
Preparing for Post-Quantum Cryptography: A Practical Guide
Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

This comprehensive guide explores the essential best practices for creating effective API documentation, crucial for developer adoption and success. F...
This comprehensive guide explores the Retry Pattern with Exponential Backoff, a crucial strategy for building resilient and fault-tolerant systems. Fr...
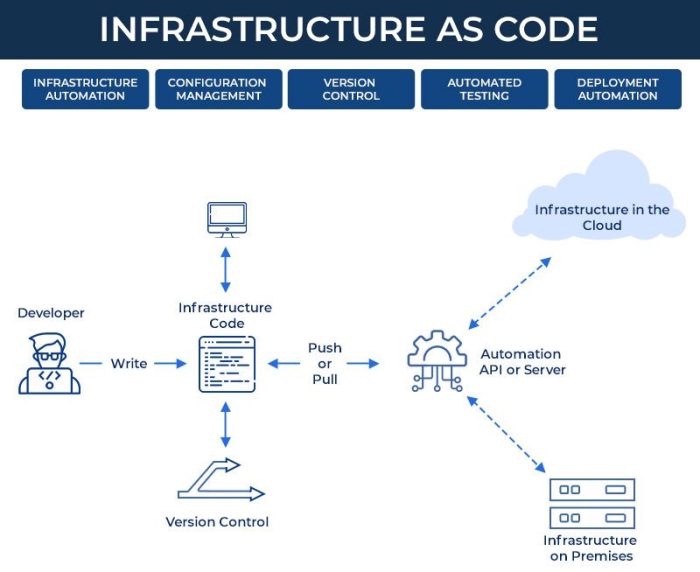
This comprehensive guide explores the power of Infrastructure as Code (IaC) to streamline deployments across various target environments, from cloud p...

This comprehensive guide delves into the crucial role of a Data Engineer within cloud architecture, exploring responsibilities, essential skills, and...
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...

Ensuring business continuity in the cloud hinges on resilient network architecture. This guide provides a detailed overview of the core principles, st...
This comprehensive guide provides a detailed roadmap for optimizing your cloud software licensing costs, covering crucial aspects from understanding v...
Serverless data analytics is revolutionizing data processing through scalable, cost-effective, and agile solutions. This paradigm shift requires strat...

Physical data transfer appliances offer a vital solution for managing large datasets and overcoming network limitations in modern data environments. T...

This article provides a comprehensive overview of Cloud Access Security Brokers (CASBs), outlining their core functions, architecture, and key feature...

This comprehensive guide outlines the critical steps for enforcing mandatory tagging across all resources, ensuring improved organization, compliance,...