Securing cloud access is paramount in today’s interconnected digital landscape. This guide delves into the intricacies of configuring a Virtual Private Network (VPN) gateway for secure cloud connectivity, a critical component for protecting sensitive data and maintaining a robust network infrastructure. Understanding the underlying principles, protocols, and configurations is essential for organizations seeking to leverage the benefits of cloud computing while mitigating potential security risks.
We will explore the fundamental concepts of VPN gateways, including the various protocols available and their respective strengths and weaknesses. Furthermore, the guide will examine the prerequisites for secure cloud access, the selection of appropriate VPN gateway solutions, and the critical network topology considerations. The core of this guide focuses on providing step-by-step instructions for configuring a VPN gateway, integrating it with major cloud platforms, and implementing security best practices to ensure a secure and reliable connection.
VPN Gateway Fundamentals
A Virtual Private Network (VPN) gateway serves as a crucial intermediary, enabling secure and private access to a network, often the cloud. It functions by establishing an encrypted tunnel, protecting data transmitted between the user’s device and the destination network. This process ensures confidentiality and integrity of the data, mitigating risks associated with eavesdropping and data breaches. The core principles revolve around encryption, authentication, and secure tunneling.
Core Principles of a VPN Gateway
The primary function of a VPN gateway is to create a secure connection. This involves several core principles that work in concert.
- Encryption: Data is scrambled using cryptographic algorithms, rendering it unreadable to unauthorized parties. Encryption protocols like Advanced Encryption Standard (AES) are commonly used, providing robust security. The strength of the encryption depends on the key length, with longer keys offering greater protection. For example, AES-256 uses a 256-bit key, which is considered highly secure.
- Authentication: This process verifies the identity of the user and the VPN gateway. It ensures that only authorized users can access the network. Authentication methods include username/password combinations, digital certificates, and multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple forms of verification.
- Secure Tunneling: A secure tunnel is established to encapsulate the data packets, protecting them from interception. This tunnel is created through a VPN protocol, which defines the rules and methods for secure communication. Protocols such as IPSec and OpenVPN create this tunnel.
- Key Exchange: This is the process of securely exchanging encryption keys between the client and the gateway. Protocols like Diffie-Hellman (DH) and Elliptic-curve Diffie-Hellman (ECDH) are used to establish a shared secret key without transmitting the key itself.
- Routing and Forwarding: The VPN gateway acts as a router, directing network traffic between the user’s device and the cloud network. It determines the optimal path for data packets to travel, ensuring efficient and reliable communication.
Different VPN Protocols
Several VPN protocols exist, each with its strengths and weaknesses. The choice of protocol depends on factors such as security requirements, performance needs, and compatibility considerations. Each protocol employs distinct cryptographic algorithms and methods for establishing and maintaining the secure tunnel.
Below is a table comparing several VPN protocols, including their advantages and disadvantages:
| Protocol | Description | Advantages | Disadvantages |
|---|---|---|---|
| IPSec (Internet Protocol Security) | A suite of protocols that secures IP communications by authenticating and encrypting each IP packet of a communication session. It operates at the network layer (Layer 3) of the OSI model. |
|
|
| OpenVPN | An open-source VPN protocol that uses SSL/TLS for key exchange and data encryption. It offers flexibility and strong security. It operates at the transport layer (Layer 4) of the OSI model. |
|
|
| WireGuard | A relatively new and modern VPN protocol that aims to be faster, simpler, and more secure than existing solutions. It uses a streamlined cryptographic design. |
|
|
| SSTP (Secure Socket Tunneling Protocol) | A VPN protocol developed by Microsoft that uses the HTTPS protocol to tunnel traffic. It’s primarily used in Windows environments. |
|
|
Cloud Access Prerequisites
Securing access to cloud resources is paramount for maintaining data confidentiality, integrity, and availability. Establishing robust prerequisites is the first step in building a secure cloud environment. These prerequisites encompass several key areas, including identity and access management, network security, and endpoint protection. Failing to address these foundational elements can expose cloud resources to significant risks, including unauthorized access, data breaches, and service disruptions.
Essential Requirements for Secure Cloud Access
Meeting the essential requirements for secure cloud access involves a multi-layered approach. This includes establishing strong authentication, implementing network segmentation, and enforcing robust endpoint security policies. These elements work in concert to protect cloud resources from various threats.
- Strong Authentication and Authorization: Implementing robust authentication mechanisms is the cornerstone of secure cloud access. This involves verifying user identities and granting them appropriate permissions.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a one-time code generated by a mobile app or sent via SMS.
This significantly reduces the risk of unauthorized access, even if an attacker compromises a user’s password. For example, a study by Microsoft found that MFA can block 99.9% of account compromise attacks.
- Role-Based Access Control (RBAC): RBAC assigns permissions based on a user’s role within the organization. This ensures that users only have access to the resources they need to perform their jobs, minimizing the potential impact of a security breach. For instance, a cloud administrator might have full access to all resources, while a developer might only have access to development environments.
- Regular Auditing and Monitoring: Regularly reviewing and monitoring access logs is crucial for detecting and responding to potential security incidents. This includes identifying unusual login attempts, unauthorized access attempts, and privilege escalation. Auditing also helps ensure compliance with security policies and regulations.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a one-time code generated by a mobile app or sent via SMS.
- Network Segmentation: Dividing the cloud environment into logical segments isolates critical resources and limits the blast radius of potential security breaches.
- Virtual Private Clouds (VPCs): VPCs provide isolated networks within the cloud, allowing organizations to control their network configuration and security. This includes defining subnets, routing tables, and security groups.
- Micro-segmentation: This involves segmenting the network at a granular level, often down to individual workloads or applications. This allows for more precise control over network traffic and can significantly reduce the impact of a security breach.
- Intrusion Detection and Prevention Systems (IDS/IPS): Deploying IDS/IPS within the cloud environment helps detect and prevent malicious activity, such as unauthorized access attempts and malware infections. These systems analyze network traffic for suspicious patterns and can automatically block or alert administrators to potential threats.
- Endpoint Security: Securing endpoints, such as laptops, desktops, and mobile devices, is critical for preventing malware infections and unauthorized access to cloud resources.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced threat detection and response capabilities, including real-time monitoring, behavioral analysis, and automated remediation. They can detect and respond to sophisticated threats that may bypass traditional security measures.
- Device Management: Implementing a robust device management strategy, including patching, configuration management, and device enrollment, is crucial for maintaining endpoint security. This ensures that devices are up-to-date with the latest security patches and configured according to organizational policies.
- Secure Remote Access: Secure remote access solutions, such as VPNs, enable authorized users to securely access cloud resources from remote locations. These solutions encrypt network traffic and enforce access controls to protect against unauthorized access.
Importance of Strong Authentication Methods
Strong authentication methods are crucial for verifying user identities and preventing unauthorized access to cloud resources. Weak authentication practices, such as relying solely on passwords, are easily compromised by attackers through techniques like phishing, brute-force attacks, and credential stuffing. Implementing strong authentication methods significantly enhances security posture.
- Multi-Factor Authentication (MFA): MFA significantly increases the security of cloud access by requiring users to provide multiple forms of authentication. This typically involves something the user knows (password), something the user has (a mobile device or security key), and/or something the user is (biometrics). Even if an attacker obtains a user’s password, they will still need to bypass the additional authentication factor to gain access.
For example, a study by Google found that enabling MFA on user accounts reduced the number of compromised accounts by 99.9%.
- Password Policies: Enforcing strong password policies, such as requiring complex passwords, regular password changes, and preventing the reuse of old passwords, is essential for protecting user accounts. These policies help to mitigate the risk of password-related attacks, such as brute-force and dictionary attacks.
- Adaptive Authentication: Adaptive authentication dynamically adjusts the authentication process based on factors such as the user’s location, device, and behavior. This can involve prompting for additional authentication factors when a user is logging in from an unfamiliar location or device. This approach enhances security by continuously assessing the risk associated with each login attempt.
- Biometric Authentication: Biometric authentication, such as fingerprint scanning and facial recognition, offers a high level of security by verifying user identity based on unique biological characteristics. This method is resistant to many forms of attack, such as password theft and phishing.
Role of Firewalls in Cloud Environments
Firewalls play a critical role in securing cloud environments by controlling network traffic and preventing unauthorized access to resources. They act as a barrier between the cloud environment and the external network, filtering traffic based on predefined rules. The proper configuration and management of firewalls are essential for maintaining a secure cloud infrastructure.
- Network Segmentation: Firewalls enable network segmentation, which involves dividing the cloud environment into logical zones or subnets. This allows organizations to isolate critical resources and limit the impact of security breaches. For example, a firewall can be configured to allow only specific traffic to flow between a web server and a database server, preventing unauthorized access to the database.
- Traffic Filtering: Firewalls filter network traffic based on predefined rules, such as source and destination IP addresses, ports, and protocols. This allows organizations to block malicious traffic, such as denial-of-service (DoS) attacks and unauthorized access attempts. Firewalls can also be configured to inspect traffic for specific content, such as malware and phishing attempts.
- Intrusion Prevention: Some firewalls include intrusion prevention system (IPS) capabilities, which actively monitor network traffic for malicious activity and automatically block or quarantine suspicious traffic. This helps to protect against a wide range of threats, including malware, botnets, and zero-day exploits.
- Centralized Management: Firewalls can be managed centrally, allowing organizations to easily configure and monitor firewall rules across multiple cloud instances. This simplifies security management and ensures consistent security policies across the entire cloud environment.
Selecting a VPN Gateway Solution
Choosing the right VPN gateway is critical for secure and efficient cloud access. The selection process involves evaluating various solutions based on factors such as performance, cost, security features, and compatibility with the chosen cloud platform. A well-chosen gateway ensures data confidentiality, integrity, and availability while optimizing network performance. This section delves into the comparison of different VPN gateway solutions and the key considerations for making an informed decision.
Comparing VPN Gateway Solutions
Different VPN gateway solutions cater to varying needs and budgets. These solutions can be broadly categorized into hardware-based, software-based, and cloud-based options. Each approach presents distinct advantages and disadvantages concerning deployment, management, and cost. Understanding these differences is crucial for selecting the most appropriate solution.
- Hardware-Based VPN Gateways: These are physical appliances designed specifically for VPN functionality. They offer high performance and dedicated processing power, making them suitable for high-bandwidth environments. However, they require upfront investment in hardware, physical space, and ongoing maintenance. Examples include appliances from Cisco, Juniper Networks, and Fortinet.
- Software-Based VPN Gateways: These solutions run on general-purpose servers or virtual machines. They provide flexibility in terms of deployment and scalability, allowing organizations to leverage existing infrastructure. They often offer cost savings compared to hardware appliances, but performance can be limited by the underlying hardware resources. Examples include open-source solutions like OpenVPN and commercial software from companies like SonicWall.
- Cloud-Based VPN Gateways: These are managed services offered by cloud providers or third-party vendors. They eliminate the need for on-premises hardware and offer scalability, ease of management, and integration with cloud services. They typically operate on a pay-as-you-go pricing model. Examples include AWS Site-to-Site VPN, Azure VPN Gateway, and solutions from providers like Perimeter 81 and NordLayer.
Factors to Consider When Choosing a VPN Gateway
Selecting the optimal VPN gateway involves a comprehensive evaluation of several critical factors. These considerations ensure that the chosen solution aligns with the organization’s security requirements, performance needs, and budget constraints. These factors include performance, security features, cost, scalability, compatibility, and ease of management.
- Performance: The VPN gateway’s throughput and latency significantly impact user experience. Consider the expected bandwidth usage, the number of concurrent users, and the geographical distribution of users. Hardware-based solutions often provide superior performance compared to software-based options, especially in high-traffic scenarios. Cloud-based solutions offer varying performance levels depending on the provider and the chosen service tier.
- Security Features: Robust security features are paramount for protecting data in transit. The gateway should support strong encryption protocols (e.g., AES-256), authentication methods (e.g., pre-shared keys, certificates), and security protocols (e.g., IPsec, SSL/TLS). Additional features like intrusion detection/prevention systems (IDS/IPS) and firewall capabilities enhance security posture.
- Cost: Total cost of ownership (TCO) includes hardware or software costs, licensing fees, maintenance expenses, and operational costs. Cloud-based solutions often have lower upfront costs but can incur higher long-term expenses depending on usage. Hardware appliances necessitate significant initial investment but may offer lower ongoing costs for high-bandwidth environments.
- Scalability: The ability to scale the VPN gateway to accommodate increasing user demands and data traffic is essential. Cloud-based solutions typically offer the best scalability, allowing organizations to easily adjust resources as needed. Software-based solutions offer good scalability with the appropriate hardware resources. Hardware appliances have fixed capacity and may require hardware upgrades for expansion.
- Compatibility: The VPN gateway must be compatible with the organization’s existing infrastructure, including cloud platforms, operating systems, and network devices. Ensure the gateway supports the necessary VPN protocols and encryption algorithms to integrate seamlessly with the cloud environment. Verify compatibility with the chosen cloud provider (e.g., AWS, Azure, Google Cloud).
- Ease of Management: A user-friendly interface and efficient management tools are crucial for simplifying configuration, monitoring, and troubleshooting. Cloud-based solutions often provide intuitive dashboards and automated management features. Software-based solutions may require more technical expertise for configuration and maintenance. Hardware appliances can vary in terms of management complexity depending on the vendor.
VPN Gateway Solution Comparison Chart
The following table provides a comparison of three VPN gateway solutions, highlighting their key features, pricing models, and supported cloud platforms. This comparative analysis assists in the decision-making process by presenting a concise overview of each solution’s capabilities. Note that pricing information is subject to change and should be verified with the respective vendors.
| Feature | Hardware-Based (Example: Cisco ASA 5500 Series) | Software-Based (Example: OpenVPN Access Server) | Cloud-Based (Example: AWS Site-to-Site VPN) |
|---|---|---|---|
| Key Features | High performance, dedicated hardware, strong security features (firewall, IPS), VPN protocols (IPsec, SSL/TLS) | Flexible deployment (on-premises, cloud), open-source option available, VPN protocols (OpenVPN, IPsec), user authentication | Managed service, scalable, integrates with AWS services, VPN protocols (IPsec), pay-as-you-go pricing |
| Pricing | Upfront hardware cost, software licensing fees, maintenance contracts | Subscription-based licensing (per user or concurrent connection), hardware costs if self-hosted | Pay-as-you-go (hourly or monthly), data transfer charges |
| Supported Cloud Platforms | Generally cloud-agnostic, can connect to any cloud platform supporting VPN connections | Cloud-agnostic, can connect to any cloud platform supporting VPN connections | Primarily designed for AWS, can connect to other cloud platforms through compatible VPN gateways |
| Scalability | Limited by hardware capacity, requires hardware upgrades | Scalable based on underlying hardware resources | Highly scalable, automatically adjusts resources |
| Management | Requires dedicated IT staff, often complex configuration | Requires IT staff, can be managed through a web interface or command line | Simplified management via AWS console, automated updates |
Network Topology Considerations
Configuring a VPN gateway for cloud access necessitates careful consideration of network topology. The chosen topology significantly impacts performance, security, and cost-effectiveness. Understanding the various options and their respective advantages and disadvantages is crucial for designing a robust and scalable cloud access solution. This section explores common network topologies suitable for VPN cloud access, providing a detailed examination of their characteristics and applicability.Selecting the appropriate network topology is a critical decision, as it directly influences the efficiency and security of cloud access.
The topology dictates how traffic flows between on-premises networks and the cloud, impacting latency, bandwidth utilization, and overall resilience. Therefore, a thorough evaluation of the requirements is essential before making a selection.
Common Network Topologies for VPN Cloud Access
Several network topologies are commonly employed for VPN cloud access, each with its own set of trade-offs. Understanding these topologies enables informed decision-making based on specific organizational needs.
- Hub-and-Spoke: This is a centralized topology where all on-premises networks (spokes) connect to a central VPN gateway in the cloud (hub). All traffic between spokes must traverse the hub. This model is well-suited for organizations with a central cloud presence and a need to control all traffic flows.
- Full Mesh: In a full mesh topology, each on-premises network connects directly to every other on-premises network and the cloud. This results in the highest level of redundancy and the lowest latency between sites. However, it can be complex and expensive to implement, especially with a large number of sites.
- Partial Mesh: This topology represents a compromise between hub-and-spoke and full mesh. Some sites connect directly to each other, while others connect through a central hub or a limited number of intermediate sites. This can be a cost-effective solution when full mesh redundancy is not required, or when some sites require higher bandwidth than others.
- Transit Network: In this model, a dedicated network acts as a transit point for VPN traffic. This is particularly useful in complex environments with multiple cloud providers or regions. The transit network simplifies routing and management by centralizing connectivity.
Hub-and-Spoke VPN Topology Diagram and Description
The hub-and-spoke topology is a popular choice for its simplicity and centralized management. The following diagram illustrates this topology.
Diagram Description:
The diagram depicts a hub-and-spoke VPN topology connecting several on-premises networks to a cloud environment. At the center, we have the ‘Cloud VPN Gateway’ (the hub), representing a virtual appliance within the cloud provider’s infrastructure. Connected to this hub are multiple ‘On-Premise Networks’ (spokes). Each spoke is a distinct network location, represented by a network icon with a label.
A secure VPN tunnel, indicated by a line, connects each on-premise network to the Cloud VPN Gateway. The lines represent encrypted communication channels. Arrows within the lines show the direction of data flow. The diagram explicitly shows the flow of traffic: all traffic from one spoke must first travel to the Cloud VPN Gateway before reaching another spoke or resources within the cloud.
Finally, the diagram includes a connection to the ‘Internet’, showing that the cloud gateway also provides access to the public internet. This design allows for centralized management of access controls and security policies.
Selecting the Most Appropriate Topology Based on Requirements
The optimal VPN topology is contingent upon specific cloud access requirements. Careful analysis of several factors is crucial to making the right choice.
- Number of Sites: The number of on-premises networks significantly impacts the complexity and cost of implementation. A hub-and-spoke model is often suitable for a moderate number of sites, while a full mesh might become unwieldy with a large number.
- Bandwidth Requirements: High-bandwidth applications or inter-site communication demands might necessitate a full mesh or partial mesh topology to avoid bottlenecks at a central hub. For instance, a company with several geographically dispersed offices that frequently share large files would likely benefit from a topology that minimizes latency between those offices.
- Security Requirements: Organizations with stringent security needs might prefer a hub-and-spoke model to enforce centralized security policies and monitor traffic flow. Centralized control can simplify security audits and compliance.
- Cost Considerations: Full mesh topologies are typically more expensive to implement and maintain than hub-and-spoke or partial mesh models. Costs associated with VPN gateway licenses, bandwidth charges, and ongoing management should be carefully evaluated.
- Latency Sensitivity: Applications that are sensitive to latency, such as real-time video conferencing or online gaming, might benefit from a full mesh topology or a partial mesh topology, allowing direct connections between sites to minimize delays.
- Redundancy and High Availability: If high availability is critical, the topology should incorporate redundancy at the VPN gateway level. A full mesh topology provides the highest level of redundancy. Consider the use of multiple VPN gateways in the cloud to provide failover capabilities.
Configuration Steps: Initial Setup
Configuring a VPN gateway for cloud access involves a series of carefully orchestrated steps. This process establishes a secure and reliable connection between your on-premises network and your cloud environment. The initial setup lays the foundation for secure data transfer, user authentication, and ongoing management. A thorough understanding of these initial steps is critical for the successful deployment and maintenance of the VPN gateway.
Network Interface Configuration for Cloud Access
Network interface configuration is a crucial step in enabling communication between the VPN gateway and both the on-premises and cloud networks. This involves assigning IP addresses, configuring routing, and ensuring proper network connectivity. Accurate configuration is essential for seamless data transfer and secure access to cloud resources.
Configuring network interfaces typically involves the following steps:
- Identifying Network Interfaces: The first step involves identifying the physical or virtual network interfaces available on the VPN gateway. These interfaces will connect to the on-premises network and the cloud provider’s network. For example, a gateway might have two interfaces: eth0 for the local network (e.g., 192.168.1.0/24) and eth1 for the cloud provider’s network (e.g., 10.0.0.0/16).
- Assigning IP Addresses: Each network interface must be assigned a unique IP address within its respective network segment. This includes configuring the IP address, subnet mask, and default gateway. For the example above, eth0 might be assigned 192.168.1.1 with a subnet mask of 255.255.255.0, and eth1 might be assigned a public IP address provided by the cloud provider, or a private IP address within the cloud network (e.g., 10.0.0.5).
- Configuring Routing: Routing configuration is vital for directing traffic between the on-premises network, the VPN gateway, and the cloud network. This involves setting up routing tables that specify how packets should be forwarded based on their destination IP addresses. The VPN gateway needs to know how to route traffic destined for the cloud network through the VPN tunnel. For example, a static route might be configured to forward all traffic destined for the 10.0.0.0/16 network through the eth1 interface, which connects to the cloud.
- Setting Up DNS Resolution: DNS resolution is necessary for the VPN gateway to resolve domain names to IP addresses. This enables the gateway to communicate with other servers and services in the cloud environment using domain names. The gateway might be configured to use the DNS servers provided by the cloud provider or use internal DNS servers in the on-premises network.
- Firewall Configuration: Firewall rules must be configured to allow traffic to pass through the VPN gateway. These rules define which traffic is permitted or denied based on source and destination IP addresses, ports, and protocols. For example, the firewall must allow incoming VPN traffic (e.g., IPSec traffic on UDP ports 500 and 4500) from the cloud provider’s network and also permit traffic from the on-premises network to the cloud network.
Initial User Authentication and Authorization Setup
Establishing robust user authentication and authorization mechanisms is paramount to securing access to cloud resources. This involves verifying the identity of users attempting to connect to the VPN gateway and granting them appropriate permissions. Proper authentication and authorization prevent unauthorized access and ensure data confidentiality and integrity.
Setting up initial user authentication and authorization typically involves these key components:
- Authentication Methods: The selection of an appropriate authentication method is the first step. Common methods include:
- Pre-shared Keys (PSK): This method uses a shared secret key that must be configured on both the VPN gateway and the client devices. It is simpler to configure but less secure than other methods, as the key must be manually distributed.
- Digital Certificates: Digital certificates provide a more secure authentication method by using public key infrastructure (PKI). Certificates are issued by a trusted Certificate Authority (CA) and are used to verify the identity of both the VPN gateway and the client devices.
- Username/Password with Multi-Factor Authentication (MFA): This involves the use of a username and password, often combined with a second factor of authentication, such as a one-time password (OTP) generated by an authenticator app or a hardware token. This significantly enhances security by requiring multiple forms of verification.
- User Accounts and Credentials: User accounts must be created within the VPN gateway configuration. Each account requires a unique username and password, or a digital certificate associated with the user. The creation process often involves defining the authentication method and associating it with the user account.
- Authorization and Access Control: Once a user is authenticated, authorization determines the resources they are permitted to access. This involves defining access control policies that specify which users or groups of users have access to specific cloud resources, such as virtual machines, databases, or file storage. These policies are typically enforced through access control lists (ACLs) or role-based access control (RBAC).
- Integration with Existing Authentication Systems: In many environments, it is beneficial to integrate the VPN gateway with existing authentication systems, such as Active Directory or LDAP. This allows users to authenticate using their existing credentials and simplifies user management. Integration often involves configuring the VPN gateway to communicate with the authentication server and validate user credentials against the existing user directory.
- Testing and Verification: After the configuration, it is critical to test the authentication and authorization mechanisms to ensure they are working correctly. This involves attempting to connect to the VPN gateway with various user accounts and verifying that access is granted or denied as expected based on the defined policies. The testing phase also includes verifying that multi-factor authentication is functioning as intended.
Configuration Steps: Protocol-Specific Settings
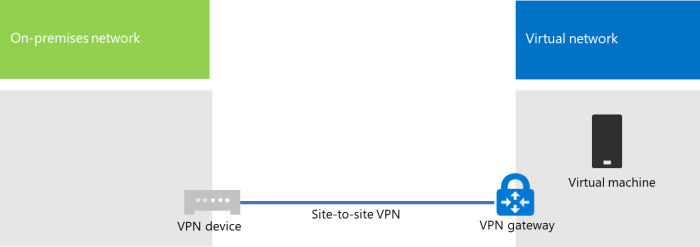
Configuring a VPN gateway for cloud access involves several crucial steps, including protocol-specific settings. This section delves into the detailed configuration of a widely used VPN protocol, IPSec, providing insights into security parameters, encryption settings, and practical code examples. IPSec, or Internet Protocol Security, is a suite of protocols designed to secure IP communications by authenticating and encrypting each IP packet of a communication session.
Its robust security features make it a popular choice for establishing secure connections between networks, including cloud environments.
IPSec Configuration Details
IPSec configuration necessitates careful consideration of several parameters. These settings directly impact the security and performance of the VPN tunnel. The configuration typically involves defining security associations (SAs), which establish the cryptographic parameters for secure communication. These parameters are negotiated between the VPN peers.To illustrate the IPSec configuration process, consider the example of configuring an IPSec VPN tunnel using the strongSwan software suite, a widely adopted open-source IPSec implementation.
The configuration will involve defining the cryptographic algorithms, authentication methods, and key exchange mechanisms.The following code block presents an example of a strongSwan configuration file, `ipsec.conf`, to establish an IPSec tunnel between a local network and a cloud environment. This configuration uses the `ikev2` protocol for key exchange, `aes256` for encryption, and `sha256` for hashing.“`config setup # NAT Traversal charon.plugins.attr.default_dns = 8.8.8.8 unique = noconn cloud-vpn keyexchange=ikev2 ike=aes256-sha256-modp3072! esp=aes256-sha256! left=192.168.1.100 # Local gateway public IP leftid=vpn.local.example.com # Local gateway FQDN or IP leftsubnet=192.168.1.0/24 # Local subnet right=203.0.113.100 # Cloud gateway public IP rightid=cloud.example.com # Cloud gateway FQDN or IP rightsubnet=10.0.0.0/16 # Cloud subnet authby=psk presharedkey=verysecretkey auto=start“`The configuration defines the following parameters:* `config setup`: Global settings for strongSwan.
`charon.plugins.attr.default_dns = 8.8.8.8`
Specifies the default DNS server for NAT traversal.
`unique = no`
Allows multiple connections with the same peer.
`conn cloud-vpn`
Defines the connection named `cloud-vpn`.
`keyexchange=ikev2`
Specifies the Internet Key Exchange version 2 (IKEv2) protocol for key exchange. IKEv2 offers improved security and performance compared to older IKEv1.
`ike=aes256-sha256-modp3072!`
Defines the IKE phase 1 proposal.
`aes256`
Advanced Encryption Standard with a 256-bit key for encryption.
`sha256`
Secure Hash Algorithm 256 for hashing.
`modp3072`
Diffie-Hellman group 15 (3072-bit) for key exchange.
`!`
Indicates the proposal is mandatory.
`esp=aes256-sha256!`
Defines the Encapsulating Security Payload (ESP) phase 2 proposal.
`aes256`
Advanced Encryption Standard with a 256-bit key for encryption.
`sha256`
Secure Hash Algorithm 256 for integrity protection.
`!`
Indicates the proposal is mandatory.
`left=192.168.1.100`
Specifies the public IP address of the local VPN gateway.
`leftid=vpn.local.example.com`
Identifies the local gateway using its fully qualified domain name (FQDN). This is a more secure method than using the IP address, as it prevents IP spoofing attacks.
`leftsubnet=192.168.1.0/24`
Defines the local network subnet.
`right=203.0.113.100`
Specifies the public IP address of the cloud VPN gateway.
`rightid=cloud.example.com`
Identifies the cloud gateway using its FQDN.
`rightsubnet=10.0.0.0/16`
Defines the cloud network subnet.
`authby=psk`
Specifies the use of a pre-shared key (PSK) for authentication.
`presharedkey=verysecretkey`
Sets the pre-shared key, which must be the same on both VPN gateways.
`auto=start`
Configures the VPN tunnel to automatically start when the strongSwan service is initiated.The choice of encryption algorithms and key lengths directly affects the security of the VPN tunnel. For instance, using AES-256 provides a significantly higher level of security compared to AES-128 due to the larger key size, making it more resistant to brute-force attacks. Similarly, SHA-256 is considered more secure than SHA-1 due to its stronger hashing algorithm.The pre-shared key (PSK) is a critical security component.
A robust PSK should be long, complex, and randomly generated to prevent unauthorized access. Regular key rotation is also a recommended security practice to mitigate the risk of key compromise.After configuring the `ipsec.conf` file, the strongSwan service must be restarted or reloaded for the changes to take effect.To verify the connection status, the command `ipsec statusall` can be used, which displays information about the active security associations and the status of the VPN tunnels.
This information is essential for troubleshooting and ensuring the VPN is operating correctly.
Cloud Platform Integration
Integrating a VPN gateway with cloud platforms is crucial for establishing secure and reliable connectivity between on-premises networks and cloud resources. This integration allows for the secure transfer of data, access to cloud services, and the creation of hybrid cloud environments. The specific configurations required vary depending on the chosen cloud platform, requiring a thorough understanding of each platform’s networking services and VPN gateway compatibility.
This section provides detailed guidance on integrating a VPN gateway with major cloud providers, including AWS, Azure, and Google Cloud.
AWS Integration
AWS offers various services to facilitate VPN gateway integration, primarily through its Virtual Private Cloud (VPC) and related services. The integration process typically involves configuring a Customer Gateway, a Virtual Private Gateway (VGW), and an IPsec tunnel. This approach allows for secure communication between the on-premises network and the AWS cloud resources.The following steps are involved in setting up a VPN connection to AWS:
- Creating a Customer Gateway: The Customer Gateway represents the on-premises VPN gateway. Its configuration requires the public IP address of the on-premises gateway.
- Creating a Virtual Private Gateway: The VGW is a VPN concentrator on the AWS side. It resides within the VPC and is responsible for establishing and managing the VPN connection.
- Creating a Site-to-Site VPN Connection: This step involves associating the VGW with the VPC and configuring the VPN connection parameters, including the Customer Gateway, routing options, and tunnel settings.
- Configuring the VPN Tunnel: This step involves configuring the IPsec tunnel on both the on-premises VPN gateway and the AWS side. This includes specifying the pre-shared key, security protocols, and encryption algorithms.
- Configuring Routing: Routing configurations are essential for directing traffic between the on-premises network and the AWS VPC. This involves setting up route tables to direct traffic destined for the VPC to the VGW and vice versa.
The following screenshot illustrates the AWS Management Console for configuring a Customer Gateway.
Screenshot Description: The screenshot shows the AWS Management Console interface for creating a Customer Gateway. The user is prompted to enter the Customer Gateway’s name and public IP address. The “Routing” option, which determines the routing type, is also presented. This step is essential for AWS to identify the on-premises VPN gateway and establish a secure connection.
The subsequent screenshot showcases the Virtual Private Gateway creation process within the AWS console.
Screenshot Description: The AWS Management Console displays the process of creating a Virtual Private Gateway (VGW). The user is required to specify a name for the VGW. After the VGW is created, it must be attached to the VPC to establish connectivity.
Finally, the screenshot shows the Site-to-Site VPN connection setup, including configuration details such as tunnel options, routing information, and the Customer Gateway settings.
Screenshot Description: This screenshot details the Site-to-Site VPN connection configuration within the AWS console. It showcases the selection of the Virtual Private Gateway, the Customer Gateway, and the routing options. The user can configure the tunnel options, including pre-shared keys and security protocols, to establish a secure IPsec tunnel.
Azure Integration
Azure’s VPN Gateway service facilitates secure connections between on-premises networks and Azure virtual networks. This integration is typically achieved through the creation of a VPN gateway, a local network gateway, and the configuration of a VPN connection.The following steps Artikel the Azure VPN gateway integration process:
- Creating a Virtual Network: A virtual network is created within Azure to host the resources that will be accessible via the VPN connection.
- Creating a VPN Gateway: The VPN gateway is created within the Azure virtual network. It acts as the VPN concentrator, terminating VPN connections from on-premises networks.
- Creating a Local Network Gateway: The local network gateway represents the on-premises network. Its configuration requires the public IP address of the on-premises VPN gateway and the on-premises network address space.
- Creating a Connection: A connection is created between the VPN gateway and the local network gateway. This involves configuring the connection type (e.g., IPsec), shared key, and other security settings.
- Configuring Routing: Routing configurations are essential for directing traffic between the on-premises network and the Azure virtual network. This involves configuring route tables to direct traffic destined for the Azure virtual network to the VPN gateway.
The following screenshot illustrates the Azure portal interface for creating a VPN gateway.
Screenshot Description: The screenshot depicts the Azure portal interface for creating a VPN gateway. The user selects the virtual network and the gateway SKU (performance tier) and configures the public IP address for the VPN gateway. This step establishes the Azure-side endpoint for the VPN connection.
The next screenshot shows the configuration of a Local Network Gateway, which represents the on-premises network.
Screenshot Description: The screenshot showcases the Azure portal interface for creating a Local Network Gateway. The user provides the public IP address of the on-premises VPN gateway and the on-premises network address space. This information allows Azure to route traffic to the on-premises network.
Finally, the screenshot shows the creation of a connection between the VPN gateway and the local network gateway.
Screenshot Description: The screenshot shows the configuration of a VPN connection within the Azure portal. The user selects the VPN gateway, the local network gateway, and the connection type (e.g., IPsec). The pre-shared key and other security settings are also configured during this step, which ensures the secure establishment of the VPN tunnel.
Google Cloud Integration
Google Cloud Platform (GCP) offers Cloud VPN for establishing secure connections between on-premises networks and Google Cloud Virtual Private Cloud (VPC) networks. The integration involves creating a Cloud VPN gateway, a Cloud Router, and configuring an IPsec tunnel.The following steps are typically followed to integrate a VPN gateway with Google Cloud:
- Creating a VPC Network: A VPC network is created within Google Cloud to host the resources that will be accessible via the VPN connection.
- Creating a Cloud VPN Gateway: The Cloud VPN gateway is created within the VPC network. It acts as the VPN concentrator, terminating VPN connections from on-premises networks.
- Creating a Cloud Router: A Cloud Router is created to exchange routing information between the on-premises network and the Google Cloud VPC network.
- Configuring an IPsec Tunnel: This involves configuring the IPsec tunnel on both the on-premises VPN gateway and the Google Cloud side. This includes specifying the pre-shared key, security protocols, and encryption algorithms.
- Configuring Routes: Routing configurations are essential for directing traffic between the on-premises network and the Google Cloud VPC network. This involves configuring custom routes to direct traffic destined for the on-premises network to the Cloud VPN gateway.
The following screenshot depicts the Google Cloud Console interface for creating a Cloud VPN gateway.
Screenshot Description: The screenshot displays the Google Cloud Console interface for creating a Cloud VPN gateway. The user selects the VPC network, the gateway type (e.g., HA VPN or Classic VPN), and the public IP address for the VPN gateway. This sets up the Google Cloud side endpoint for the VPN connection.
The subsequent screenshot demonstrates the configuration of a Cloud Router.
Screenshot Description: The screenshot illustrates the Google Cloud Console interface for creating a Cloud Router. The user specifies the name, region, and the associated VPC network. The Cloud Router facilitates the exchange of routing information using protocols such as BGP.
Finally, the screenshot demonstrates the IPsec tunnel configuration process.
Screenshot Description: The screenshot details the IPsec tunnel configuration within the Google Cloud Console. The user configures the tunnel settings, including the on-premises VPN gateway’s IP address, the pre-shared key, and the security protocols. This step ensures the secure establishment of the IPsec tunnel between the on-premises network and the Google Cloud VPC.
Security Best Practices
Securing a VPN gateway is paramount to protecting cloud resources from unauthorized access, data breaches, and various cyber threats. Implementing robust security measures throughout the configuration and maintenance of the VPN gateway is crucial. This section Artikels the key security best practices, potential vulnerabilities, and mitigation strategies to ensure a secure and reliable cloud access environment.
Authentication and Authorization
Rigorous authentication and authorization mechanisms are fundamental to controlling access to the VPN gateway and subsequently, the cloud resources. Strong authentication verifies the identity of users and devices attempting to connect, while authorization determines what resources they are permitted to access.
- Multi-Factor Authentication (MFA): MFA requires users to provide multiple forms of verification, typically something they know (password), something they have (security token), and something they are (biometric data). Implementing MFA significantly reduces the risk of unauthorized access, even if a password is compromised. For instance, consider a scenario where an attacker obtains a user’s password through phishing. With MFA enabled, the attacker would still need to bypass the second authentication factor (e.g., a one-time code generated by an authenticator app) to gain access.
- Strong Passwords and Password Policies: Enforce strong password policies that mandate the use of complex passwords with a minimum length, and the inclusion of uppercase and lowercase letters, numbers, and special characters. Regular password changes should also be enforced.
- Role-Based Access Control (RBAC): Implement RBAC to grant users only the necessary permissions to perform their job functions. This principle of least privilege limits the potential damage from a compromised account. For example, an administrator might have full access to the VPN gateway configuration, while a regular user might only have access to connect and disconnect from the VPN.
- Regular Audits and Access Reviews: Regularly audit user access and permissions to ensure that they align with current job roles and responsibilities. Conduct periodic access reviews to identify and revoke unnecessary or excessive privileges.
Encryption and Protocols
Secure encryption protocols are essential to protect data transmitted over the VPN tunnel from eavesdropping and tampering. The choice of protocols and the implementation of robust encryption algorithms directly impact the confidentiality and integrity of the data.
- Strong Encryption Algorithms: Utilize strong encryption algorithms such as AES-256 for data encryption and SHA-256 or SHA-384 for hashing. Avoid outdated or weak algorithms like DES or MD5, which are susceptible to known attacks. The selection of encryption algorithms should be based on current industry best practices and recommendations from organizations like NIST.
- Protocol Selection: Choose secure VPN protocols such as IPsec or OpenVPN. IPsec is a suite of protocols that provides confidentiality, integrity, and authentication at the network layer. OpenVPN is a versatile, open-source protocol that offers flexibility in configuration and supports various authentication methods. Avoid older, less secure protocols like PPTP.
- Key Management: Implement a robust key management system to securely generate, store, and rotate encryption keys. Regularly rotate keys to minimize the impact of a potential key compromise. Automated key rotation mechanisms can be integrated into the VPN gateway configuration.
- Perfect Forward Secrecy (PFS): Enable PFS to ensure that even if a session key is compromised, past sessions remain secure. PFS generates a new key for each session, preventing an attacker from decrypting previous sessions using a compromised key.
Network Security
Network security configurations play a vital role in protecting the VPN gateway and the connected cloud resources from external threats. These configurations include firewall rules, intrusion detection systems, and regular monitoring.
- Firewall Rules: Configure strict firewall rules on the VPN gateway to allow only necessary traffic. Only allow traffic from trusted sources and restrict access to specific ports and protocols. For example, if the VPN gateway only needs to allow SSH traffic, then only port 22 should be open, and only from authorized IP addresses.
- Intrusion Detection and Prevention Systems (IDS/IPS): Deploy an IDS/IPS to monitor network traffic for malicious activity. An IDS detects suspicious behavior and alerts administrators, while an IPS can automatically block malicious traffic.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration tests to identify vulnerabilities in the VPN gateway configuration and network infrastructure. These tests should simulate real-world attacks to assess the effectiveness of security measures.
- Network Segmentation: Segment the network to isolate the VPN gateway and cloud resources from other parts of the network. This limits the impact of a security breach. For example, the VPN gateway can be placed in a separate DMZ (demilitarized zone) to isolate it from the internal network.
Configuration Hardening
Hardening the VPN gateway involves configuring it securely by disabling unnecessary services, applying security patches, and monitoring system logs. These actions enhance the overall security posture of the gateway.
- Disable Unnecessary Services: Disable any services on the VPN gateway that are not required for VPN functionality. This reduces the attack surface by eliminating potential entry points for attackers.
- Apply Security Patches: Regularly apply security patches and updates to the VPN gateway software and operating system. Patch management is crucial to address known vulnerabilities and protect against exploitation.
- Monitor System Logs: Implement comprehensive logging and monitoring of system and security events. Analyze logs to detect suspicious activity, identify potential security breaches, and troubleshoot issues.
- Secure Configuration Management: Maintain secure configuration files and implement version control to track changes. Regularly review and audit the configuration to ensure it aligns with security best practices.
Important Security Considerations
The following blockquote highlights the most critical security considerations for VPN gateway configuration.
- Strong Authentication is Mandatory: Always use MFA to prevent unauthorized access.
- Encryption is Non-Negotiable: Implement strong encryption algorithms and protocols to protect data in transit.
- Firewall is Your First Line of Defense: Configure strict firewall rules to control network traffic.
- Regular Monitoring is Critical: Monitor system logs and network traffic to detect and respond to security incidents.
- Patching is Essential: Keep the VPN gateway software and operating system up-to-date with the latest security patches.
Monitoring and Logging
Monitoring and logging are critical components of a robust VPN gateway implementation, providing insights into performance, security posture, and overall health. Effective monitoring allows administrators to proactively identify and address potential issues, ensuring continuous availability and optimal performance of cloud access. Comprehensive logging is essential for security auditing, troubleshooting, and compliance purposes. Neglecting these aspects can lead to undetected vulnerabilities, performance bottlenecks, and difficulties in incident response.
Importance of Monitoring VPN Gateway Performance and Activity
Monitoring VPN gateway performance and activity is paramount for maintaining secure and reliable cloud access. This involves tracking various metrics and events to ensure the gateway operates within acceptable parameters and promptly identifies any anomalies that could indicate a problem. The goals of monitoring include performance optimization, security incident detection, and compliance adherence.
- Performance Optimization: Monitoring bandwidth utilization, latency, and connection stability allows for identifying and resolving performance bottlenecks. For example, if the VPN gateway consistently experiences high latency during peak hours, this indicates a need for scaling the gateway infrastructure or optimizing the underlying network configuration.
- Security Incident Detection: Monitoring connection attempts, failed logins, and unusual traffic patterns helps identify potential security threats, such as brute-force attacks or unauthorized access attempts. Analyzing log data for suspicious activity is crucial for detecting and responding to security incidents promptly.
- Compliance Adherence: Logging and monitoring are essential for meeting regulatory compliance requirements, such as those mandated by HIPAA, GDPR, or PCI DSS. Maintaining detailed logs of user activity, access attempts, and system events provides the necessary audit trails to demonstrate compliance.
Essential Logs to Monitor
Several types of logs provide valuable information for monitoring and troubleshooting VPN gateways. Analyzing these logs allows for a comprehensive understanding of the gateway’s operation and the identification of potential issues.
- Connection Logs: These logs record details about VPN connections, including connection initiation and termination times, source and destination IP addresses, usernames, and connection status. Analyzing connection logs is crucial for tracking user activity and identifying connection-related issues.
- Authentication Logs: Authentication logs document user login attempts, both successful and failed, including timestamps, usernames, and source IP addresses. These logs are essential for detecting unauthorized access attempts and identifying compromised credentials.
- Traffic Logs: Traffic logs capture information about network traffic passing through the VPN gateway, such as source and destination IP addresses, protocols, port numbers, and the volume of data transferred. Analyzing traffic logs helps identify performance bottlenecks, detect suspicious traffic patterns, and monitor bandwidth usage.
- System Logs: System logs record system-level events, such as service starts and stops, configuration changes, and error messages. These logs provide valuable insights into the overall health and stability of the VPN gateway.
- Security Logs: Security logs document security-related events, such as firewall rule violations, intrusion attempts, and security alerts. Analyzing security logs is crucial for identifying and responding to security threats.
Tools and Methods for Monitoring VPN Connections and Traffic
Various tools and methods can be employed to monitor VPN connections and traffic effectively. The selection of appropriate tools and methods depends on the specific VPN gateway solution, the cloud platform used, and the overall monitoring requirements.
- Built-in Monitoring Tools: Many VPN gateway solutions offer built-in monitoring tools that provide real-time performance metrics and log data. These tools often include dashboards that visualize key performance indicators (KPIs), such as bandwidth utilization, connection counts, and latency. Examples include the monitoring dashboards available within the management interfaces of popular VPN solutions like OpenVPN Access Server or Cisco AnyConnect.
- Log Aggregation and Analysis Tools: Log aggregation and analysis tools, such as the ELK Stack (Elasticsearch, Logstash, Kibana), Splunk, and Graylog, can collect, process, and analyze logs from multiple sources, including VPN gateways. These tools provide powerful search, filtering, and visualization capabilities, enabling administrators to identify trends, detect anomalies, and generate reports. For instance, using the ELK stack, administrators can configure Logstash to collect logs from various VPN gateway instances, Elasticsearch to store the processed logs, and Kibana to visualize the data, creating custom dashboards to monitor connection counts, bandwidth usage, and error rates.
- Network Monitoring Tools: Network monitoring tools, such as Nagios, Zabbix, and SolarWinds, can monitor network devices and services, including VPN gateways. These tools can monitor network traffic, measure latency, and detect performance bottlenecks. They often provide alerts and notifications based on predefined thresholds. For example, configuring Nagios to monitor the VPN gateway’s CPU utilization, memory usage, and network interface traffic can proactively alert administrators to potential performance issues.
- Cloud-Specific Monitoring Services: Cloud platforms, such as AWS, Azure, and Google Cloud, offer built-in monitoring services that can be used to monitor VPN gateways deployed within their environments. These services typically provide real-time performance metrics, log data, and alerting capabilities. For instance, in AWS, CloudWatch can be used to monitor the performance of a Site-to-Site VPN connection, tracking metrics such as tunnel up/down status, bytes in/out, and tunnel errors.
- SNMP Monitoring: Simple Network Management Protocol (SNMP) can be used to monitor VPN gateways that support SNMP. SNMP allows administrators to collect performance data and receive alerts from the gateway. SNMP is a widely used protocol for network device monitoring and provides a standardized way to access performance metrics.
Troubleshooting Common Issues
Troubleshooting is a critical aspect of maintaining a VPN gateway, ensuring continuous and secure cloud access. This involves systematically identifying and resolving issues that may arise during the configuration, operation, and maintenance phases. Effective troubleshooting requires a structured approach, leveraging diagnostic tools and techniques to pinpoint the root cause of problems and implement appropriate solutions. Addressing common issues proactively minimizes downtime and ensures the reliability of the VPN connection.
Connectivity Problems and Solutions
Connectivity problems are among the most frequently encountered issues when working with VPN gateways. These problems can manifest in various ways, including inability to establish a connection, intermittent disconnections, or slow data transfer rates. A methodical approach to troubleshooting is crucial to identify the underlying cause and implement effective solutions.
- Firewall Configuration Issues: Firewalls can inadvertently block VPN traffic. This is a common issue, and often the first place to check when connection problems arise.
- Solution: Verify that the firewall rules on both the VPN gateway and the client devices allow the necessary traffic. Ensure that inbound and outbound traffic on UDP ports 500 (ISAKMP), 4500 (NAT-T), and TCP port 1723 (PPTP) are permitted. Also, check for any implicit deny rules that might be blocking traffic.
- Incorrect Network Configuration: Incorrect IP addresses, subnet masks, or routing configurations can prevent the VPN connection from being established.
- Solution: Double-check the IP addresses assigned to the VPN gateway and the client devices. Confirm that the subnet masks are correctly configured and that the routing tables are set up to direct traffic through the VPN tunnel. Verify that the default gateway is correctly specified on both the VPN gateway and the client.
- DNS Resolution Problems: DNS resolution failures can prevent the client from resolving the VPN gateway’s hostname or IP address.
- Solution: Ensure that the client can resolve the VPN gateway’s hostname or IP address. Test DNS resolution by pinging the VPN gateway’s hostname or IP address. If resolution fails, check the DNS server settings on the client and the VPN gateway. Verify that the DNS servers are reachable and functioning correctly.
- MTU (Maximum Transmission Unit) Mismatch: An MTU mismatch can cause fragmentation issues, leading to slow data transfer rates or connection failures.
- Solution: Determine the optimal MTU size for the VPN tunnel by performing a path MTU discovery test. This can be done using the “ping” command with the “df” (don’t fragment) option. For example:
ping -c 1 -s 1472 [VPN Gateway IP Address] -M do
. Adjust the MTU settings on both the VPN gateway and the client devices to match the optimal size. A common starting point is to reduce the MTU by the overhead introduced by the VPN protocol (e.g., 20-100 bytes depending on the protocol).
- Protocol-Specific Issues: Problems can arise with the specific VPN protocols being used, such as IPsec, OpenVPN, or SSTP.
- Solution: For IPsec, check the pre-shared key (PSK) or certificate configuration. Verify that the encryption and hashing algorithms are compatible. For OpenVPN, examine the configuration files for errors and ensure that the server and client configurations match. For SSTP, check for certificate-related issues and ensure that the server certificate is trusted by the client. Consult the specific documentation for each protocol to identify and resolve protocol-specific issues.
Diagnosing and Resolving Authentication Errors
Authentication errors prevent users from successfully connecting to the VPN gateway, which is a common issue. These errors typically arise from incorrect credentials, misconfigured authentication methods, or problems with the authentication server. Diagnosing and resolving authentication errors requires a careful examination of the logs and configurations.
- Incorrect Credentials: The most frequent cause of authentication failures is the use of incorrect usernames or passwords.
- Solution: Verify that the user is entering the correct username and password. Double-check the case sensitivity of the credentials. Reset the user’s password if necessary, and ensure that the password meets the complexity requirements of the VPN gateway.
- Authentication Method Mismatches: Mismatched authentication methods between the VPN gateway and the client can result in authentication failures.
- Solution: Ensure that the authentication method configured on the VPN gateway matches the method configured on the client. For example, if the VPN gateway is configured to use RADIUS authentication, the client must be configured to use RADIUS as well. Verify that the RADIUS server is reachable and functioning correctly.
- Certificate-Related Issues: When using certificate-based authentication, issues with certificates can lead to authentication errors.
- Solution: Verify that the client has the correct certificate installed and that the certificate is trusted by the VPN gateway. Check the certificate’s validity period and ensure that it has not expired. Ensure that the certificate’s common name (CN) matches the hostname or IP address of the VPN gateway.
- Account Lockout: Repeated failed login attempts can lead to account lockout, preventing the user from authenticating.
- Solution: Check the VPN gateway’s logs to determine if the user’s account has been locked out. Unlock the account if necessary. Implement a mechanism to notify users when their accounts are locked out.
- Authentication Server Problems: Problems with the authentication server (e.g., RADIUS, LDAP) can prevent users from authenticating.
- Solution: Verify that the authentication server is reachable and functioning correctly. Check the logs on the authentication server for any errors. Ensure that the VPN gateway is configured correctly to communicate with the authentication server. Test the authentication server independently to verify its functionality.
Advanced Configuration Options
Configuring a VPN gateway for cloud access often involves more than just basic setup. Optimizing performance, ensuring resilience, and tailoring access policies are crucial for a secure and efficient cloud environment. This section explores advanced configuration options that enhance the functionality and security of your VPN gateway, covering high availability, load balancing, and split tunneling.
High Availability and Load Balancing
Ensuring continuous cloud access is critical for business operations. High availability (HA) and load balancing are key strategies to achieve this goal. These configurations minimize downtime and optimize resource utilization by distributing traffic across multiple VPN gateway instances.
- High Availability (HA) Implementation: High availability ensures that a VPN connection remains active even if one gateway fails. This typically involves deploying redundant VPN gateway instances. If the primary gateway becomes unavailable, a secondary gateway automatically takes over, maintaining the connection. The transition, or failover, should be seamless to the end-user.
- Load Balancing Implementation: Load balancing distributes incoming VPN traffic across multiple VPN gateway instances. This approach improves performance by preventing any single gateway from becoming overloaded, thereby reducing latency and enhancing overall throughput. Load balancing can be implemented at the VPN gateway level or through external load balancers.
- Redundancy and Failover Mechanisms: A robust HA setup necessitates redundant hardware and software components. Failover mechanisms are critical. These mechanisms automatically detect failures and initiate the switch to a backup gateway. Heartbeat signals, or keep-alive messages, are commonly used to monitor the status of each gateway. When a heartbeat is missed, the system initiates a failover.
- Load Balancing Algorithms: Various algorithms can be used for load balancing, each with its own advantages.
- Round Robin: Traffic is distributed sequentially to each gateway in a rotating fashion.
- Least Connections: Traffic is directed to the gateway with the fewest active connections.
- Weighted Round Robin: Allows for assigning different weights to gateways based on their capacity.
Split Tunneling Implementation
Split tunneling allows specific traffic to be routed through the VPN tunnel while other traffic bypasses the tunnel and accesses the internet directly. This can optimize performance and bandwidth usage, especially for applications that do not require the security of a VPN connection.
- Traffic Segmentation: Split tunneling requires defining which traffic should traverse the VPN tunnel and which should not. This is typically achieved through access control lists (ACLs) or routing policies.
- Policy-Based Routing: This approach uses routing policies to determine the path of each packet. The policies can be based on source IP addresses, destination IP addresses, ports, or application types.
- ACL Configuration: Access control lists define rules for allowing or denying traffic based on various criteria. For split tunneling, ACLs are used to specify which traffic should be encrypted and sent through the VPN tunnel. For example, traffic destined for the cloud network would be routed through the tunnel, while traffic for the public internet would bypass the tunnel.
- Security Considerations: While split tunneling can improve performance, it also introduces security risks. Traffic that bypasses the VPN tunnel is not protected by the encryption and security measures of the VPN. Therefore, it’s crucial to carefully consider the applications and data that are allowed to bypass the tunnel and to implement appropriate security measures, such as endpoint security, on the devices accessing the internet directly.
High-Availability Architecture Diagram for a VPN Gateway
A high-availability architecture diagram visually represents the components and connections involved in a redundant VPN gateway setup. The diagram helps to understand how the system operates and how failover mechanisms are implemented.
Diagram Description:
The diagram depicts a cloud environment connected to an on-premises network via a VPN. Two VPN gateway instances (Gateway A and Gateway B) are deployed for redundancy. Each gateway is connected to the cloud network via a secure VPN tunnel. A load balancer sits in front of the two VPN gateways. The load balancer distributes incoming VPN traffic between Gateway A and Gateway B.
The load balancer monitors the health of both gateways using heartbeat signals. If Gateway A fails, the load balancer automatically directs all traffic to Gateway B. The on-premises network is connected to the internet via a router. This architecture ensures that if one gateway fails, the other automatically takes over, maintaining VPN connectivity. The diagram also illustrates a monitoring system that tracks the status of the gateways and load balancer, providing alerts in case of any issues.
Key Components and their functions:
- On-Premises Network: The local network where users and resources originate.
- Router: The device that connects the on-premises network to the internet.
- Gateway A and Gateway B (VPN Gateways): Two VPN gateway instances, configured identically, providing redundancy.
- Load Balancer: Distributes incoming VPN traffic across Gateway A and Gateway B. Monitors the health of the gateways and performs failover if one fails.
- Cloud Network: The cloud infrastructure where the resources are hosted.
- VPN Tunnels: Secure connections between the VPN gateways and the cloud network.
- Monitoring System: Monitors the status of all components, including the gateways and the load balancer.
Closing Notes
In conclusion, configuring a VPN gateway for cloud access demands a thorough understanding of VPN fundamentals, network security principles, and cloud platform integration. By carefully considering the various aspects Artikeld in this guide, from protocol selection and configuration to security best practices and troubleshooting, organizations can establish a secure and reliable connection to their cloud resources. Implementing these measures is not merely a technical necessity but a strategic imperative for safeguarding data and ensuring business continuity in the ever-evolving threat landscape.
Query Resolution
What is the primary function of a VPN gateway?
A VPN gateway creates a secure, encrypted tunnel between a private network and a public network (like the internet) or another private network, allowing secure access to cloud resources and protecting data in transit.
What are the main differences between IPSec, OpenVPN, and WireGuard?
IPSec is a mature protocol often used for site-to-site VPNs, known for its robustness. OpenVPN is highly flexible and widely supported, offering strong security. WireGuard is a newer protocol, designed for speed and simplicity, and gaining popularity for its performance.
How does a VPN gateway enhance cloud security?
A VPN gateway encrypts all data transmitted between the user’s network and the cloud, protecting it from eavesdropping and unauthorized access. It also provides secure authentication and authorization, ensuring only authorized users can access cloud resources.
What are the key considerations when selecting a VPN gateway solution?
Consider factors such as supported VPN protocols, scalability, compatibility with cloud platforms, security features, performance, and pricing. Also, consider ease of management and the vendor’s reputation and support.
What is split tunneling, and when is it beneficial?
Split tunneling allows only specific traffic to be routed through the VPN, while other traffic uses the regular internet connection. It can be beneficial for performance and reducing bandwidth usage, but requires careful configuration to avoid security vulnerabilities.