
Cloud Security Forensics: A Step-by-Step Guide
Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...
152 posts in this category

Cloud environments present unique challenges for security forensics, but understanding the core principles is crucial for effective investigation. Thi...
Protecting your organization from internal cybersecurity risks is paramount. This guide, "How to Detect and Respond to Insider Threats," offers a comp...

In today's evolving digital landscape, cloud security certifications are crucial for professionals seeking to validate their expertise and advance the...

This article provides a comprehensive guide to managing secrets and encryption keys in the cloud, a critical aspect of cloud security. It explores fun...
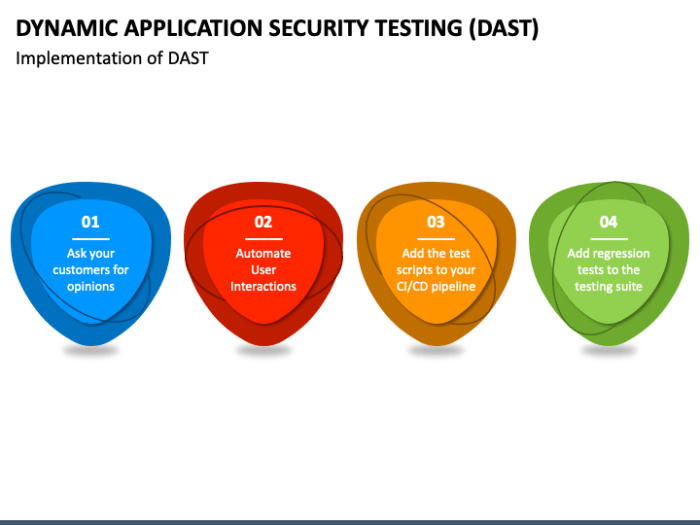
This comprehensive guide explores Dynamic Application Security Testing (DAST), providing a deep dive into its core concepts, functionality, and practi...
The proliferation of Internet of Things (IoT) devices necessitates robust security measures to protect against increasingly sophisticated cyber threat...
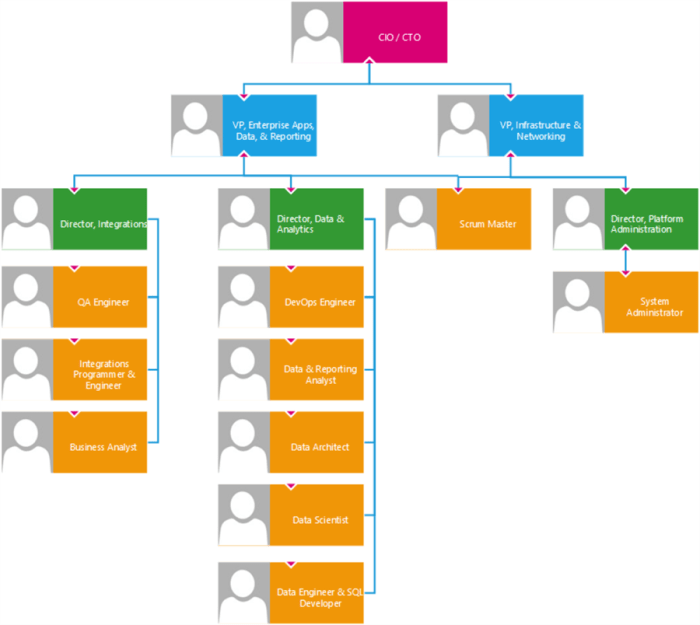
Cloud computing's scalability demands stringent security measures, making clear role and responsibility definitions for cloud access paramount. This a...
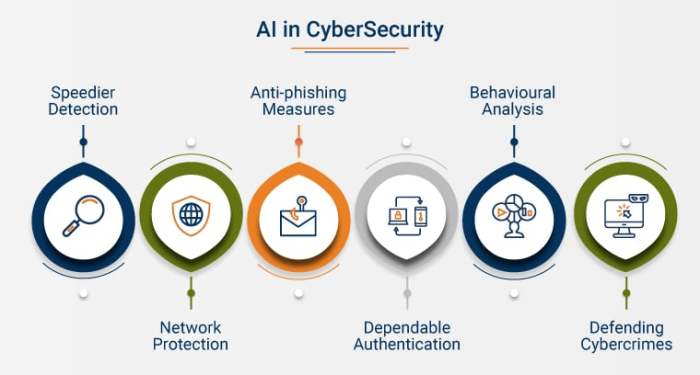
This article explores the vital integration of threat intelligence into cloud security operations, a crucial step in defending against modern cyber th...

This article provides a comprehensive overview of security maturity models, essential frameworks for enhancing an organization's cybersecurity posture...

This comprehensive guide explores the critical importance of securing your software dependencies, outlining potential risks from supply chain attacks...

In today's complex regulatory environment, establishing a robust data retention policy is crucial for compliance and minimizing potential risks. This...

This article delves into the critical security challenges inherent in serverless computing, covering everything from authentication and authorization...