
Containerizing Legacy Applications: A Practical Guide
Containerizing legacy applications, with their inherent complexities and technical debt, requires a strategic approach. This process begins with under...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

Containerizing legacy applications, with their inherent complexities and technical debt, requires a strategic approach. This process begins with under...
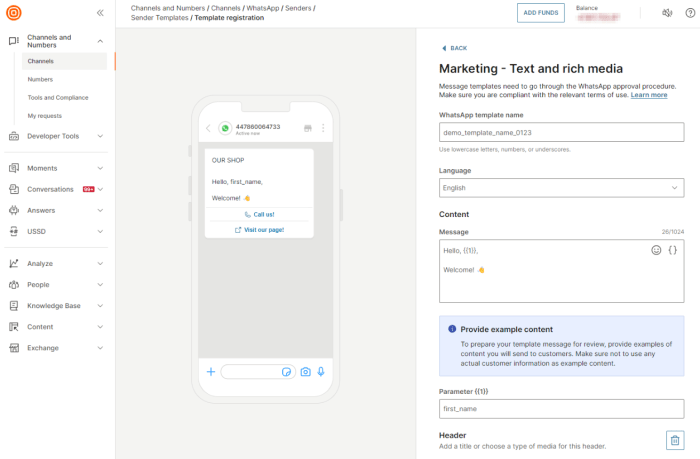
This article outlines a comprehensive strategy for designing a secure cloud landing zone, a critical foundation for any organization adopting cloud se...
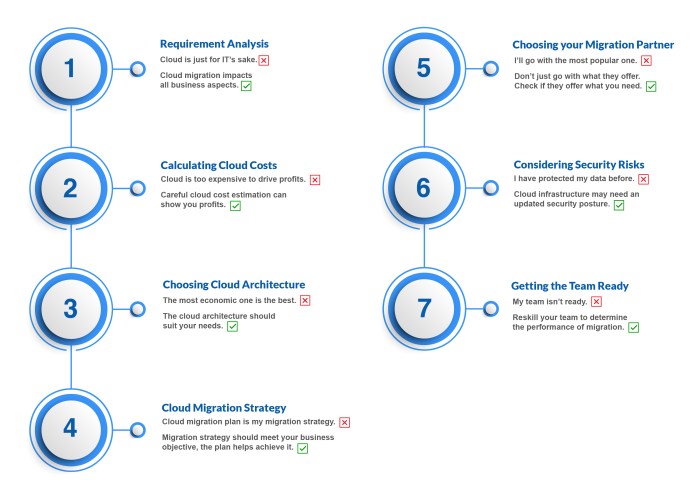
A cloud migration assessment report is a crucial document for organizations considering a move to the cloud, providing a comprehensive roadmap for a s...

Choosing between managed databases and self-hosted solutions is a critical decision impacting operational efficiency, cost, and adaptability for any o...
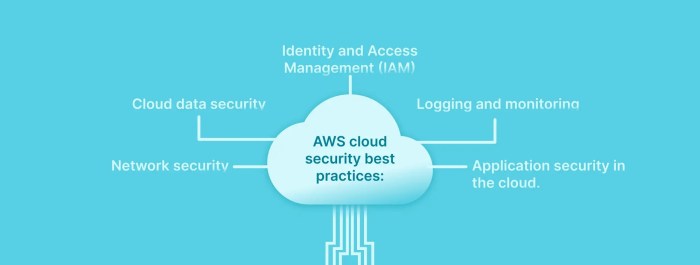
Embarking on a cloud migration requires a robust security strategy to protect your data and infrastructure. This comprehensive guide outlines essentia...
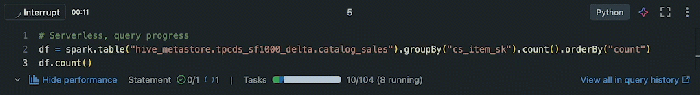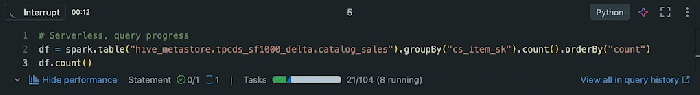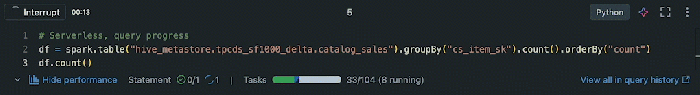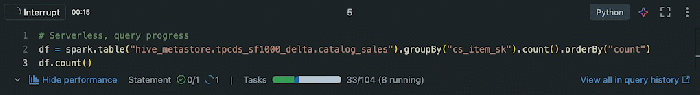
Serverless architectures offer significant advantages, but integrating databases introduces distinct complexities. This article examines the key chall...

This article explores the critical role of automation in modern migration factories, detailing how it streamlines complex processes. From automated da...
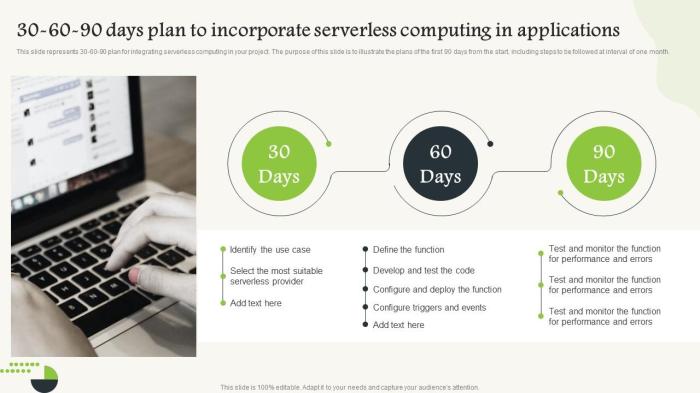
Serverless computing revolutionizes application development by abstracting away infrastructure management, but it introduces execution time limits tha...

The "Latency is Zero" fallacy, a dangerous misconception in architectural design, can lead to significant performance bottlenecks and system instabili...
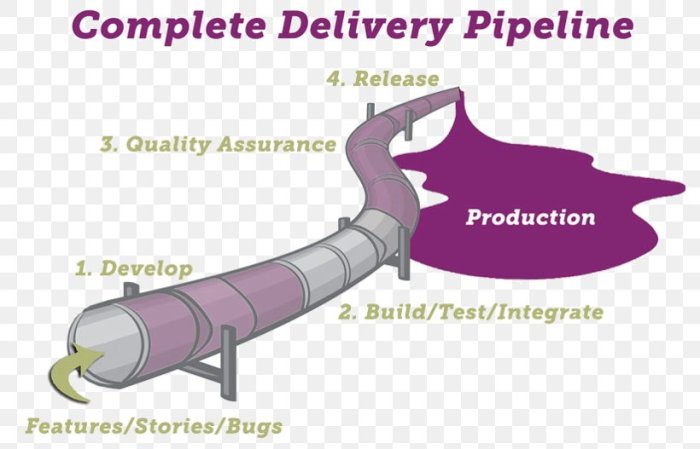
This comprehensive guide explores the transformative power of Continuous Delivery (CD) in automating application deployment, highlighting its core pri...

Navigating the complexities of chargebacks is crucial for any business accepting online payments. This comprehensive guide provides a detailed overvie...
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...