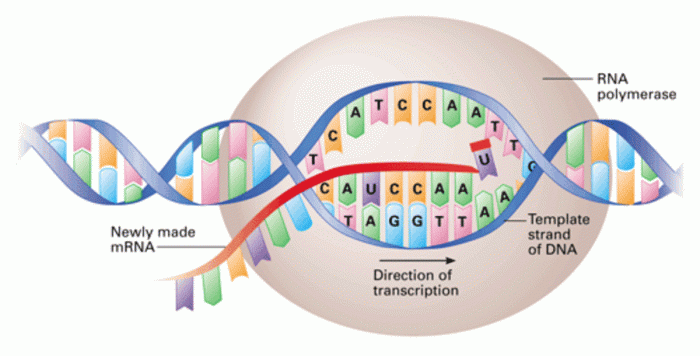
Achieving High Availability for Critical Applications: A Comprehensive Guide
Ensuring continuous operation of critical applications is vital in today's digital landscape. This article explores the essential strategies, architec...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Ensuring continuous operation of critical applications is vital in today's digital landscape. This article explores the essential strategies, architec...
This article provides a comprehensive overview of serverless Step Functions, detailing their core components, benefits, and practical applications in...

Serverless computing offers significant benefits, but its cost management requires a specialized approach. This article explores the unique challenges...
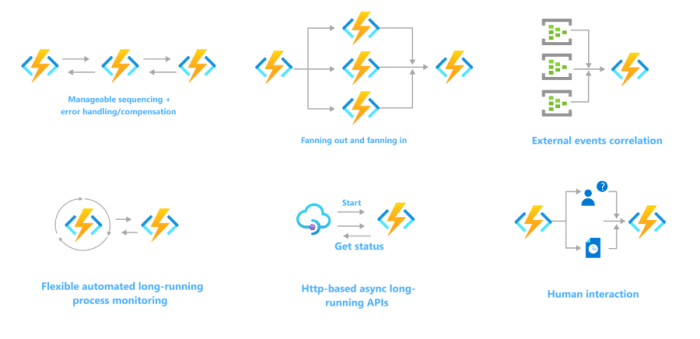
This article delves into the critical role of API composition within serverless architectures, exploring how to effectively build, manage, and optimiz...

Navigating the complexities of PCI DSS compliance is crucial for any business handling cardholder data. This comprehensive guide provides a detailed r...

Serverless computing is revolutionizing software development by transferring operational burdens to cloud providers, enabling event-driven architectur...

This comprehensive article delves into Runtime Application Self-Protection (RASP), exploring its fundamental concepts, architecture, and operational m...

Navigating cloud service level agreements (SLAs) is paramount for successful cloud adoption. This guide offers a structured approach to evaluating pro...

This article provides a comprehensive overview of Amazon Aurora Serverless, exploring its core concepts, architecture, and benefits for database manag...
Securing remote access to cloud environments is paramount in today's interconnected landscape, yet presents significant security challenges. This guid...

This guide provides a comprehensive approach to identifying and managing untagged resources in your cloud environment. By understanding the process of...

A security baseline serves as the foundation for robust cybersecurity, providing a standardized configuration for systems and applications to ensure a...