features include data encryption, access controls, and data replication for redundancy.
Pricing
Cloud storage is often priced based on storage capacity, data transfer rates, and the level of service chosen.
Ease of Use
Cloud storage solutions are generally easy to set up and manage, with user-friendly interfaces and automated data management features.
Examples
Amazon S3, Microsoft Azure Blob Storage, and Google Cloud Storage.
Data Loss Prevention (DLP) Software
Features
DLP software monitors and controls data in use, in motion, and at rest to prevent sensitive data from leaving the organization. Features include data classification, policy enforcement, and incident response.
Pricing
Pricing depends on the number of users, the features offered, and the level of support.
Ease of Use
DLP solutions can be complex to configure and manage, requiring specialized knowledge and ongoing tuning.
Examples
McAfee DLP, Symantec DLP, and Digital Guardian.
Data Disposal Tools
Features
These tools securely erase data from storage media. They often use data wiping techniques or physical destruction methods.
Pricing
Pricing can range from free, open-source tools to paid enterprise solutions.
Ease of Use
Data wiping tools are generally straightforward to use, but physical destruction requires specialized equipment.
Examples
Blancco Drive Eraser, DBAN (Darik’s Boot and Nuke), and ShredIt.The selection process for data retention software and tools should include a thorough evaluation of each solution’s capabilities, cost, and ease of integration with existing IT infrastructure. The organization must assess its specific data retention requirements, including compliance regulations, data volume, and security needs, to determine the best fit.
Integrating Data Retention Tools with Existing IT Infrastructure and Security Systems
Integrating data retention tools into the existing IT infrastructure and security systems is essential for ensuring seamless operation, data protection, and regulatory compliance. This integration involves several key considerations.* Network and Storage Infrastructure: Data retention tools must be compatible with the existing network and storage infrastructure. This may involve configuring network connections, storage locations, and access permissions. Integration with existing SANs, NAS devices, or cloud storage services is often required.
Security Systems
Data retention tools should integrate with security systems, such as firewalls, intrusion detection systems, and access control mechanisms. This ensures that data is protected from unauthorized access and data breaches.
Data Classification and Tagging
Implementing a data classification and tagging system enables automated data retention policies. This involves classifying data based on its sensitivity, business value, and regulatory requirements. Data retention tools can then use these classifications to apply the appropriate retention rules.
Identity and Access Management (IAM)
Integrating with IAM systems allows organizations to control access to archived data based on user roles and permissions. This ensures that only authorized personnel can access sensitive information.
Logging and Auditing
All data retention activities, including data archiving, backup, and disposal, should be logged and audited. This provides a record of data lifecycle events and facilitates compliance audits.
Workflow Automation
Automating data retention workflows can streamline processes and reduce manual effort. This includes automating data archiving, backup, and disposal tasks based on predefined rules and schedules.
Regular Testing and Validation
Regular testing and validation of data retention processes are critical to ensure that data is being retained and disposed of correctly. This involves testing data recovery procedures, verifying data integrity, and validating disposal methods.By carefully considering these factors, organizations can effectively integrate data retention tools into their IT infrastructure and security systems, thereby improving data management, compliance, and security.
Closing Notes
In conclusion, crafting a data retention policy for compliance is a multifaceted process that demands careful consideration of legal, operational, and technological aspects. By following the guidelines Artikeld in this comprehensive guide, organizations can establish a strong foundation for effective data management, mitigate risks, and maintain compliance with evolving regulations. Remember, a well-defined policy is not merely a legal requirement; it is a strategic asset that can significantly enhance your organization’s efficiency, security, and overall success.
Expert Answers
What is the primary purpose of a data retention policy?
The primary purpose is to ensure that data is retained only for as long as necessary to meet legal, regulatory, and business requirements, while minimizing the risk of data breaches and non-compliance.
How often should a data retention policy be reviewed and updated?
A data retention policy should be reviewed and updated at least annually, or more frequently if there are changes in regulations, business needs, or technology.
What are the potential consequences of failing to comply with data retention regulations?
Consequences can include significant financial penalties, legal action, reputational damage, and loss of customer trust.
Does a data retention policy apply to all types of data?
Yes, a comprehensive data retention policy should cover all types of data held by an organization, including electronic and physical records, regardless of format or location.