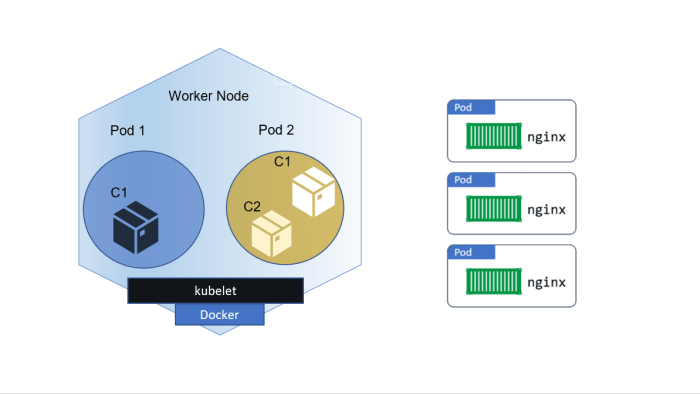
Kubernetes Rightsizing: Optimizing Pod and Node Resources for Efficiency
Kubernetes rightsizing for pods and nodes is a crucial strategy for maximizing resource efficiency and minimizing costs within your Kubernetes deploym...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Kubernetes rightsizing for pods and nodes is a crucial strategy for maximizing resource efficiency and minimizing costs within your Kubernetes deploym...
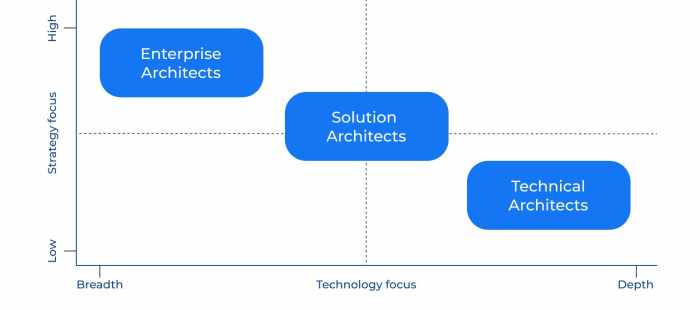
In the complex landscape of cloud migration, the Cloud Solution Architect plays a critical role in translating business needs into a secure and cost-e...
Cloud-native development offers significant advantages for businesses seeking agility, delivering faster deployment cycles, enhanced scalability, and...

Cloud computing's benefits hinge on the reliability of its underlying systems. This guide provides a comprehensive overview of designing robust cloud...

To thrive in a competitive environment, engineering teams must prioritize cost-aware decision-making. This guide provides a comprehensive overview of...

Managing costs in a multi-cloud environment demands a proactive and strategic approach. This article provides a comprehensive guide to understanding c...

This comprehensive guide dives into the world of Jenkinsfiles, exploring their crucial role in automating Continuous Integration and Continuous Delive...

Data masking and tokenization are essential security practices for safeguarding sensitive data while maintaining its usability. This article delves in...

In the ever-evolving cloud environment, safeguarding your digital assets is critical, and Cloud Infrastructure Entitlement Management (CIEM) tools off...
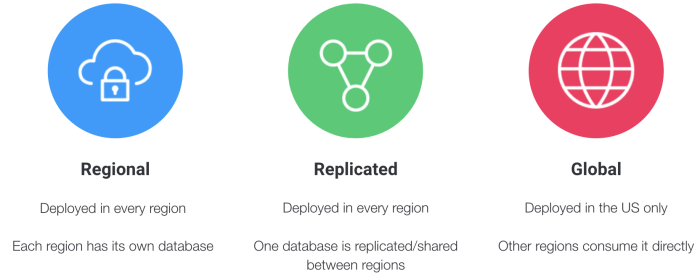
Multi-region architecture, while offering enhanced scalability, availability, and disaster recovery capabilities, demands careful planning for success...

This comprehensive article explores the critical practice of cloud cost anomaly detection, providing a detailed overview of its definition, benefits,...
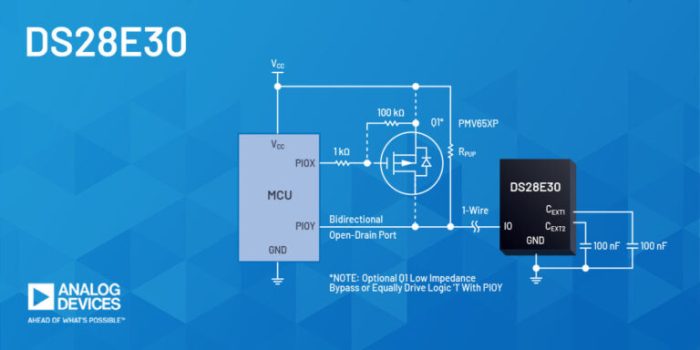
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...