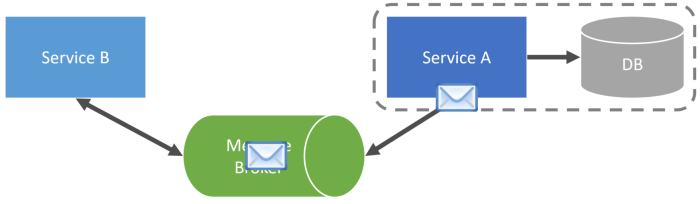
Managing Shared Databases in a Microservices Architecture: Best Practices
Navigating the complexities of data sharing is crucial in a microservices architecture. This article delves into the challenges and opportunities of m...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Navigating the complexities of data sharing is crucial in a microservices architecture. This article delves into the challenges and opportunities of m...
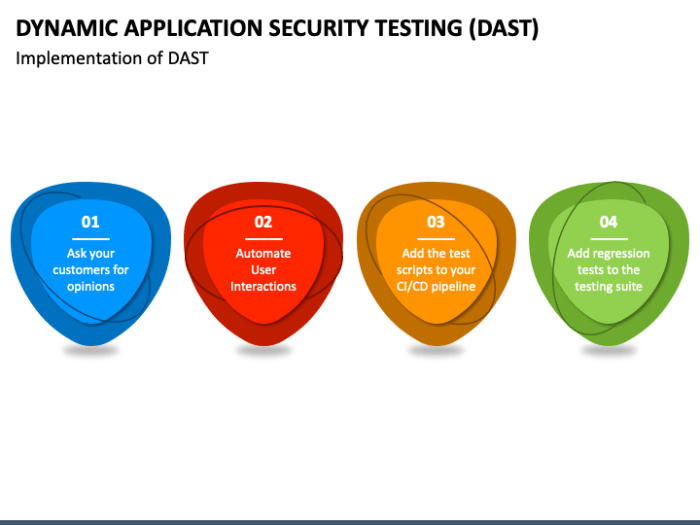
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...

This article provides a comprehensive overview of runtime security for containers, emphasizing its critical role in protecting containerized applicati...
This comprehensive guide delves into the intricacies of OAuth 2.0 and OpenID Connect, explaining their roles in modern authentication and authorizatio...
This article delves into the 'analysis paralysis' anti-pattern, a common pitfall in project planning that can severely impact timelines, budgets, and...

Data lifecycle policies are essential for organizations seeking to effectively manage their data throughout its entire lifespan, from creation to disp...
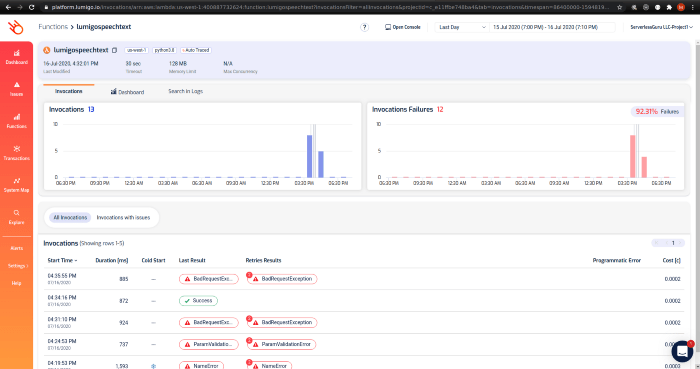
Serverless architectures offer exciting scalability but introduce complexities in observability. This guide provides a comprehensive overview of essen...
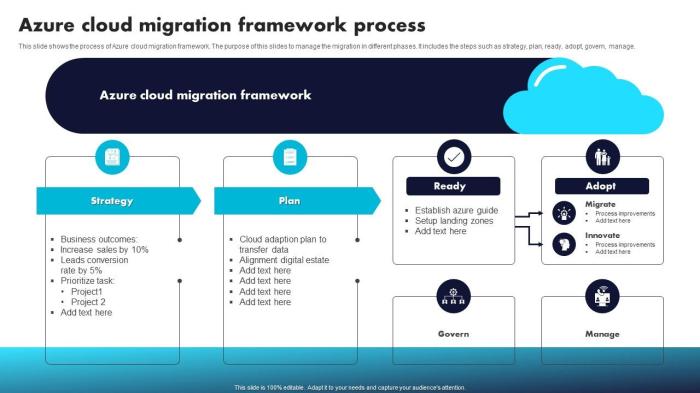
Successfully navigating a cloud migration requires a robust cloud governance framework to mitigate risks and ensure compliance. This comprehensive gui...

This article provides a comprehensive overview of designing scalable machine learning architectures, essential for handling large datasets and complex...

Serverless computing promises significant benefits in scalability and agility, but its pay-per-use model necessitates careful cost management. This ar...

This article provides a comprehensive overview of the roles and responsibilities within a Security Operations Center (SOC), crucial for modern cyberse...