
Building a Cloud Security Operations Center (SOC): A Comprehensive Guide
This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...
152 posts in this category

This comprehensive guide provides a roadmap for building a robust Security Operations Center (SOC) specifically designed for the cloud environment. Fr...

Prepare for the future of cybersecurity with a comprehensive guide to Post-Quantum Cryptography (PQC). This article delves into the fundamental concep...

This article provides an introduction to threat modeling using the STRIDE methodology, a critical practice for enhancing software security. Learn how...
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...

Safeguarding your digital assets requires vigilant monitoring for unauthorized file changes. This article explores the critical importance of detectin...

This article provides a comprehensive overview of Data Privacy Impact Assessments (DPIAs), essential tools for protecting personal information in the...
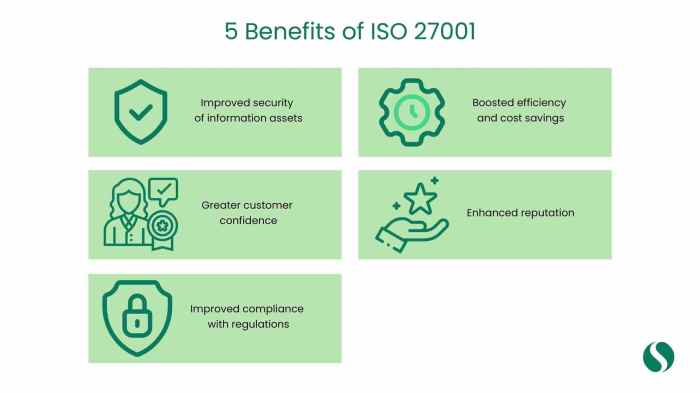
This comprehensive guide provides a detailed roadmap for achieving ISO 27001 certification, covering everything from understanding the core principles...
Artificial intelligence is rapidly transforming the cybersecurity landscape, offering powerful new tools for threat detection, incident response, and...
Managing security across a multi-cloud environment requires a strategic approach to avoid fragmentation and ensure consistent protection. This guide o...

This article provides a comprehensive overview of User and Entity Behavior Analytics (UEBA), exploring its core concepts, components, and practical ap...

Protect your organization from the potential pitfalls of cloud service provider failures with a robust third-party vendor risk assessment program. Thi...

Kubernetes Pod Security Policies (PSPs) are crucial for bolstering the security of your containerized applications within a Kubernetes cluster. These...