Preventing Cross-Site Scripting (XSS) Attacks: A Comprehensive Guide
This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...
152 posts in this category

This article provides a comprehensive guide to preventing Cross-Site Scripting (XSS) attacks, detailing the fundamental concepts, various attack types...

Handling Data Subject Access Requests (DSARs) is a critical component of GDPR compliance. This comprehensive guide offers a clear and detailed roadmap...
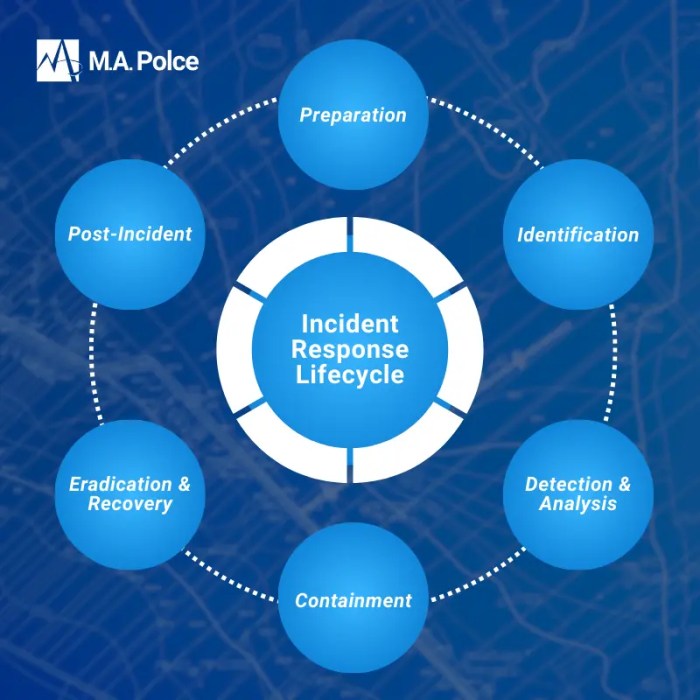
In the face of ever-evolving cyber threats, tabletop exercises are vital for strengthening an organization's incident response capabilities. These dyn...
Managing resources across multiple cloud providers like AWS, Azure, and GCP introduces complex challenges for consistent security and access control d...
In the face of ever-evolving digital threats, organizations need efficient and proactive security solutions. Automated security remediation offers a p...

This article provides a comprehensive guide to preventing SQL injection attacks specifically within cloud application environments. It covers critical...
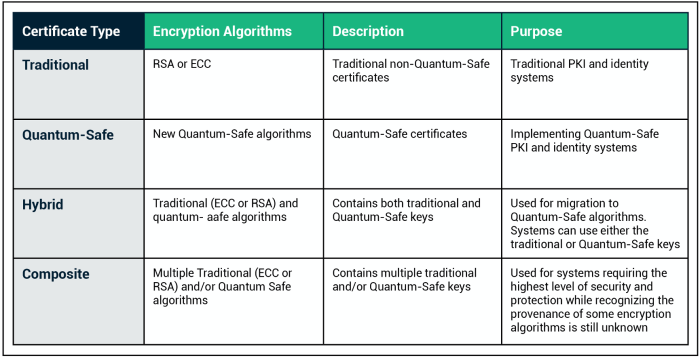
Explore the groundbreaking field of quantum cryptography and its revolutionary impact on cybersecurity in this comprehensive article. From fundamental...

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...

This article provides a comprehensive overview of Static Application Security Testing (SAST), exploring its core principles, role within the Software...
In the world of interconnected microservices, secure service-to-service communication is critical. Mutual Transport Layer Security (mTLS) provides a p...

This comprehensive guide provides a detailed overview of securing the Kubernetes control plane, covering essential aspects from authentication and aut...
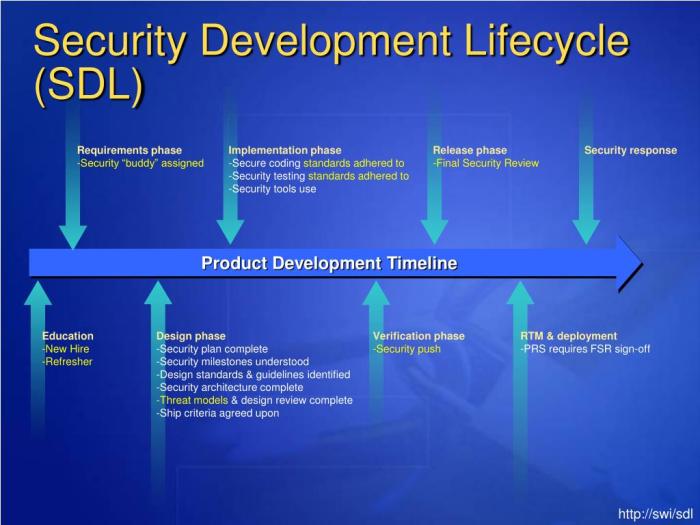
"Shifting security left" is a critical strategy for modern software development, emphasizing the integration of security practices early in the develo...