
Documenting Cloud Architecture Decisions: Best Practices and Strategies
Cloud architecture decisions are fundamental to an organization's success in the cloud. This article provides a comprehensive guide to effectively doc...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Cloud architecture decisions are fundamental to an organization's success in the cloud. This article provides a comprehensive guide to effectively doc...
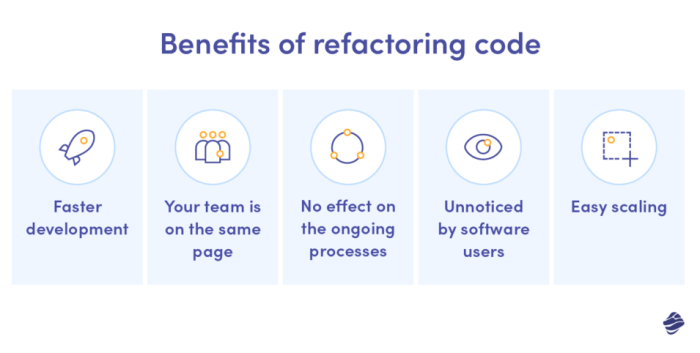
Refactoring code is crucial for long-term software health, allowing developers to improve code structure and maintainability without changing its core...
This comprehensive guide explores the powerful combination of Amazon Kinesis Streams and AWS Lambda, detailing how to build real-time data processing...

Point-in-time recovery (PITR) is a vital data management strategy that allows for the restoration of a database to a specific moment in time, safeguar...

Data migration, while essential for modernizing systems, presents significant compliance challenges. Organizations must navigate complex data privacy...

This article explores the pivotal role of service meshes in securing modern, microservices-based application architectures. It highlights how service...

Navigating a cloud migration requires a robust business continuity plan to mitigate risks and ensure operational resilience. This comprehensive guide...

Edge computing is transforming data processing by minimizing latency and improving response times for real-time applications. By shifting computation...

DevSecOps is revolutionizing software development by integrating security into the CI/CD pipeline, streamlining the process from code creation to depl...

Ensuring a graceful shutdown is critical for maintaining data integrity, preventing user disruption, and facilitating robust application behavior. Thi...

Preparing for a cloud migration requires a thorough pre-migration security and compliance assessment. This crucial step involves a comprehensive evalu...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...