
Managing Large Lambda Deployment Packages: Layers as the Solution
Facing Lambda deployment size limitations and slow cold starts? This comprehensive guide explores how to effectively manage large deployment packages...
161 posts in this category

Facing Lambda deployment size limitations and slow cold starts? This comprehensive guide explores how to effectively manage large deployment packages...

This article delves into the world of serverless stream processing, exploring its core components, benefits, and real-world applications. Readers wil...
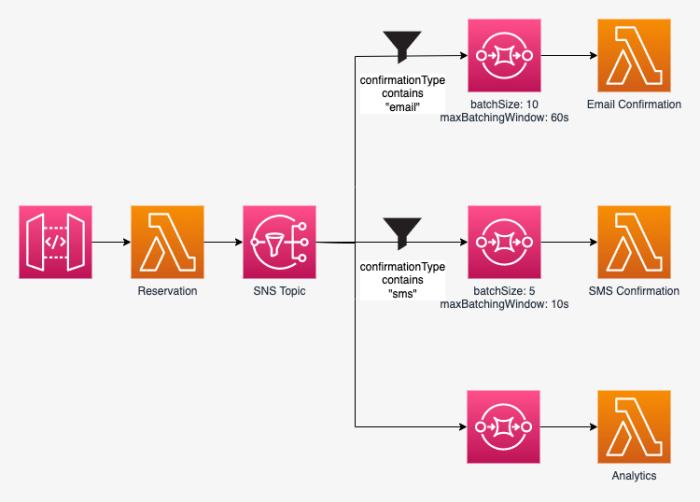
This article provides a comprehensive guide to leveraging Amazon SNS for efficient message fan-out to AWS Lambda functions. Readers will learn how to...

Effectively managing dependencies is crucial for building robust and performant AWS Lambda functions. This comprehensive guide explores various strate...
To ensure high availability and performance, designing a scalable DynamoDB table is crucial for modern applications. This article provides a comprehen...

This article delves into the transformative impact of serverless computing on DevOps culture, exploring how it reshapes collaboration, deployment proc...
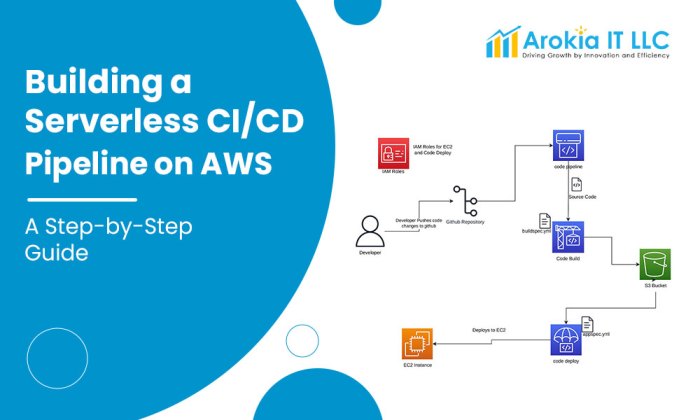
This article delves into the innovative world of serverless CI/CD pipelines, exploring their core concepts, component breakdown, and significant advan...

Serverless computing's impact on software development has created a thriving open-source ecosystem, presenting exciting avenues for developers to cont...
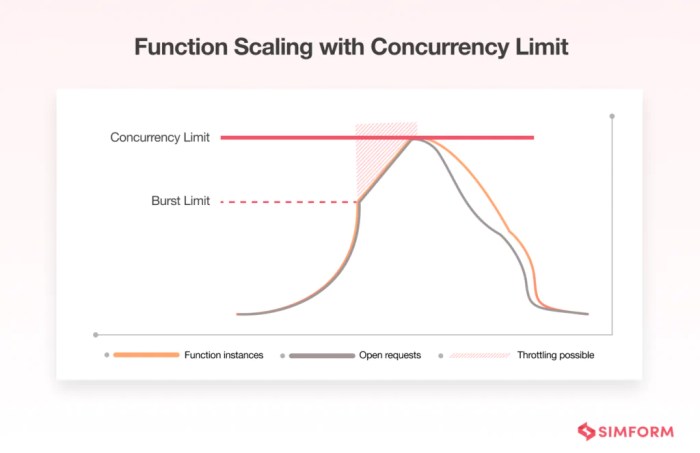
Serverless architectures boast impressive scalability, but require careful management of concurrency to optimize performance and resource utilization....
This comprehensive guide offers a deep dive into the vast ecosystem of community resources available to serverless developers, from online forums and...

Serverless applications, despite their scalability benefits, require robust strategies for managing sensitive data like API keys and database credenti...
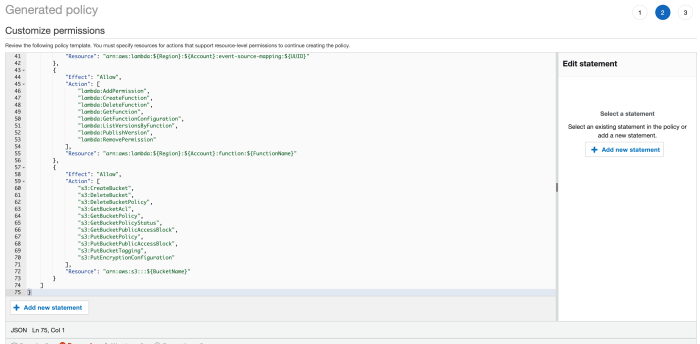
This comprehensive guide provides a deep dive into serverless security, covering critical aspects from authentication and authorization to incident re...