
Key Management Service (KMS): Definition, Benefits, and Best Practices
In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

In today's data-driven world, protecting sensitive information is critical, and Key Management Services (KMS) are essential for achieving this. This a...
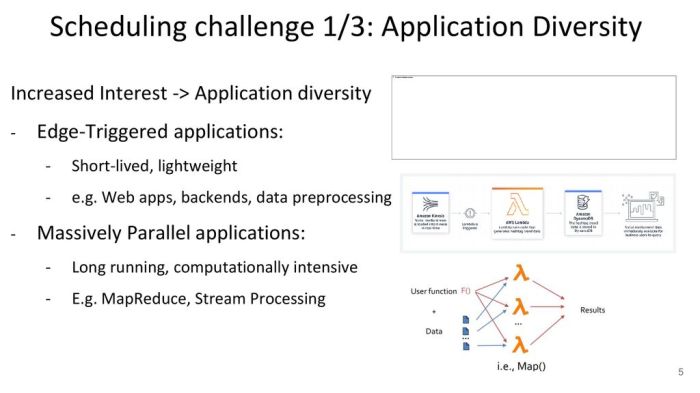
Serverless computing offers a transformative approach to software development, enabling developers to concentrate on code rather than infrastructure m...
Migrating applications demands a robust approach, and User Acceptance Testing (UAT) is a crucial step in ensuring a successful transition. UAT validat...
This comprehensive guide provides a deep dive into automating rollback procedures to mitigate the impact of failures in your deployments. From definin...
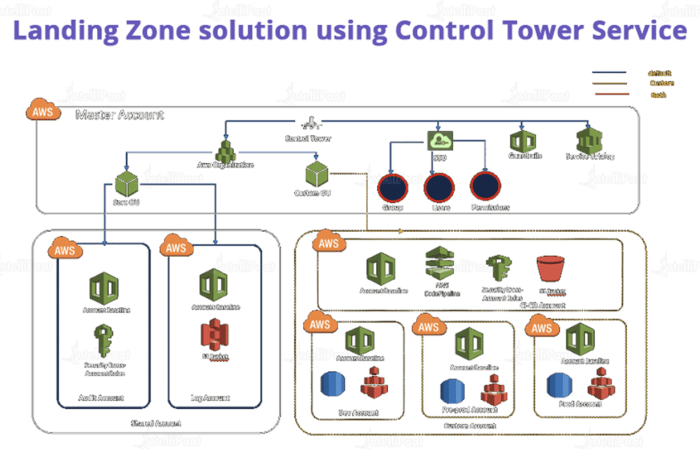
Building a secure and compliant cloud environment is crucial, and this article provides a comprehensive guide to designing a robust landing zone. Fro...

Before undertaking a system migration, establishing a robust performance baseline is crucial for success. This article provides a comprehensive guide...

This comprehensive guide details the process of analyzing the costs associated with a specific workload, from defining its scope and identifying key c...

This comprehensive guide dives deep into the art of crafting efficient and secure Dockerfiles, covering crucial aspects from base image selection and...

Migration projects often face resistance to change, stemming from psychological factors and concerns about the unknown. To ensure a successful transit...

This article provides a comprehensive overview of service meshes, elucidating their core functionalities, role in microservices architecture, and bene...

Managing session state effectively is paramount for building scalable and reliable distributed applications. This involves tracking user data across m...

Understanding the Principle of Least Privilege (PoLP) is crucial for securing your AWS Lambda functions. This principle emphasizes granting only the m...