
SOC 2 Compliance in the Cloud: A Comprehensive Guide
Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...
152 posts in this category

Navigating SOC 2 compliance in a cloud environment requires a strategic approach, and this article provides a comprehensive guide. It covers essential...

Organizations face increasing cyber threats, making robust security awareness training for employees crucial. This comprehensive guide provides a step...
User Lifecycle Management (ULM) and provisioning are crucial for security, operational efficiency, and compliance within any organization. This guide...

Managing third-party contractor access is a crucial element of robust cybersecurity. This guide outlines essential strategies for securely granting ac...
In today's cloud-centric world, understanding Data Loss Prevention (DLP) solutions is critical for safeguarding sensitive information. This article pr...

A Business Continuity Plan (BCP) is essential for any organization seeking to minimize disruption and maintain operational resilience in the face of u...
In the face of escalating cyber threats, protecting web applications is more critical than ever. This article delves into the essential function of We...

Organizations leveraging multi-cloud environments face a complex landscape of security risks, including data breaches, identity and access management...

This comprehensive article explores the evolving landscape of cloud security, addressing current threats and vulnerabilities while examining the impac...
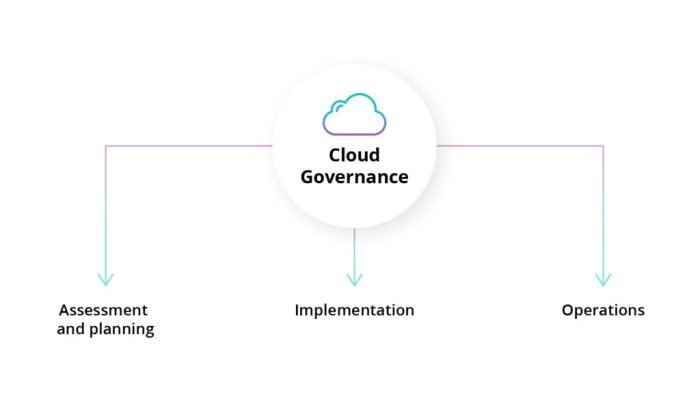
Establishing a formal cloud security governance framework is crucial for protecting valuable assets and maintaining compliance in the cloud. This fram...

In the modern cloud-centric business environment, robust data and infrastructure security is critical. Security Information and Event Management (SIEM...

Discover insights and practical tips in this comprehensive guide about What Are The Compliance Requirements For Data Breach Notifications.