
File Integrity Monitoring (FIM): Definition, Benefits, and Implementation
In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...
152 posts in this category

In the ever-evolving digital world, File Integrity Monitoring (FIM) serves as a crucial security layer, vigilantly protecting your data and systems fr...
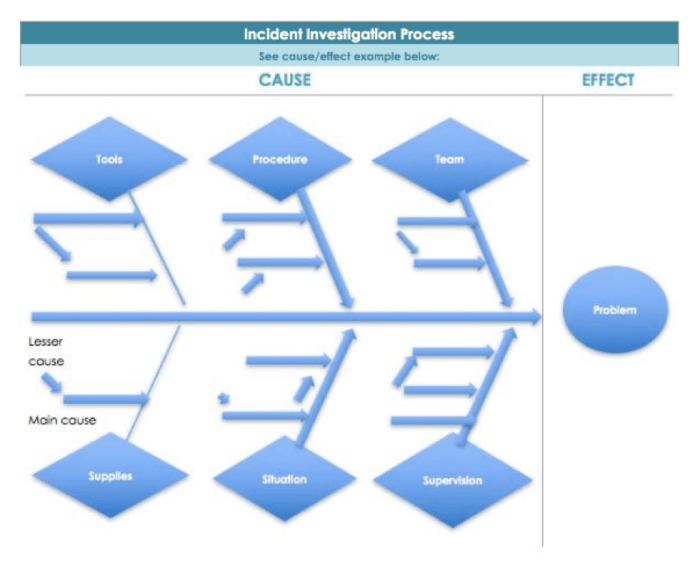
This article provides a comprehensive guide to performing a Root Cause Analysis (RCA) following a security incident, a crucial skill in today's digita...

Data security is crucial for modern businesses, highlighting the need for effective backup and disaster recovery (BDR) strategies. This guide provides...

This article delves into the intricacies of identity federation, explaining its core concepts, components, and the benefits it offers for streamlined...

This article delves into the critical process of de-provisioning user accounts, explaining its definition, triggers, and the vital role it plays in bo...

This article provides a comprehensive overview of Software Bill of Materials (SBOMs), explaining their definition, purpose, and benefits for various s...

The cloud offers significant advantages, but it also presents new vulnerabilities to malware and ransomware attacks. This article outlines essential s...

This article delves into the intricacies of legal hold and eDiscovery, focusing on the significant advantages of leveraging cloud technology for these...

Protecting sensitive data within big data platforms demands a comprehensive approach encompassing encryption, access control, data governance, and rob...
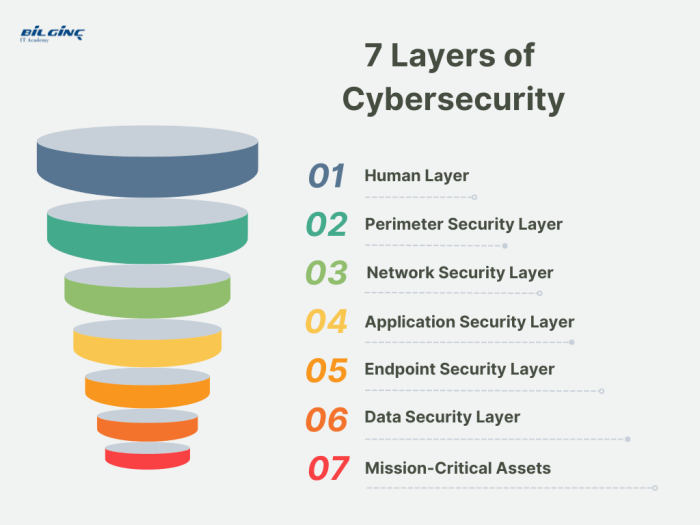
Defense in depth is a critical cybersecurity principle that emphasizes a layered approach to security, acknowledging that no single measure is impenet...
In an increasingly cloud-dependent business environment, establishing a strong cloud security team is crucial for protecting valuable data and applica...
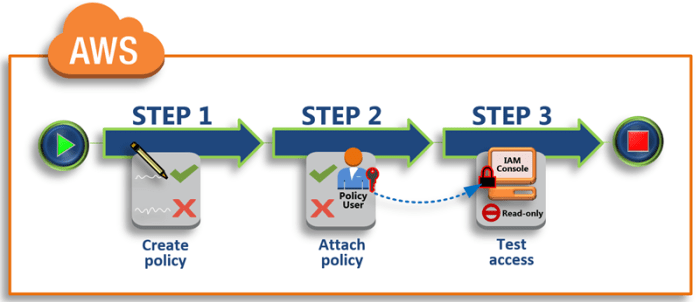
This comprehensive guide delves into the world of Identity and Access Management (IAM) policies, explaining their crucial role in securing access to y...