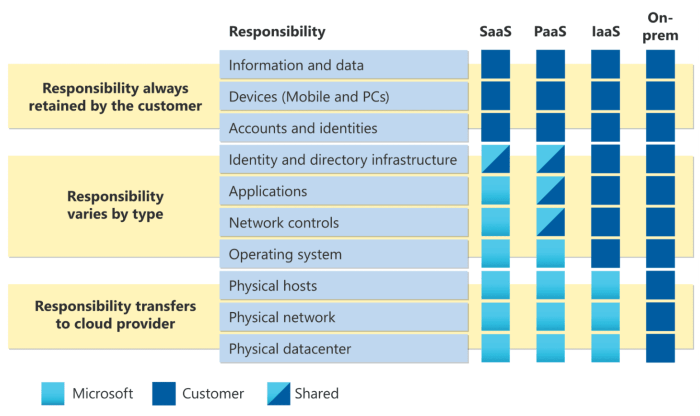
Securing Data in Use: A Guide to Secure Enclaves
This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...
152 posts in this category

This article explores the critical need to protect "data in use," delving into the inherent security risks and challenges associated with active compu...

In today's digital world, the Chief Information Security Officer (CISO) is a vital strategic leader, tasked with protecting an organization's data and...

This comprehensive guide provides a detailed overview of FedRAMP, the critical security authorization program for cloud services used by the U.S. gove...
Facing an increasingly complex cyber threat landscape, security operations teams need efficient solutions. This article explores how Security Orchestr...

Digital Rights Management (DRM) is a critical component of the digital landscape, serving to protect intellectual property in the realm of content cre...

This comprehensive guide delves into the critical role of Cloud Workload Protection Platforms (CWPP) in modern cloud security, exploring its core conc...

Enhance your cybersecurity strategy by learning how to set up a honeypot, a valuable tool designed to attract and analyze potential attackers. This gu...

This article delves into the critical practice of Continuous Compliance Monitoring (CCM) in cloud environments, explaining its core concepts and showc...
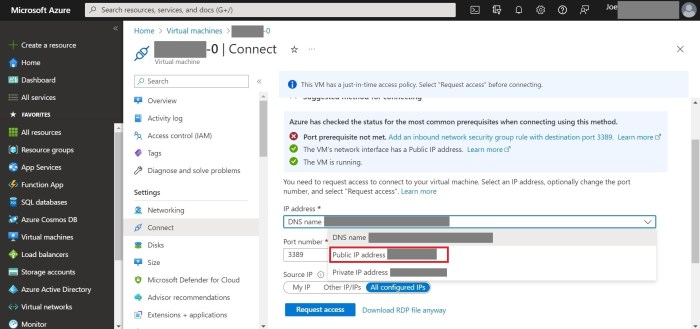
This article delves into the critical concept of Just-in-Time (JIT) access for cloud resources, exploring its core principles and the significant secu...
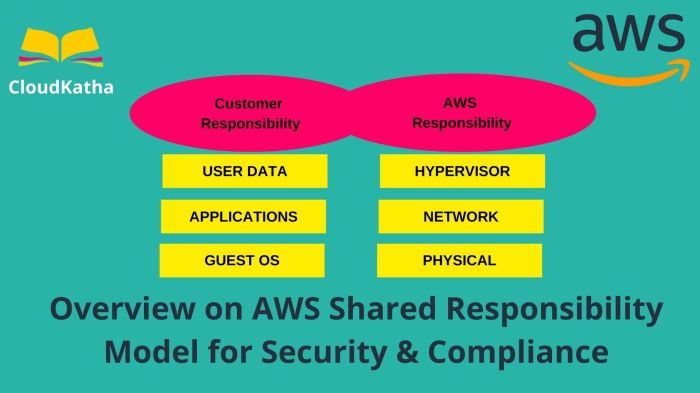
The shared responsibility model is a critical framework in cloud security, outlining the security obligations of both the cloud provider and the custo...

This article provides a comprehensive overview of cloud-native security services, exploring their core concepts, key components, and numerous benefits...

The NIST Cybersecurity Framework is a widely adopted, voluntary standard designed to help organizations proactively manage and reduce cybersecurity ri...